Windows security is just more than basic virus safety. It guards against fishing, blocks ransomware, and prevents malicious app from moving. However, it is not easy to present these features – they are hidden behind the layers of the menu.
Protect sensitive files from ransomware
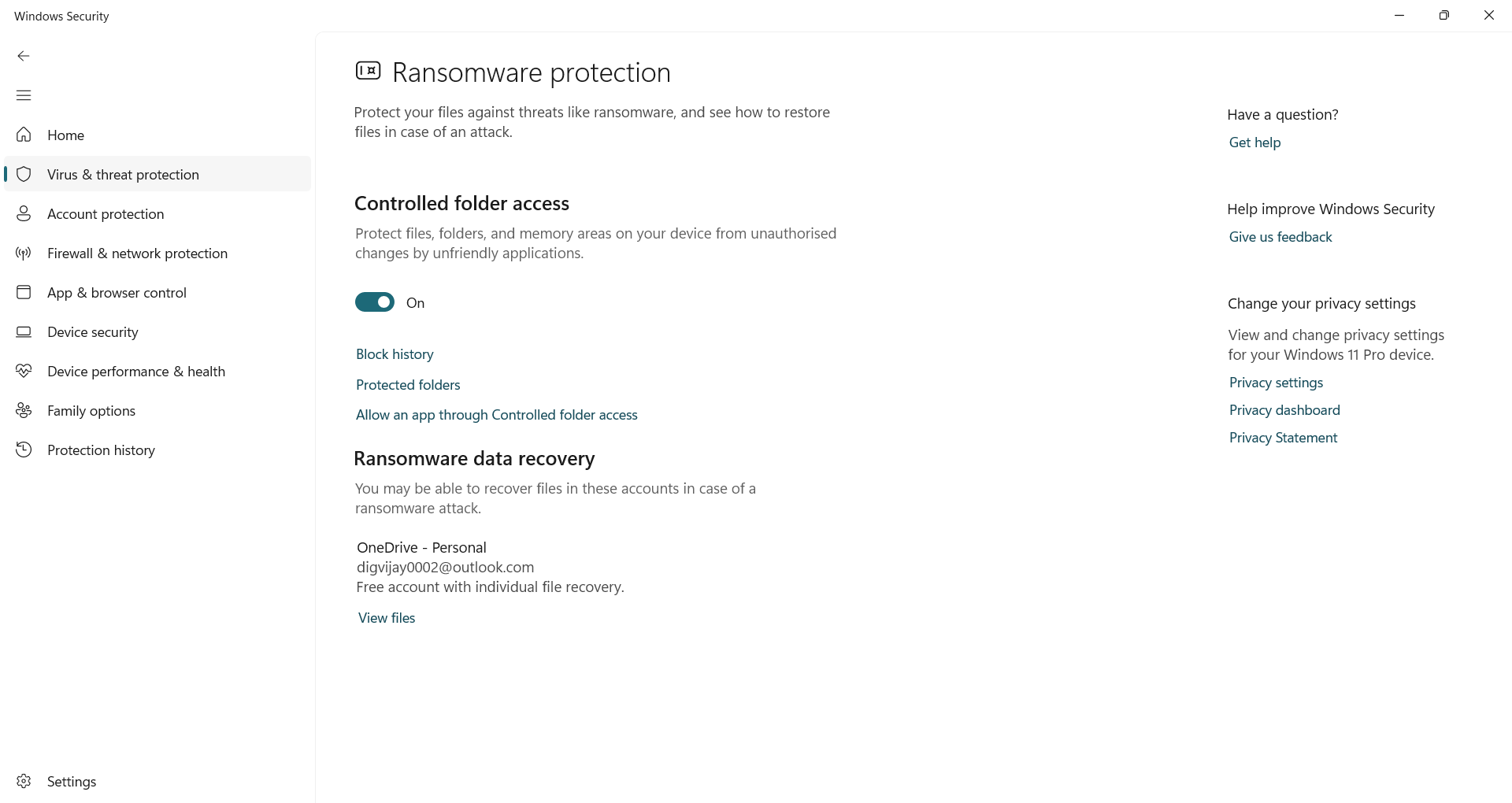
Downloading files or opening an unknown attachment always always causes some risk, especially if a ransomware becomes which can lock your files in seconds. Fortunately, Windows includes a feature Controlled folder access This helps to protect your most important folders from the same.
Once capable, it blocks incredible apps by modifying protected folders. By default, it covers places such as documents, pictures and desktops, but you are not limited to them only. You can click Protected folder To connect other places that you care about, such as work projects, financial records, or files stored on external drives.
To turn it on, open Windows securityGo Virus and danger protectionClick again Manage ransomware protection Below Ransomware protection Section. From there, togle Controlled folder access,
If a reliable app is blocked, Windows will often not inform you. To find out what was blocked, open Conservation history The section, where Windows logs recent efforts to reach protected folders. Just look Blocked folder access And allow any app you recognize and trust.
And if a known app, Like your video editor or backup tool, faces problems, you can directly head Allow an app through controlled folder access To white and stop it Any future blockage.
Once it is set, the safety works quietly in the background. If the ransomware or any suspicious app tries to intervene, Windows will immediately block it, keep your files safe without raising your finger.
Block malicious or incredible apps automatically
Threats do not always look suspicious. The file you download may seem useful, but it may install trackers, malware, or otherwise. Even a fake login page can be sufficient to fool anyone. A wrong click, and your login details may fall into the wrong hands.
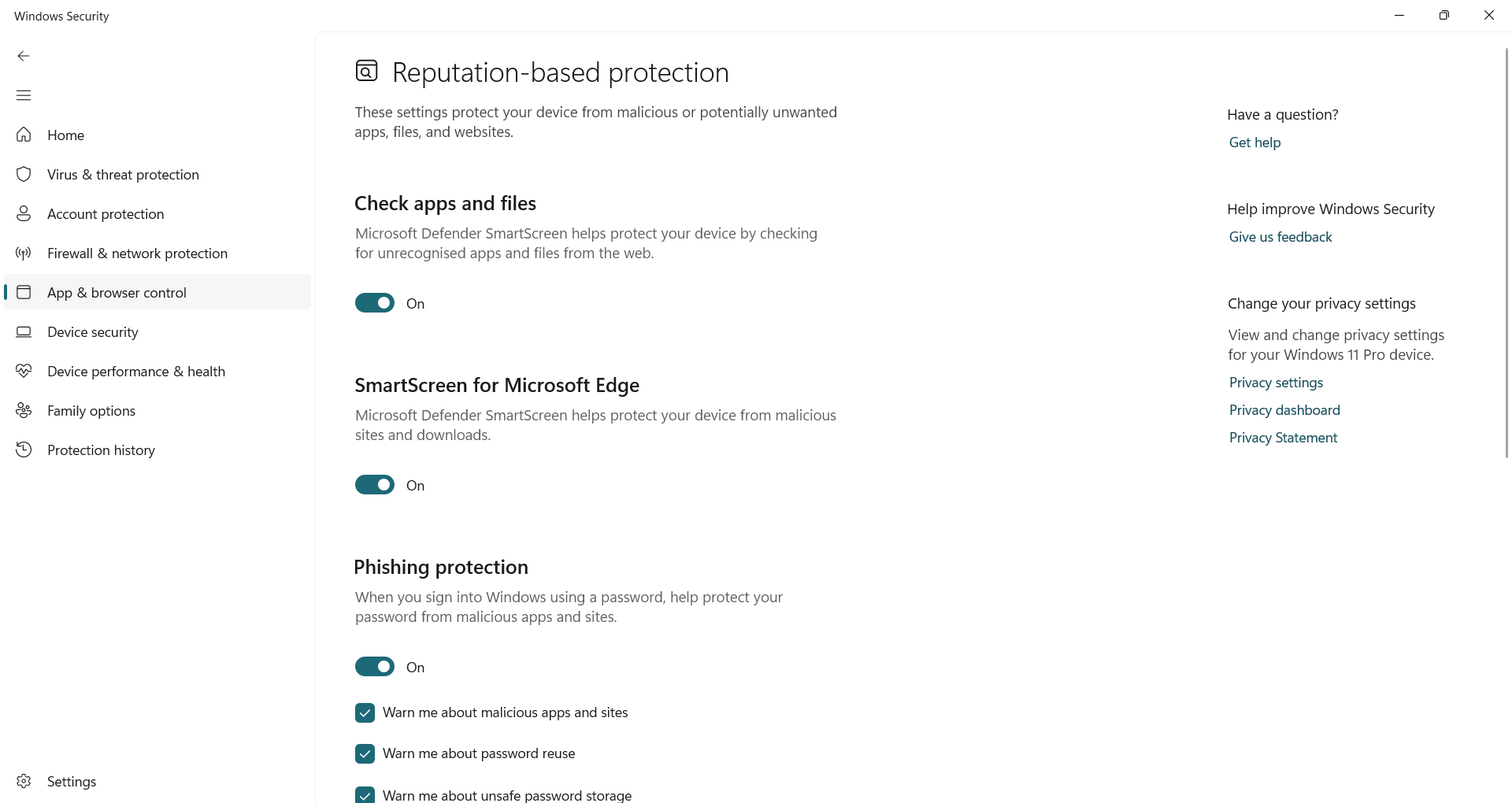
The reputation-based security manufactured in the protection of windows, prevents these dangers before reaching you. Using Microsoft’s Real-Time Threat Intelligence, it blocks shady apps, suspected downloads, and blocks fishing sites, so you will not have to guess another with every click.
To turn it on, open Windows security Go more App and browser controlClick Reputation-based protection settingsThen turn on all available options: Check apps and files, smartscreen for microsoft edge, potentially unwanted app blockingAnd Fishing protection,
Once it becomes active, Windows silently monitors your activity in the background. If a file or site appears risky, you will receive a warning before the execution is executed. You can still approve apps that you trust, but these underlying checks help you avoid a mistake that can spend you later.
Use offline scan for stubborn dangers
Some malware is sophisticated enough to get out of regular scans. It hides deep inside your system, starts walking even before loading the windows, and causing damage in the background, while it begins to detect.
When this happens, a normal scan is usually not enough. So Windows contains an offline scan, which conducts a deep check before Windows starts. In this way, hidden hazards do not get a chance to load or intervene.
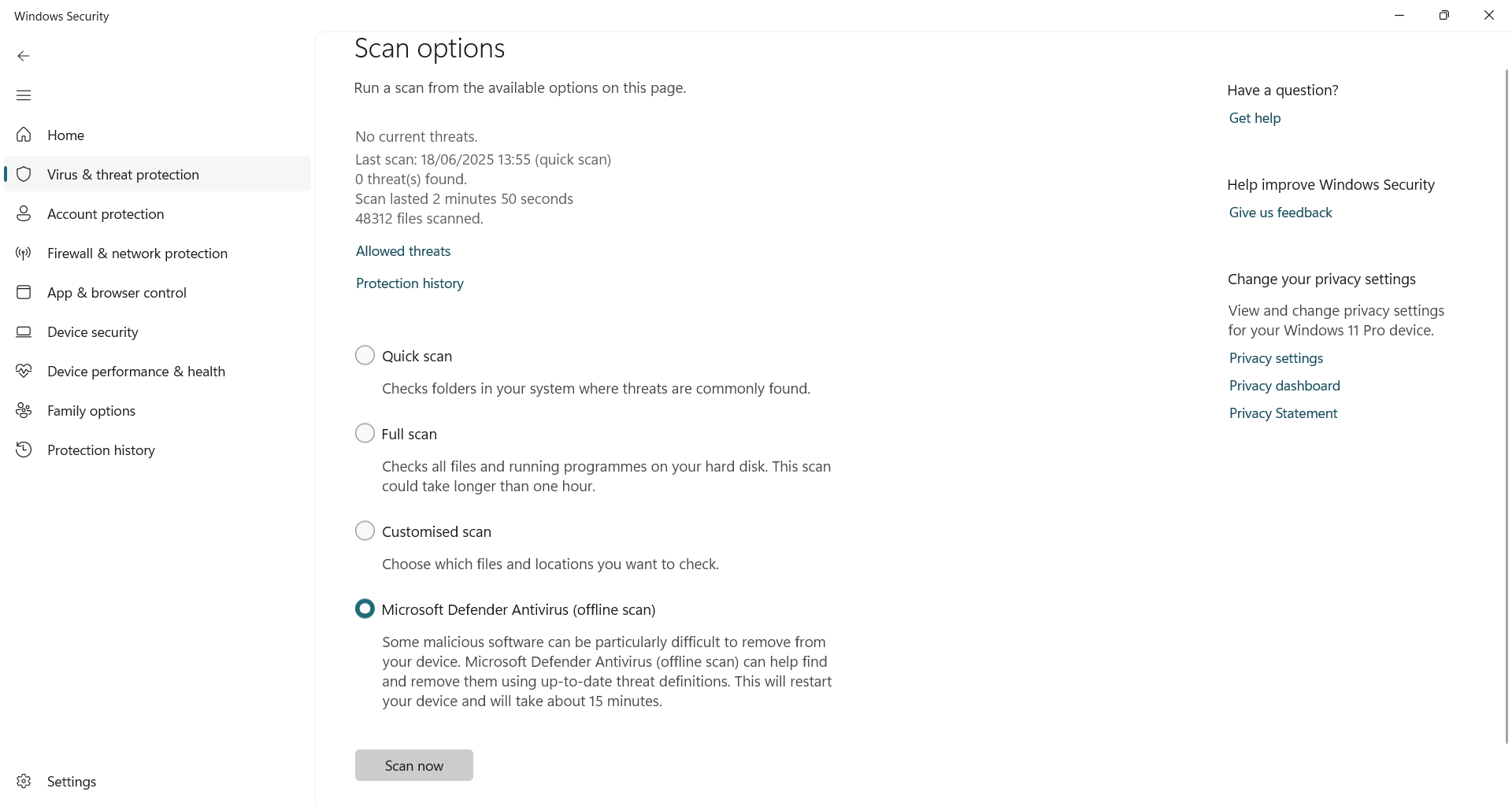
Open it Windows securityGo to Virus and danger protectionClick again scan options,
choose Microsoft defender antivirus (offline scan) And click scan Now,
Your PC will restart, will do the scan in a clean position, and when it is done will return to your desktop. It takes only 15 minutes, and once it starts, you do not need to do anything. Open when it is finished Conservation history To see if something was found or removed.
Memory mold your system with integrity
Your system memory handles some of the most sensitive tasks on your PC. If the malware manages to reach that level, it can tamper with important processes, install evil drivers, or quietly take control without touching their individual files.
Memory integrity acts like a security post in the heart of your system. This creates a protected environment using virtue, which seals vital processes with anything incredible. If some shady makes its way, it blocks the moment he tries.
To activate it, navigate Windows Safety> Device Safety> Core isolation detailsIf the memory integrity is discontinued, togle it. You may be motivated to restart your PC.
If the togle does not work immediately, Windows can flagged an old driver or app that is causing conflict. In that case, try updating or restoring the affected software. Once everything goes on, memory integrity should be started without any problem.
Exploit security settings for systems and programs
Most security dangers try to trick you to install some shady, but exploitation is a little secretly. Instead of seeking permission, they slip through hidden flaws in your apps. All of this is an unseen vomiting to inject the code for an attacker, hijack a process, or quietly take control of your system.
Exploitation protection helps to close those intervals before anything can be worse. Rightly built in Windows, it acts as a reinforced shield around the weak spots of your software. This monitors for known attack techniques and prevents them automatically, even though the app is not yet patching. Whether it is your browser, PDF viewer, or another everyday program, this feature helps prevent those apps from being against you.
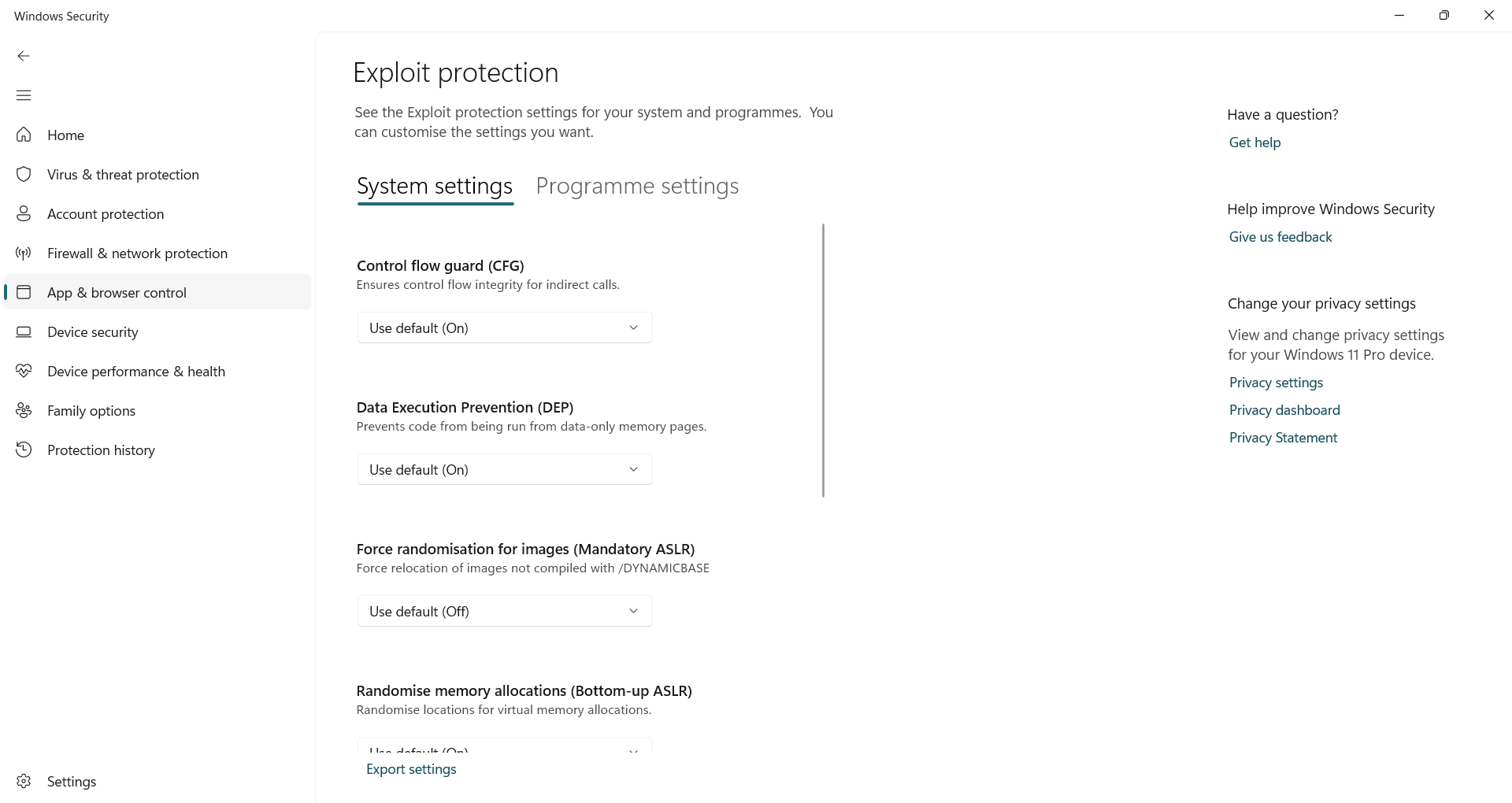
You will find it under Windows Security- Head to to App and browser control And click Exploit safety settings on the bottom. This includes two sections: System settingsWhich are capable by default, and Program settingsWhere you can make a custom rules for a personal app.
To lock a specific app, go on Program settings Tab and click Add programs to customize, Select an app or its .exe file, then enable advanced rescue, such as Control flow guard, Data performance preventionOr Compulsory AsLR, To block the common exploitation strategy.
As long as you are troubleshooting or locking the high-risk app, the omission is usually sufficient. But if you want more control, exploitation protection gives you flexibility to tighten safety.
Fix TPM safety issues with a quick reset
TPM (trusted platform module) is a small but required chip manufactured in your computer. This handles important security tasks, such as storing encryption keys and verifying hardware integrity.
However, after a major Windows update, BIOS change, or hardware upgrade, TPM-related problems can sometimes appear. You can withstand Bitalocker errors, warnings about issues signed with Windows Hello, or security processors.
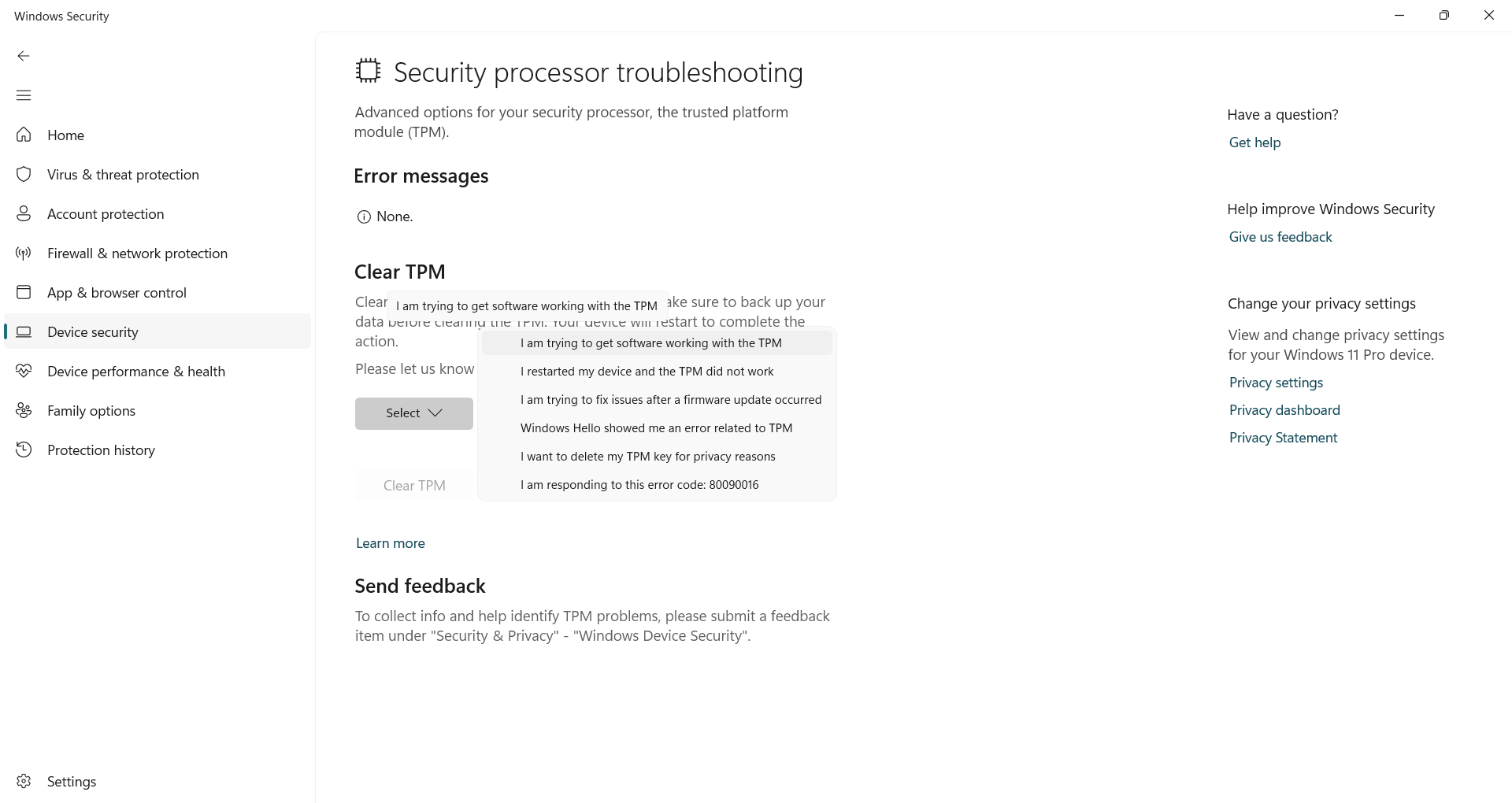
Fortunately, most TPM issues can be decided by resetting it through Windows security. This process cleanses its stored data and re -presenting the chip, which often fixes the problem without affecting your individual files. Just keep in mind that you may need to re -configure some characteristics such as Bitalocker or Windows Hello later.
To reset TPM, open Windows Safety, Go Device securityAnd click Safety processing detailsChoose again Safety processing troubleshootingChoose a reason for reset, and hits Clear TPMYour PC will restart to complete the process.
If you do not see a TPM option, you may need to enable TPM in BIOS first. Check your BIOS settings for something called TPM, FTPM, or PTT (based on your hardware), and make sure it turned on before trying again.
Control what your family can see and what can do
Family option panel Windows Security has a direct relationship between the Microsoft family protection, which gives you a central location to determine the boundaries and monitor how your device is used.
From here, you can manage the screen time, limit the app and game, filter the web content, and apply rules for each member of your Microsoft family group. It is particularly helpful to guide the use of your child and prevent contact with unprotected materials or unpublished downloads.
To access it, open Windows security, scroll Family optionAnd click See family settingsThis will take you to the Microsoft Family Safety Dashboard in your browser, where you can create a child account, set the ban, and check the activity report.
These settings are attached to your child’s microsoft account and carry on any Windows device used by them. If they try to reach something that is blocked, you will receive a notice and choose whether to approve or reject the request.
So, these are some of the most powerful characteristics tucking inside the Windows Security. They help you to protect your files, manage dangers and maintain control of your device’s safety. If you haven’t discovered them yet, now is a good time to start.