
Anubis Ransomware-AS-A-Service (RAS) operation has added a wiper module to its file-econstimge malware that destroys targeted files, yet makes recovery impossible even after paying ransom.
Anubis (the same name with a ransomware module not to be confused with Android Malware) is a relatively new RAAS that was first seen in December 2024, but became more active at the beginning of the year.
On 23 February, the operators announced an affiliated program on the ramp forum.
A Banana report At that time it was explained that Anubis introduced 80% of his income to ransomware colleagues. Data extortion affiliation was offered 60%, and initial access brokers were offered a deduction of 50%.
Currently, the forced recovery of anubis on the dark web lists only eight victims, indicating that this can increase the amount of attack after strengthening confidence in the technical aspect.
On that front, a trend micro report published yesterday involves evidence that the operators of the option are actively working on adding new features, an unusual a file-wipe function.
Researchers found the wiper into the latest veil samples, and believe that this feature was introduced to pay quickly instead of early paying to increase the pressure on the victim or to make a quick payment to ignore them completely.
“What further separates Annabis from other RAAS and lends an edge for its operation, it is the use of a file wiping facility, which is designed to break the recovery efforts even after encryption,” Trend Micro explains,
“This devastating tendency puts pressure on victims and already enhances the bet of harmful attacks.”
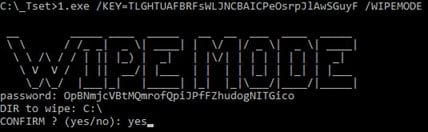
The disastrous behavior is activated using the command-line parameter ‘/vipmod’, which requires key-based authentication to release.
Source: Trend Micro
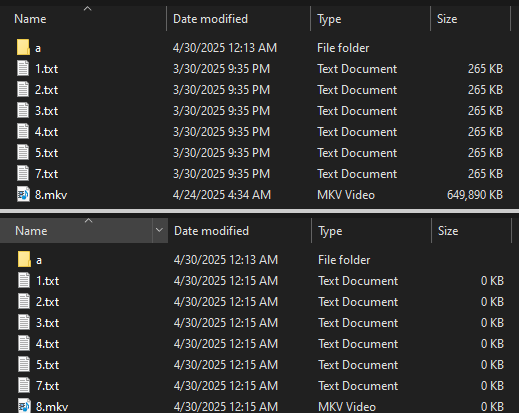
When active, the viper erases all file materials, reducing its size to 0 KB by retaining the file name and structure.
The victim will still look at all the files in the required directors, but their content will be uninterrupted, which will make recovery impossible.
Source: Trend Micro
Analysis of trend micro suggests that Anubis launches supports several commands, including the target path for privilege height, directory exclusion and encryption.
Important systems and program directors are excluded in default form to avoid submitting a fully unusable system.
The ransomware removes volume shade copies and eliminates procedures and services that can interfere with the encryption process.
The encryption system uses ECIES (elliptical curve integrated encryption scheme), and researchers noted implementation similarities for evilbate and prince ransomware.
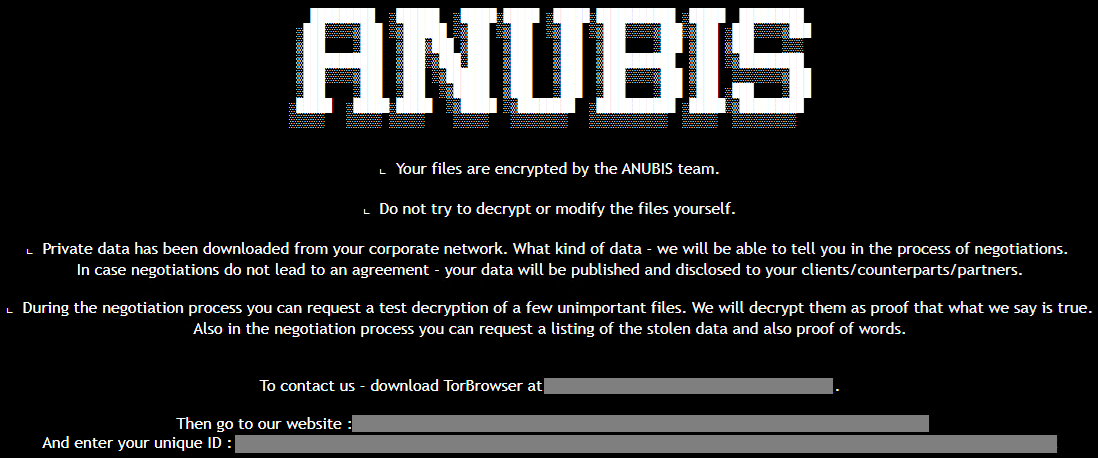
Encrypt files are added to the ‘.anubis’ extension, an HTML ransom note is dropped on the affected directions, and also makes an effort (failed) to replace the malware desktop wallpaper.
Source: Trend Micro
Trend Micro noticed that the attacks of Aubis begins with the fishing email that carry malicious links or attachments.
There is a complete list of indicators of the agreement related to the optional attacks (IOCs) Available here,



