
Arc Linux has drawn three malicious packages uploaded on the Arc user repository (AUR), used to install Caous Remote Access Trojan (RAT) on Linux devices.
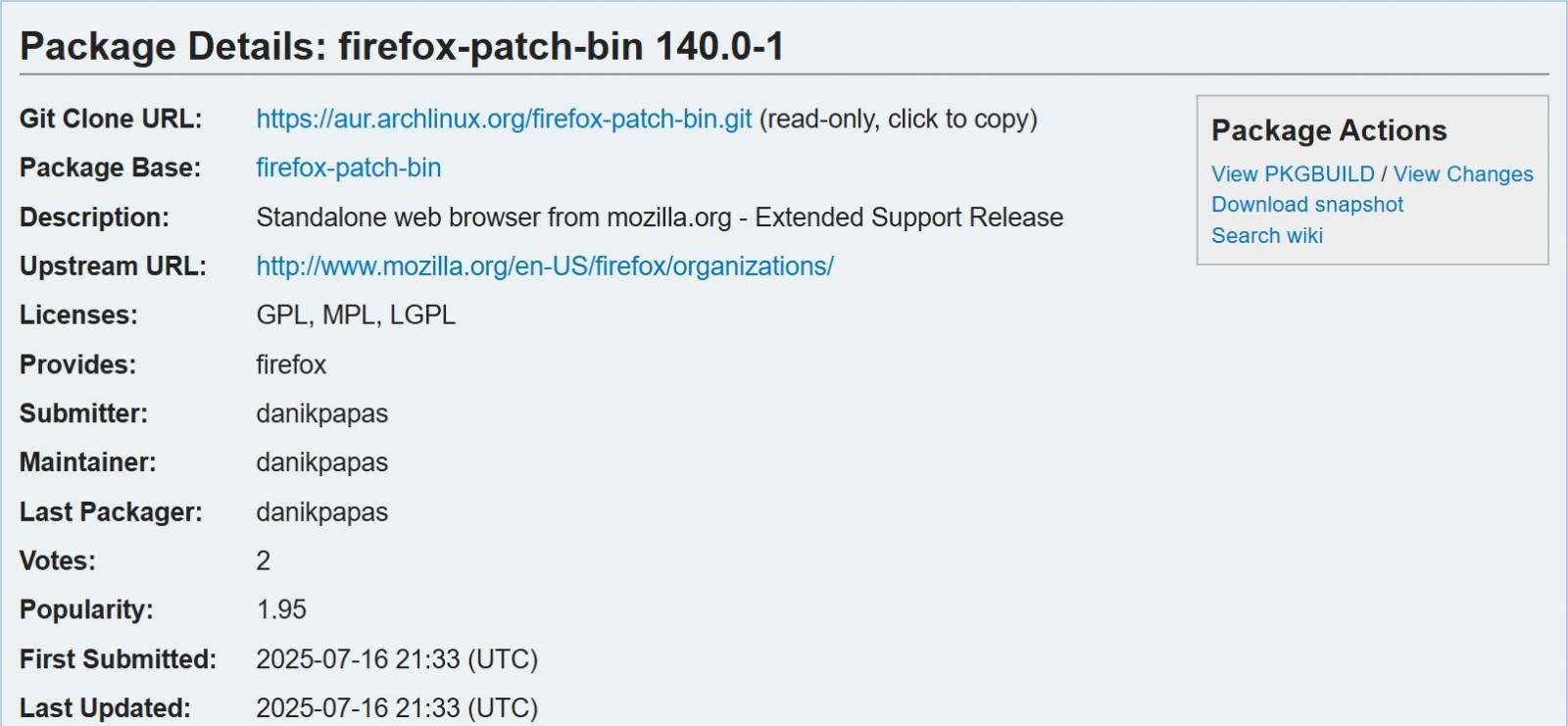
The packages were named “Libravolf Fix-Bin”, “Firefox-Patch-Bin”, and “Zen-Buruser-Pitted-Bin”, and uploaded by the same user, “Danikpapas,” on 16 July.
The package was removed two days later by the Arc Linux team after being marked by the community as malicious.
“On July 16, at around 8pm UTC+2, a malicious Aur package was uploaded on AUR,” Aur warned maintenance,
“Two other malicious packages were uploaded by the same user a few hours later. These packages were installing a script coming from the same Github repository that was identified as remote access Trojan (RAT).”
Source: Bleepingcomputer
Aur is a repository where arch Linux user can publish the process of downloading, construction and installing the packgbuilds, which is not included with the operating system.
However, like many other package repository, AUR has no formal review process for new or updated packages, allowing it to review the code and installation script before you create and install the package.
Although all the packages have now been removed, the Bleeping Computer found the stored copies of the three, indicating that the danger actor started submitting the package on 18:46 UTC on 16 July.
Each package, “Librewolf-FIX-bin,Firefox-patch-bin“, And “Zen-Buruser-Pachade-Bin“All included a source entry in the PKGBuild file, called” called “Patch“It pointed to a github repository under the control of the attacker:
When buildpkg is processed, this repository is cloned and considered as part of the patching and building process of the package. However, instead of having a valid patch, the Github repository contains malicious code that was executed during the build or installation phase.
This github repository has been removed since then, and .git repository is no longer available for analysis.
However, a Reddit account today began to respond to various arch linux threads on the platform, which promotes these packages on AUR. The comments were posted by an account that seems passive in the years and possibly compromised to spread malicious package.
Hardcore user reddit Quickly found the comments suspect, one of them uploaded one of the components WirstotalWhich finds it as a linux malware called chaos rat.
The Caos rat is an open-source remote access trojan (rat) for Windows and Linux that can be used to upload and download files, execute the command and open a reverse shell. Finally, danger actors have complete access to an infected device.
Once installed, the malware is repeatedly connected to a command and control (C2) server, where it waits to execute the command. In this campaign, the C2 server was located at 130.162 (.) 225 (.) 47: 8080.
Malware is usually used in cryptocurrency mining campaigns, but it can also be used to cut credentials, steal data or cyber.
Due to the severity of malware, whoever accidentally installed these packages, should immediately investigate a suspected “Systemd-Initd” executable for the appearance on their computer, which may be located in a /TMP folder. If found, it should be removed.
The Arc Linux team removed all three packages till 18 July at UTC+2 at around 6 pm.
“We strongly encourage users who have taken necessary measures to remove one of these packages from their system and to ensure that they were not compromising,” the Arc Linux team warned.



