
The news of the “mother of all violations” today broke the news, which sparks widespread media coverage filled with warnings and fear. However, it appears to be a compilation of pre -stolen leaked credentials by infosellers, exposed in data violations, and through credential stuffing attacks.
To be clear, it is not a new data breech, or at all violations, and the websites involved were not recently compromised to steal these credentials.
Instead, these stolen credentials were broadcast for some time, if not for years. This was then collected by a cyber security firm, researchers, or danger actors and returned to a database that was exposed on the Internet.
Cybenuse, which Discovered In short exposed collection, it was said that it was stored in a format that was usually associated with Infostealer Malware, although he did not share samples
There is an infostealer malware that attempts to steal credentials, cryptocurrency wallets and other data from an infected device. Over the years, infostealers have become a major problem, causing violations worldwide.
This type of malware affects both Windows and Mac, and when executed, all will collect credentials, which can find stored on a device and are called “logs”.
An infostealer log is typically a collection that contains several text files and other stolen data. Text files have a list of credentials stolen from browsers, files and other applications.
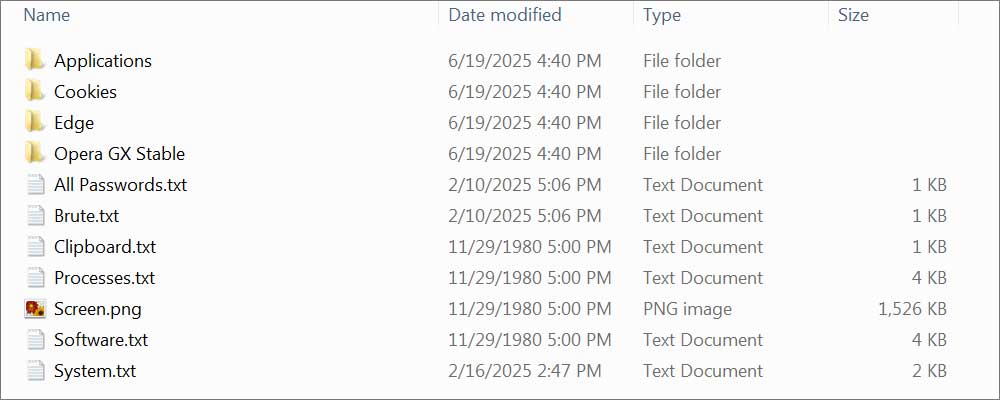
Source: Bleepingcomputer
The credibility of theft is usually saved per row in the following format:
URL: User Name: Password
Sometimes, the border between each component turns into a altarm, semi -weram, or dash.
For example, the following is how to save the stolen credentials in logs from an infostealer device:
If a person is infected with an infostealer and a thousand credit is saved in his browser, Infostealer will steal all of them and store them in the log. These logs are then uploaded to a danger actor, where credentials can be used for further attacks or sold on cybercrime marketplace.
The problem of infostealer has become so bad and widespread that the compromise has become one of the most common methods for the actors of danger for credibility.
We have a webinar next month titled “Stolen Credit: The New Front Door to Your Network“This infosteals focus on compromise credentials, and how the organizations can protect themselves.
This problem has led to law enforcement worldwide to actively crack on these cyber crime functions in recent tasks, such as “Operation Secure” and the disintegration of the lummastaler.
Since infostealers are so abundant and commonly used, the actor of danger telegram, release large -scale compilations on pastbin, and discord to achieve reputation as a teaser for the cyber crime community or for offerings made for offerings.
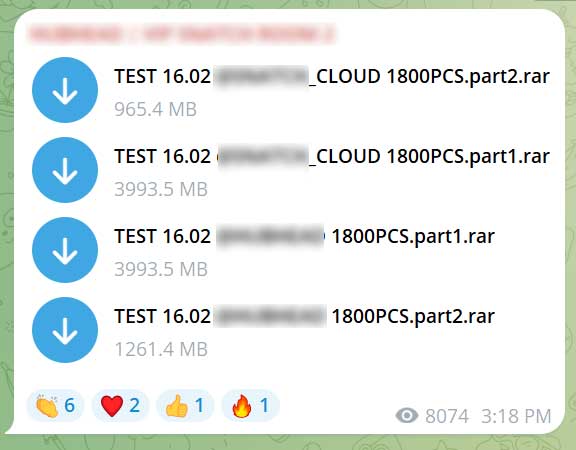
Source: Bleepingcomputer
To see how many passwords are provided for free, the upper image has a single 1,261.4 MB file 64,000 credential pairs.
There are thousands, if there are not hundreds of thousands, then the leaked archives are being shared online, resulting in billions of credensible records for free.
The possibility of many of these free archives was compiled on a large scale database that was briefly exposed and seen by cybernews.
Similar credential collections were released in the past, such as Rockyou2024 leakedWith more than 9 billion records, and “COLECTION #1”, which included more than 22 million unique passwords.
Despite the discussion, there is no evidence that this compilation includes new or earlier unseen data
what should you do?
Therefore, now that you know that there was a big leak of the possibility of the stolen credibility through infostallers, data brech and credential-stuffing attacks, you must be wondering what you should do.
The most important step is that you should already follow to adopt and maintain good cyber security habits.
If you are concerned that an infostealer may exist on your computer, scan your device with a reliable antivirus program before changing any password. Otherwise, newly recorded credentials may also be stolen.
Once you are convinced that your system is clean, focus on improving the hygiene of your password.
This means using a unique, strong password for each site you use, and relying on a password manager to maintain and secure them.
However, even unique passwords will not help you stay preserved if you are hacked, fall for a fishing attack, or install malware.
Therefore, it is important that you use a certification app as well as two-factor authentication (2FA), such as Microsoft authentic, Google GutenticatorOr EightTo manage your 2FA code. Some password managers, such as Bitwards and 1password, include certification functionality, allowing you to use an application for both.
With 2FA being competent, even if a password is compromised on a site, actor actor cannot reach the account without your 2FA code.
As a general rule, you should avoid using SMS texts to get 2FA code, as the danger actor can conduct a sim-swapping attacks to kidnap your phone number and get them.
As this leak, with this many credentials leaks, one of the readers of this article will be listed in compilation.
However, do not panic about it and do not stress, walk around all your passwords. Instead, take this opportunity to improve your cyber security habits.
To check if your credentials have appeared in known violations, consider using services Have i been pwned,
And if you use the same password on many sites, now is time to switch to unique people.
In this way, leaks in this way become very dangerous for you.



