
Actor is misusing the Connectwaiz Screnconconable Installer threatening to construct signed remote access malware by modifying the settings hidden within the client’s authentic signature.
ConnectWise Screenconnect is a remote monitoring and management (RMM) software that allows it to remove devices remotely to admins and managed service providers (MSPS).
When a screenconnect installer is created, it can be adapted to include a remote server that the client should connect, what text is shown in the dialog box, and the logo that should be displayed. This configuration is saved within the authenticode signature of the data file.
This technique, called authenticode stuffing, allows the insertion of the data to be inserted into the table while retaining the digital signature.
Abuse for initial access was misused
Cyberspace firm Ghi data saw All file categories except the certificate table, malicious connectwaizer binergies with the same haveh value.
The only difference was a modified certificate table that had a new malicious configuration information, while the file was still allowed to be signed.
G Data says that the first samples were found in the blepping computers forums, where members reported to be infected after falling for the fishing attacks. Similar attacks were reported on Reddit.
These phishing attacks used PDF or mediated canva pages, which were associated with the executable host hosted at Claudflair’s R2 Server (R2.DEV).
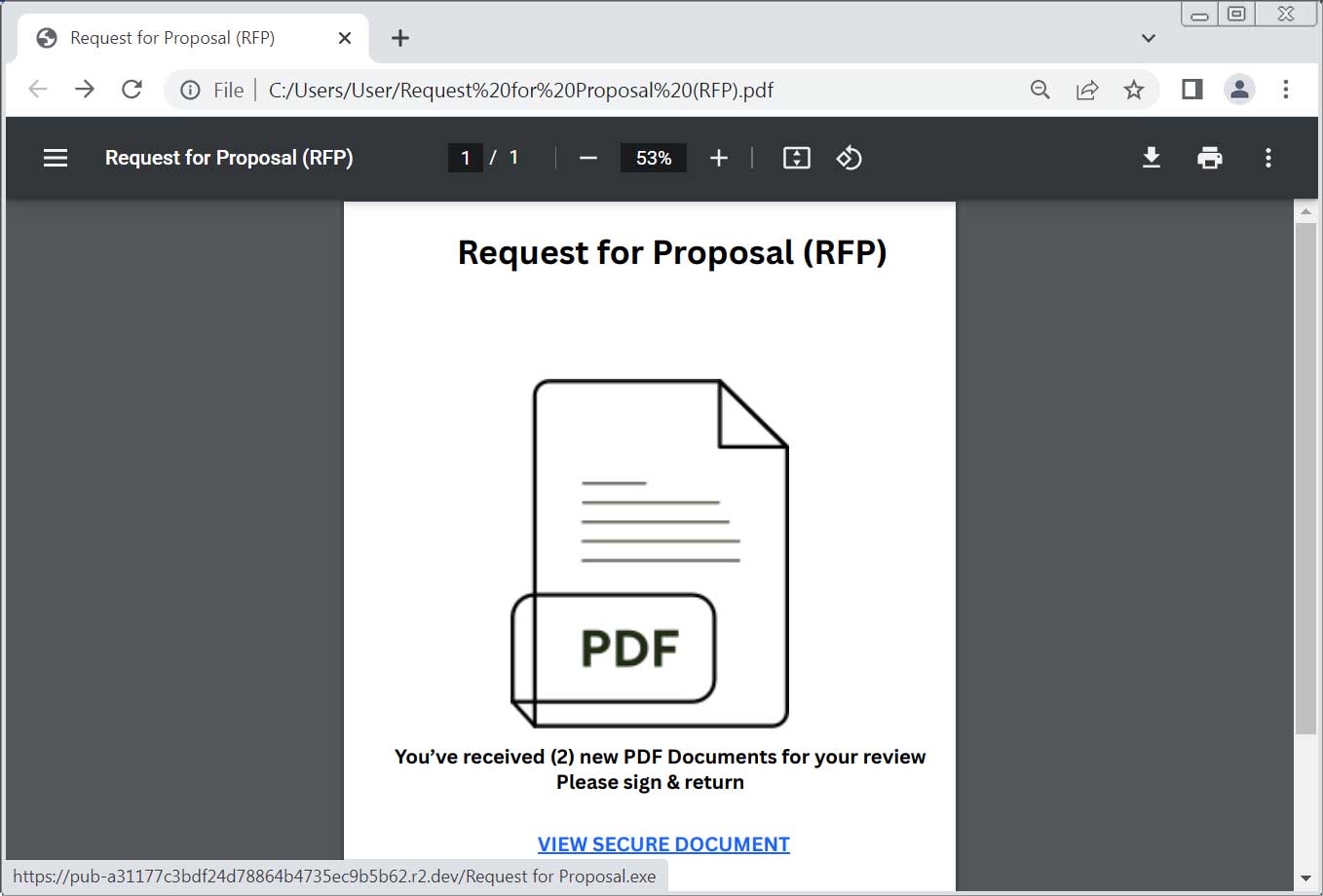
Source: Bleepingcomputer
File viewed by bleepingcomputer, “request for proposal.Wirstotal) 86.38.225 (.) On 6: 8041, configured to connect the attacker’s server
G data created a tool to remove and review the settings found in these campaigns, where researchers found significant amendments, such as converting the title of the installer into “Windows updates” and the background with the fake Windows update image shown below.
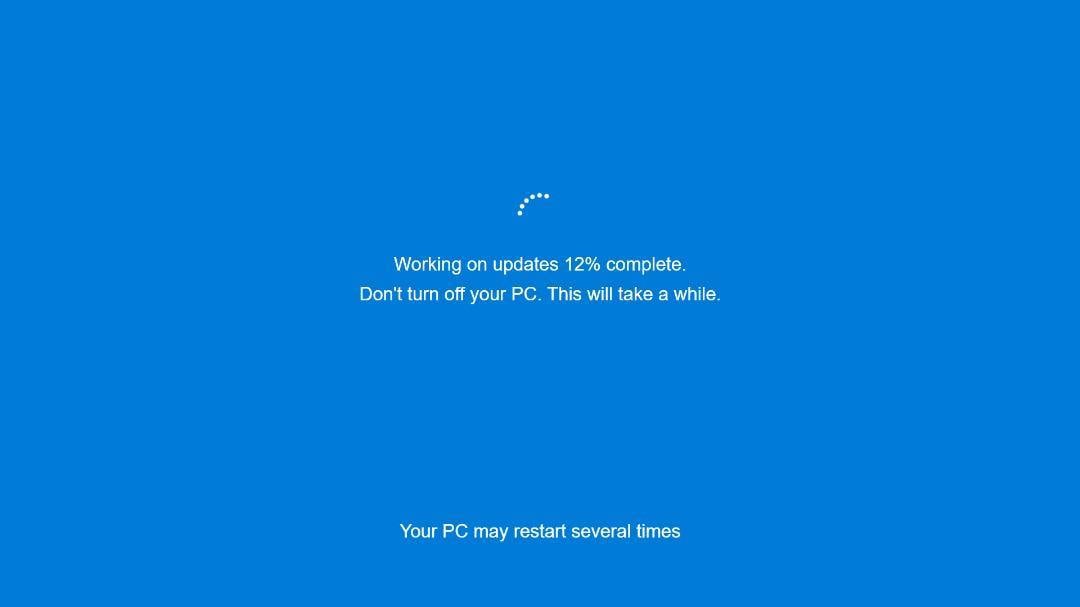
Source: G data
Essentially, the danger actors converted the legitimate connecting screensacconomct clients into malware, which allows them to have access to the infected infected equipment.
After contacting G data, Connectwaiz canceled the certificate used in these binergies, and G data is now marking these samples as win32.backdoor.evilconwi.
G Data says that he never got a response from connectivity about this campaign and his report.
Another expedition is also enterprise software, this time distributing traogenous versions of the user name, password and domain information to steal the Sonicwall Netextender VPN clients.
According to a advisor to Sonicwall, these revised versions send credentials captured on an attacker-controlled server, making it important for users to get software clients from only official sites.



