
A total of 689 printer models from brother, Fujifilm, Tosiba and 53 other models of Konika Minolta come with a default administrator password that can generate remote attackers. Worse, there is no way to fix the defect through firmware in existing printers.
Defended, tracked under Cve-2024-51978Is part of a set of eight weaknesses Rapid7 discovered by researchers Brother during a long test of hardware.
| CVE | Description | Affected service | CVSS |
|---|---|---|---|
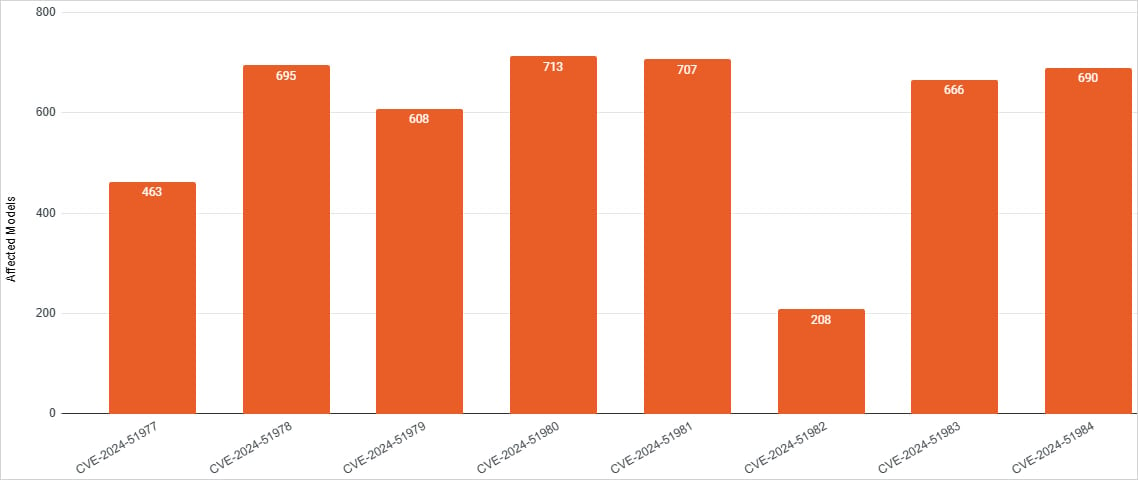
| Cve-2024-51977 | An informal attacker can leak sensitive information. | HTTP (Port 80), HTTPS (Port 443), IPP (Port 631) | 5.3 (medium) |
| Cve-2024-51978 | A default administrator of an informal attacker device can generate passwords. | HTTP (Port 80), HTTPS (Port 443), IPP (Port 631) | 9.8 (important) |
| Cve-2024-51979 | A certified attacker can trigger a stack -based buffer overflow. | HTTP (Port 80), HTTPS (Port 443), IPP (Port 631) | 7.2 (high) |
| Cve-2024-51980 | An informal attacker may force the device to open a TCP connection. | Web services on http (Port 80) | 5.3 (medium) |
| Cve-2024-51981 | An informal attacking may force the device to request an arbitrary HTTP. | Web services on http (Port 80) | 5.3 (medium) |
| Cve-2024-51982 | An informal attacker can crash the device. | PJL (Port 9100) | 7.5 (high) |
| Cve-2024-51983 | An informal attacker can crash the device. | Web services on http (Port 80) | 7.5 (high) |
| Cve-2024-51984 | A certified attacker may disclose a password of a configured external service. | LDAP, FTP | 6.8 (medium) |
This important vulnerability can be chained by chains with chains with crash or pivot within the network with other weaknesses discovered by Rapid 7, taking control of equipment, taking control of equipment, performing remote code, or pivot within the network.
Not all flaws affect each one of the 689 brother printer model, but other manufacturers including Fujifilm (46 models), Konika Minolta (6), Ricoh (5), and Toshiba (2) are also affected.
Source: Rapid 7
Unprotected password generation
The default password in the affected printer is generated during manufacturing using a custom logirtham based on the serial number of the device.
according to a Detailed technical analysis By Rapid 7, the password generation algorithm follows an easily reversible process:
- Take the first 16 letters of the serial number.
- Add 8 bytes obtained from a stable “salt” table.
- The result is the result with sha256.
- Base64- Hash Hash.
- Take the first eight letters and replace some letters with special characters.
Attackers can leak the serial number of the target printer using or exploiting various methods. Cve-2024-51977They can then use algorithm to generate default administrator passwords and log in as administrators.
From there, they can configure the printer again, access the stored scan, read the address books, exploit Cve-2024-51979 Distance code for execution, or exploitation Cve-2024-51984 For harvesting credentials.
Rapid 7 started its disclosure process in May 2024 and assisted by JPCERT/CC in coordination of revelations for other manufacturers.
Although all flaws have been fixed in the firmware update provided by the affected manufacturers, the case is complicated with CVE-2024–51978 in terms of risk management.
The vulnerability lies in the password generation logic used in hardware manufacturing, and therefore, there will be predicted passwords in any devices made before its discovery until the users change them.
“The brother has indicated that this vulnerability cannot be completely removed in the firmware, and requires a change in the manufacturing process of all affected models,” Rapid 7 explains about CVE -2024-51978.
The users of the current brother printer listed in the affected model consider their devices to be unsafe and immediately change the default administrator password, after which the firmware applies updates.
In general, it is recommended to restrict access to the unprotected protocol and external network’s administrator interfaces.
Security bulletin with instructions on what users should do Brother, Konika Minolta, Fujifilm, RicohAnd Toshiba,



