
A new wave of North Korea’s ‘infectious interview’ campaign is targeted by job seekers with evil NPM packages that infect Dev’s equipment with Infosellers and Backdore.
Packages were discovered Socket threat researchThose who report that they load the two-well-recorded payloads associated with the Beertel Information-Stellar and Invitating Backdor, DPRK actors on the machines of the victims.
The latest attack wave uses 35 malicious packages presented to NPM through 24 accounts. The packages have been downloaded more than 4,000 times in total, and six of them are available at the time of writing.
Many of the 35 malicious NPM packages mimic typosquat or mimic to mimic famous and reliable libraries, making them particularly dangerous.
The remarkable examples of them are:
- React-Plade-SDK, Reactbutstrapes
- Vite-plugin-next-Refresh, Vite-LODER-SVG
- Node-mongoz
- jsonpacks, jsonspecific
- Chalk kaf
- Node Loggors, *-Kalger
- Framar-Motion-Apt
- Nextjs-inight
- Structure-logger, logbin-nod
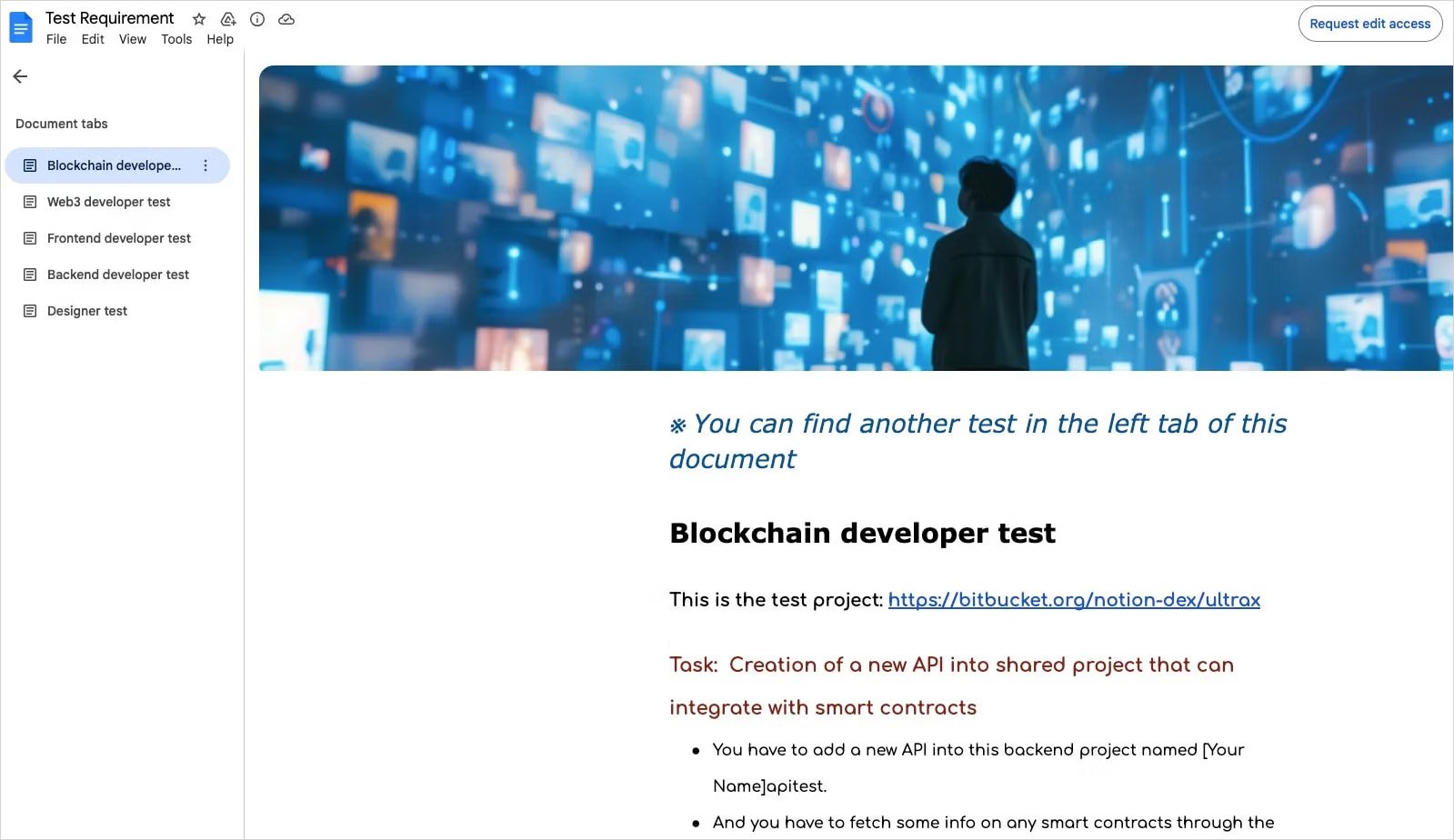
The victims, usually software engineers and developers, are led by North Korean operatives to download these packages, which are presented as recruitments, who request job candidates to work on a test project.
“As a recruiter on LinkedIn, North Korean dangers send” assignments “to the developers and job seekers through the North Korean threat actor Google Docs, embedding these malicious packages within the project, and often pressurizing candidates to run code while screen-sharing.”
Source: socket
The assignment is hosted on the bitbacket and disguised as legitimate tests, but in fact, they trigger a transition chain that drops several payloads on the target computer.
The first stage is the hexwell loader, which is hidden in NPM packages, which fingerprints the host, contacts the actor’s command-end-control (C2) server, and uses ‘eval ()’ to bring and perform the second phase payload, bearrtel.
Beertel is a multi-platform information-steller and malware loader, stealing browser data, including cookies and cryptocurrency wallets, and loads the third stage, invisible.
The invisible is a cross-platform consistent backdor that is given as a zip file, providing the attackers to the afflicted system with deep, remote control, file theft and screen-performance capabilities.
Finally, the attackers release a cross-platform (Windows, MacoS, Linux) Keyloxon tools that hook in low-level input events and make real-time monitoring and data exfoliation.
This kelogger was only associated with one of the NPM surnames used in the campaign, so it can only be deployed on selected high-value goals.
.jpg)
Source: socket
Software developers contacted with attractive remote job offers should treat these invitations carefully and always run unknown code in containers or virtual machines instead of executing it on their OS.
Last March, North Korean hackers Lazarus were caught presenting another set of malicious packages on NPM, so it is an ongoing risk.



