Malibly software can easily find your way on your computer and remain uncontrolled from there. However, with the right equipment, you can scan your system and remove spyware, adhaware and other malicious programs that can be hidden on your system.
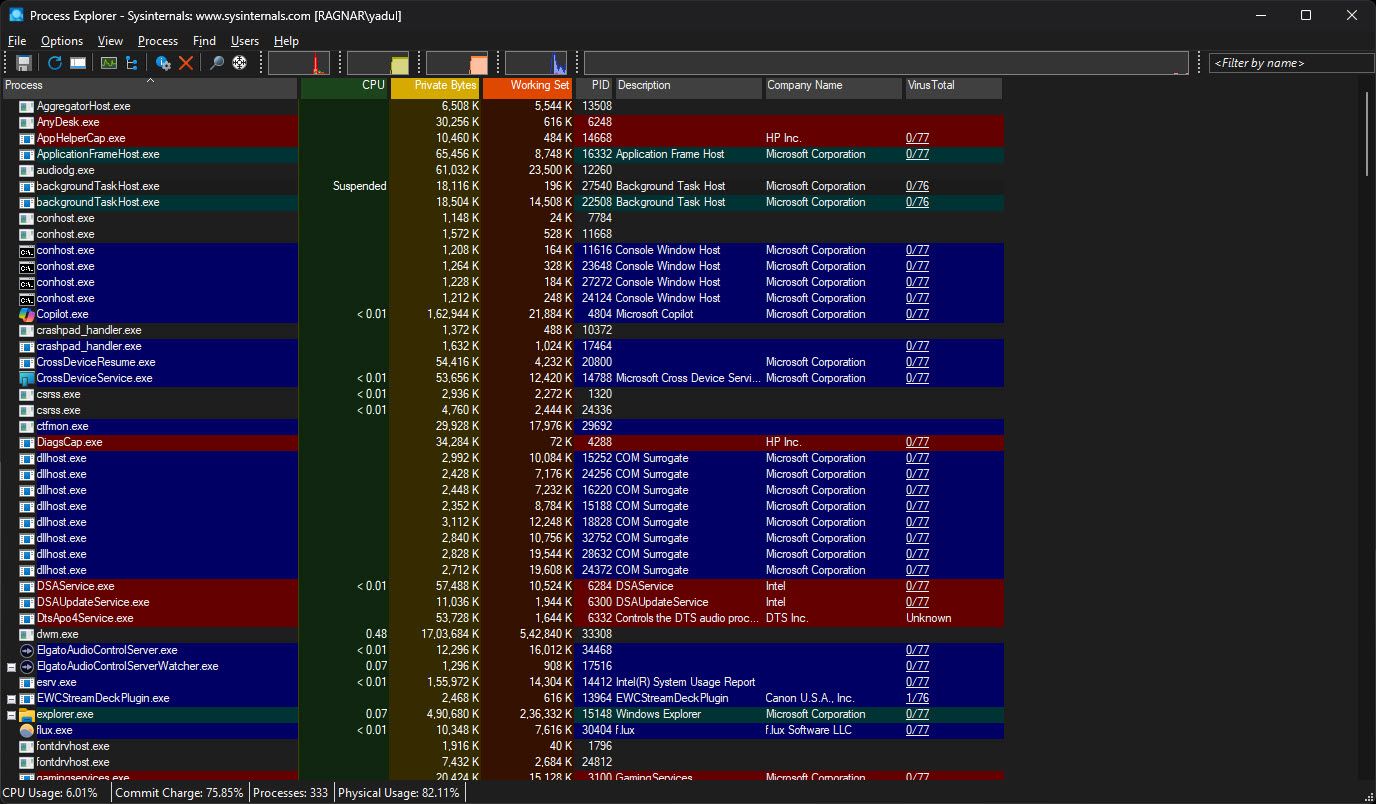
The process is part of the explorer tool Sisinarnals The suite of programs from Microsoft, which provides extended functionality and replaces the preinstold tools such as the task manager. In the case of Process Explorer, the program provides information about the handle and DLL that has been opened or loaded on the system on the system.
The program makes the evil DLL running on your system incredibly easy and determines which programs are using these files. Additionally, it is also useful for tracking the problems of the DLL version, handling leaks and providing information about Windows and application work.
This may be intimidating at first glance, but the interface is surprisingly friendly to the user, and spending some time with the program will clarify the purpose of many areas and buttons. moreover, Microsoft process explorer documentation This involves important information about how it works and how to use it more effectively.
For everyday Windows user, Processes is a bus task manager on explorer steroids. You can not only see which procedures are going on your system and how many system resources they are consuming, but also run a wirestotall scan directly from within the equipment. It provides an initial check of the potentially malicious devices on your system and a good bird view. This enables you to match the hash to the process against the known good and bad ish, which will help you find out whether the process is malicious or not.
You can also use a procedure explorer to track network activity run by a specific procedure. Right-click on the process you want to check, select PropertyAnd then navigate TCP/IP Tab. You will be able to see all the ongoing network connections that are using the process – it is a very easy way to check whether a program on your PC is connecting with the malicious server. A slight negative side for this is that the process explorer does not display historical network connections; However, it is easy to identify malicious processes that are currently running.
Last but at least, Process Explorer also shows you that the command prompt command requires a particular program to launch to hover over the process for a few seconds. Checking commands can reveal special keys, flags or instructions, a malicious program system can use to achieve access to system resources.
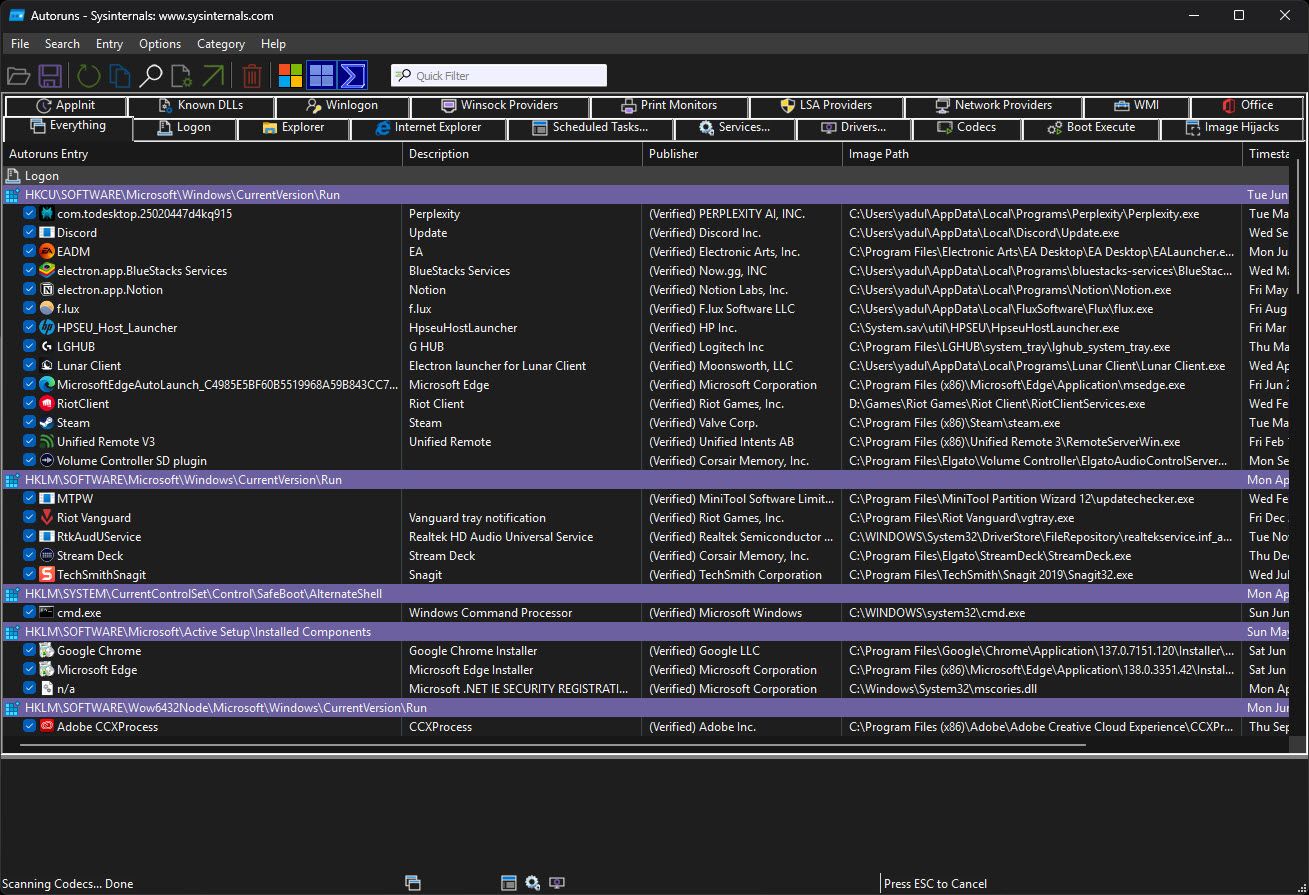
Sysinternals also takes part of suite, replacing autoruns Startup apps The task manager tab, which shows all the apps that are completely loaded as Windows. It also shows all other processes, including DLL files, services, scheduled functions and even registry entries-everyone is classified under a well-defined tab.
Autoruns makes any malicious executable, DLL, and spotting tasks incredibly easy that can begin with your Windows system. Malware often combines scheduled functions in Windows, allowing it to start with your system and maintain firmness automatically. With autoruns, you can quickly check suspicious procedures, run virustotal scans if necessary, and eliminate them.
In addition to hunting spyware and other malicious programs, Autorun is also very good to customize your PC. Many settings scattered throughout the windows, instead of jumping around the windows, you can disable all unwanted programs and procedures that begin with the windows at once. This can still be useful when you are troubleshooting Windows to examine any program, which can cause crash or system instability during startups.
Every time I set a new Windows PC, I use Autorun and Process Explorer to remove any suspicious or unwanted files. This is one of the best ways to remove the blotware from your PC, such as in addition to using external devices Windows 11 Debatter,
Connected
If you want a sharp, cleaner Windows 11 then you need this hack
Windows comes with a lot of extra accessories. This is about the time when you get rid of it.
While checking for spyware or malicious programs, I like to undergo the first main Everything Uncheck the tab and any program that appear suspicious or I do not need otherwise. Pay special attention to scheduled tasks The tab for any scheduled program begins and verification that all suspicious or unwanted programs are disabled. Be careful not to disable the required system procedures or microsoft-signed entries. If uncertain, consult the file name Google or Virustotal before taking action.
Subsequently, a simple system will show the restart that disabled procedures were causing issues or not. Once you identify a problematic process, you can remove the process permanently by right-clicking and selecting it from your system. deleteHowever, note that it does not remove malicious file (potentially underlying malware). This only prevents the process. Once you look at a malicious process, you will need to run a proper malware removal tool such as malwarebights.
Virustotal is the easiest ever and perhaps the most basic of all equipment you should do to check if a suspicious program is malicious in any way. In addition to checking individual files for malicious signature, the site also allows you to check the URL, hash, IP addresses and domains against the database.
This allows you to check quickly whether a file or a URL that is communicating with a process on your PC is malicious or not. This is one of the easiest ways to check if a downloaded file is safe before using it.
The device tests your files against more than 60 antivirus engines from various vendors. Since antivirus programs differ from each other and cannot always identify a malicious file, in a few clicks, as possible, there is a great way to check a file against many antivirus engines as possible.
Since it is an online tool, it is also a platform-independent, which means that you can upload a file from any device. It saves a lot of time and effort, especially if you want to check a file you may have found on your phone or tablet. However, its results are not certain, as you will note when you flag down some antivirus engine, while others ignore it. This is why it is best to use virustotal as part of a multi-level system for checking potential spyware, adware and malware.
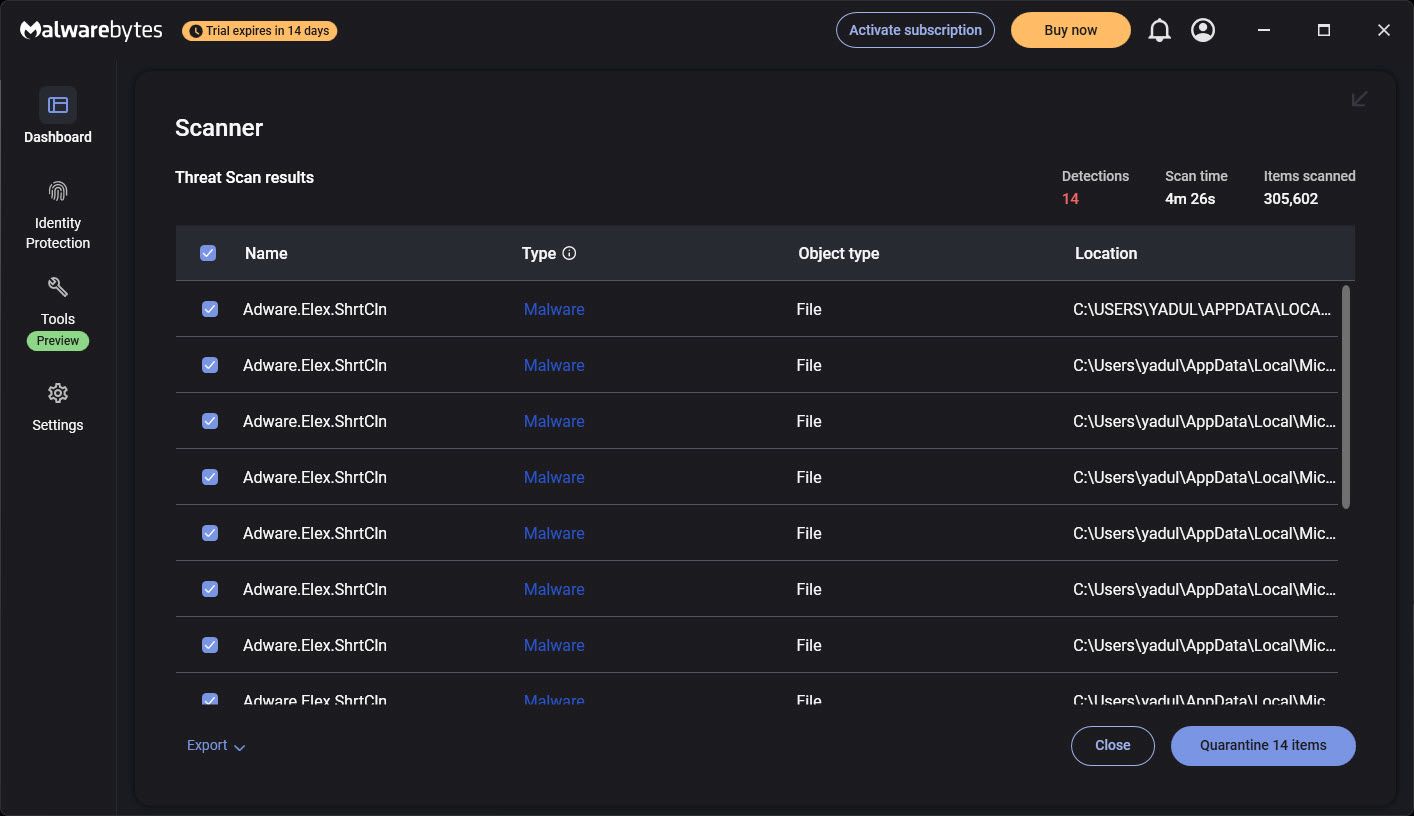
Malwarebytes are one of the best anti-malware and antivirus programs that you can install for free. This often detects files that are remembered by other antivirus programs, including Windows Security- Microsoft’s Micarosoft’s underlying antivirus solution for Windows.
Malwarebights are particularly effective in detecting adhaware. It can also quarrel and remove the adhaware manufactured in Microsoft Tools such as Edge, which Windows Security will ignore. It also has a suit of inherent equipment that lets you twist Windows Privacy Settings and Control Startup applications. If you choose a malwarebytes subscription, you will also get a built -in VPN and additional safety option, as well as the option to enable real -time system scanning to detect the dangers.

Connected
This new scam-checking app is so good that I trust it for the safety of my parents
I have tested malwarebights scam guards, and it is really quite useful.
To be clear, you can do all this with Windows safety or any other antivirus software that you are using. However, malwarebites scans are deep and often catch files that may miss other antivirus programs. Additionally, it is very easy to navigate the interface. If you are not a computer wizard, to ensure that everyone can clearly see suspicious files and decide what to do with them easily.
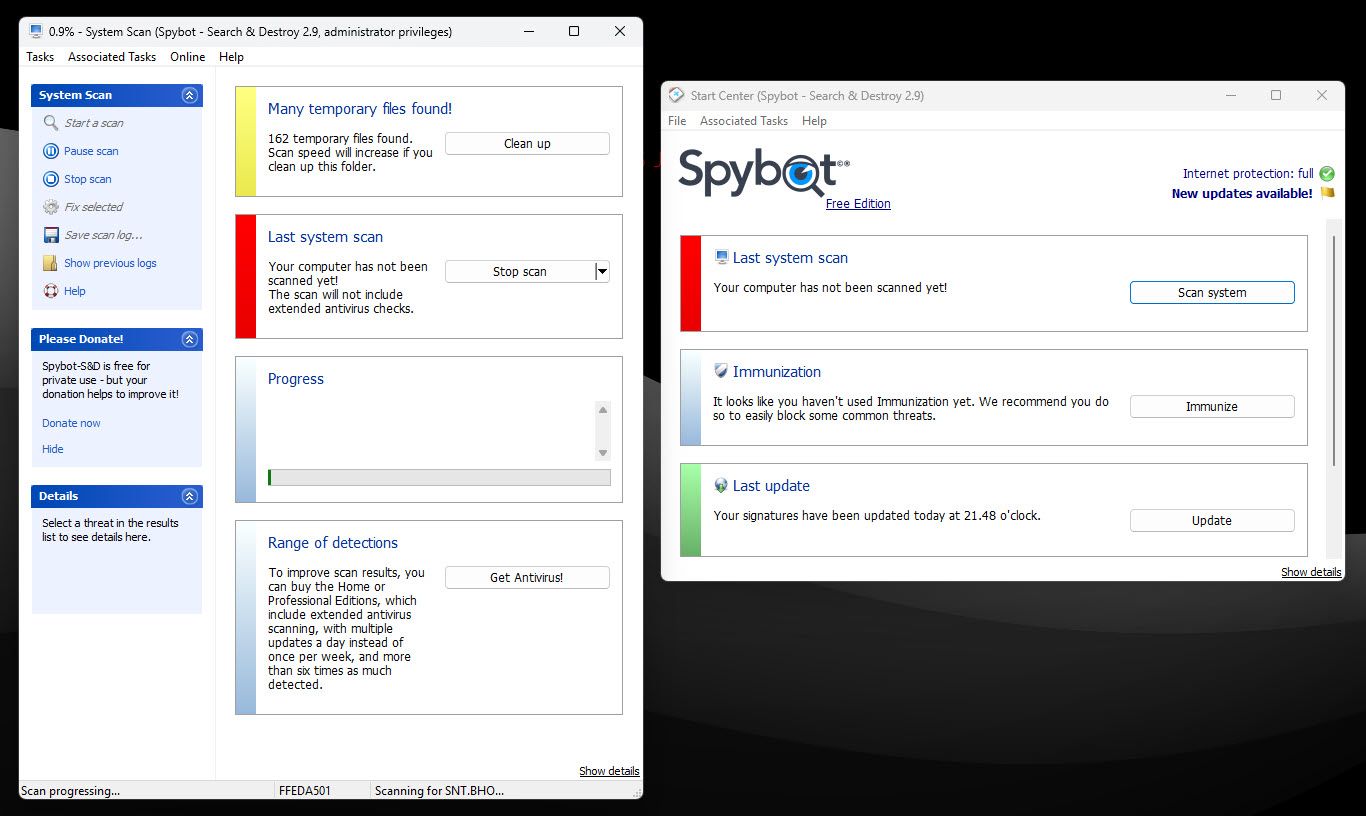
The spybot is certainly dated to some extent at this point; I remember to use it back in the early days of Kaza and Limavire. However, despite its old user interfaces, it is still a very easy tool to find and remove adhaware and spyware from your computer, as it specifically targets them. The spybot comes with an additional antivirus component, but it is not included in the free version.
Even without its antivirus engine, spybott is an easy anti-spyware app in hand as complement to your existing antivirus program. The setup process is also comfortable and allows you to select the tool for automatic safety or manually configure the settings.
Its primary features include detection and detection of spyware, adhaware, tracking software, keynues and other unwanted programs. Free version is also included System immunization The feature, which protects your system against malware by blocking access to known sites to host malware or other unwanted software. It also tracks cookies and browser plugins known to include malware. You also get a startup program control utility and rootkit scan.
Most other, more powerful features of the spybot are paid. However, when you are using it in combination with other devices such as Autorun, Process Explorer and an antivirus program, it offers sufficient capabilities to provide very comprehensive protection on free tier.
Spaiware can be very timid, and finding it on your system, sometimes with appropriate equipment, can be difficult. However, if you check multiple checks with the right equipment, they become relatively easy to spot and even become easier to remove. For best results, start with autorun and process explorer to identify suspicious procedures and startup items. Then, confirm any suspicious files with virustotal. Finally, run a full system scan with malwarebights and/or spybot to remove anything hidden in the background.