- Experts warned that AI-written fishing email polish and bypass traditional email filters
- Polymorphic attacks continuously shift to detect in real time
- Professional Email Agreement Scams now copy the authorities with closely formatting
We have said it earlier, and we will say it again. Artificial Intelligence Cybercrime’s face is changing, and Fishing is an area where it is the most difficult.
The new data of the security firm Coffs has warned that the AI-managed phishing campaign is not only more frequent, but also more confident than ever.
These email cleaner, more polished, are sewn to fooling even more alert users, and are now accessible to anyone with a generative AI tool now, almost even accessible to anyone, the danger actor is scaling his operations at a rate that many businesses can not simply keep.
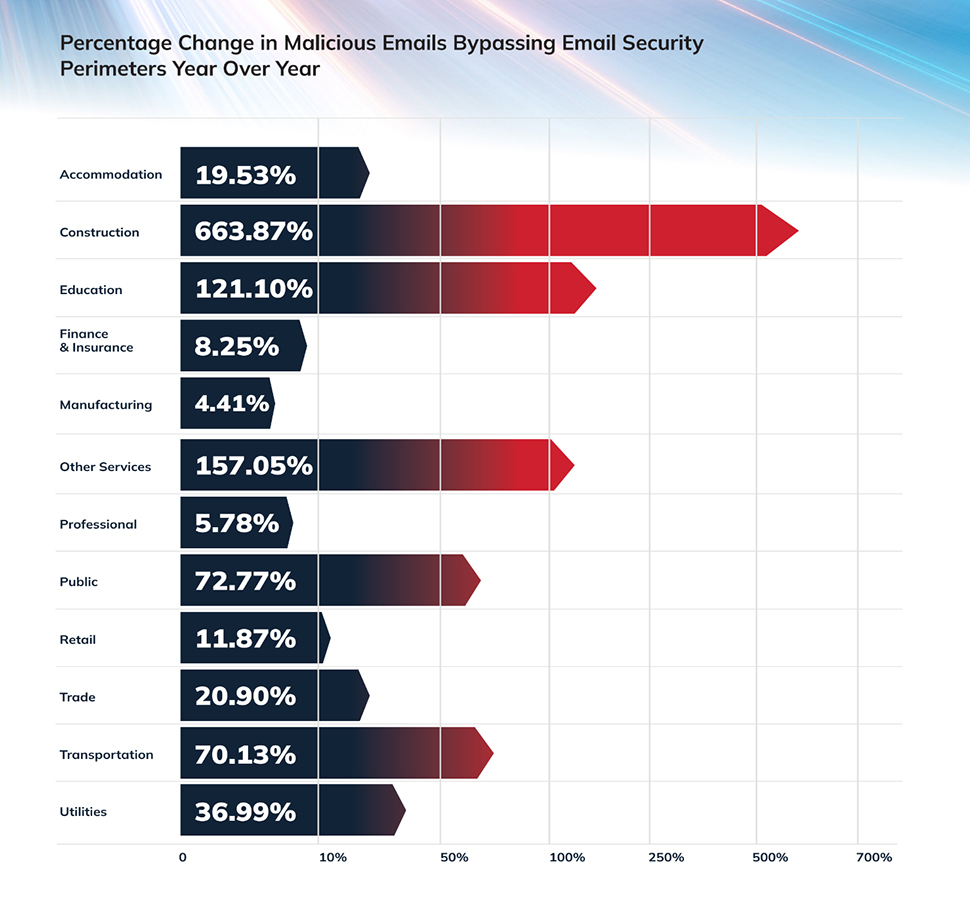
Over -development system
In its latest danger intelligence report, Rise of AI – A new era of fishing dangersCoffene Description How Fishing Strategy is developing at an unprecedented rate.
In 2024, the Coffs Fishing Defense Center detected a malicious email every 42 seconds, many of which slipped through heritage circumference.
Email-based scams jumped 70% year-on-year, fuel from the ability to mimic the tone of AI, spoil the internal email and personalize messages with impressive accuracy.
The message is now the right grammar, accurate formatting and realistic sender addresses. They often apply C-suits authorities, respond within existing email threads, and use looklike domains such as “@Consultant.com”.
This change towards the Trade Email Agreement (BEC) has become a major threat. The AI-related material lacks teltel signals, which first removes fisherrs, such as typos, spelling mistakes and strange phrases, often clues that suggest that English sender may not be the first language of the sender.
According to Coffs, polymorphic fishing campaign is another area of concern. These continuously modify their content in real time to avoid signing-based safety devices. Subject lines, sender details, and text shift all dynamically, which detects all but impossible with traditional filters.
Emails have also developed embedded malware, the coffene report, 2024 have new observation threats with more than 40% samples, many of them are remote access trozons (mice).
How to be safe

Carefully check the email material: Doubt the emails associated with financial activities, immediate requests, or out-off-place language, even if the formatting looks correct.
Verify internal requests: If someone claims to be from an email colleague or executive, double-check using the contact methods known before taking action.
Do not rely on appearance: AI-borne emails often look innocent, so focus on reference, time and material rather than “professional” appearance.
Avoid clicking on the link without verification: To check your destination, hover the link and avoid downloading files from unfamiliar or unexpected messages.
Use safety devices beyond the perimeter: Look for solutions that provide delivery analysis and danger response based on behavior, not only signature.


