The decentralized exchange CETUS protocol announced that hackers stole $ 223 million in cryptocurrency and are offering a deal to stop all legal action if the funds are returned.
The project also announced a $ 5 million bounty to anyone providing relevant information for the identity and arrest of the attacker.
The Cetus Protocol is a decentralized exchange (DEX) and liquidity protocol working on SUI and APTOS blockchain.
It appoints a concentrated liquidity market manufacturer (CLMM) model, allowing liquidity providers to allocate property within specific value limits, increase capital efficiency and enable advanced trading strategies.
The total trading volume in the CETUS protocol is $ 57 billion (until May 2025), with more than 15 million accounts execut 144 million trades on platforms.
This incident took place yesterday, initially inspired the Cetus Protocol Stop its smart contract For investigation.
A few hours later, the project confirmed the theft and “the $ 162M of the compromised funds has been successfully prevented.”
In a later statement, the Cetus Protocol announced that the hacker had exploited a weak package, but no details have been revealed.
“We identified the root cause of exploitation and fixed the respective package, and informed the builders of the ecosystem as fast as we can with the help of members of the ecosystem to prevent other teams from being affected,” Alleged seat -protocol,
Additionally, the platform mentioned that it identified the attacker’s atherium wallet addresses and accounts, and is working with third party to detect and freeze funds. Law enforcement has also been informed.
The CETUS protocol also offered the hacker “a time-sensitive WhiteHat Settlement”, if the legal action was promised not to carry out the money when the funds were refunded. To put more pressure on the attacker, the project announced a bounty of $ 5 million for identification and information for the arrest of the hacker.
Meanwhile, a significant $ 162 million on the SUI blockchain was stopped after an emergency vote by the verifications.
Blockchain analytics company Published a report Depending on its visibility of the event, the automatic market maker (AMM) enables flash loan-style attacks, probably indicating a defect in logic, to include manipulation in the pool value.
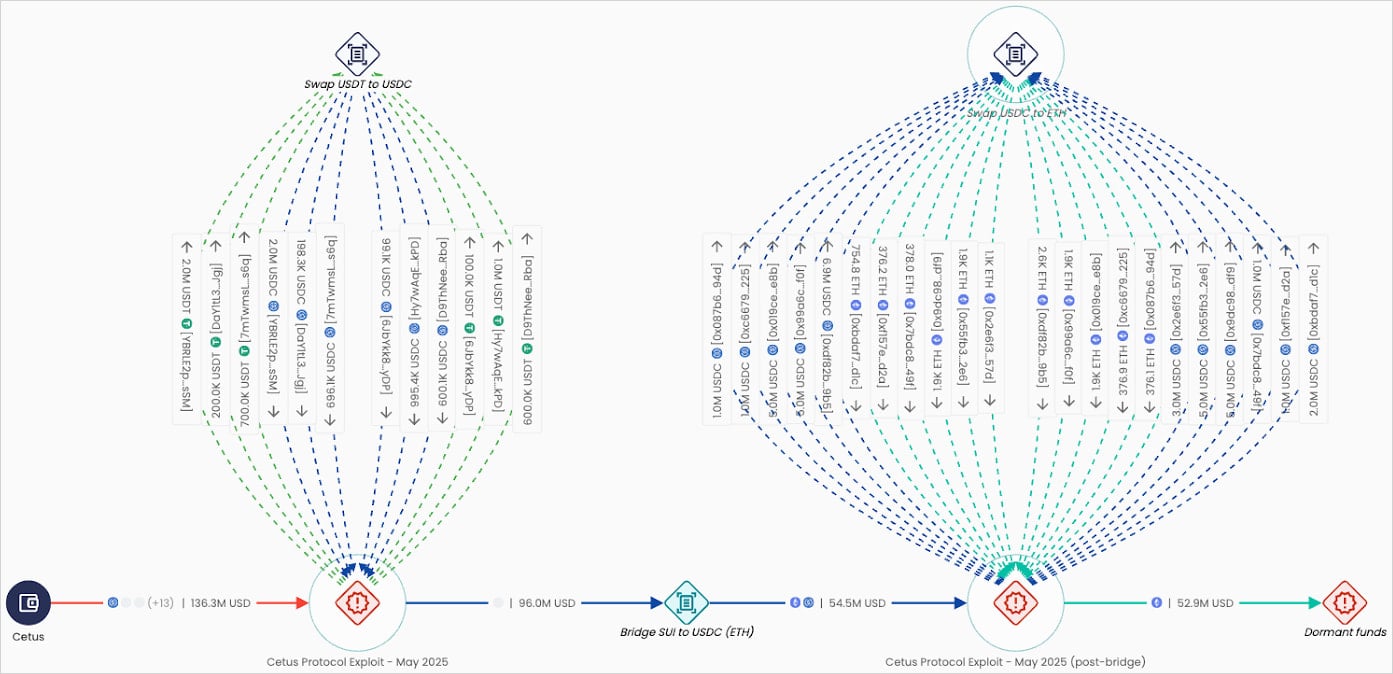
The blockchain intelligence firm also offers an observation of the attacker’s efforts for the fund movement, which includes swaps from USDT to USDC and cross-chain movement from suits to the atherium.
Source: Eggs
Illiptic is actively detecting transactions from initial exploitation on the needle, which is up to the attacker’s wallets on the atherium, and the hacker’s address is flagged off on all major exchanges and virtual asset service providers, which prevents laundering or transfer efforts.



.png)