
The recently discovered ransomware can bypass UEFI Secure Boot features to set up a malicious application on the Hybridptia EFI system division called Strain.
Hybridptia appear to be inspired by destructive patya/NOTEPA malware that encryps the computer and prevented the windows from booting in attacks in 2016 and 2017, but did not provide a recovery option.
Researchers at Cyber Security Company ESET found a sample of hybridpetya on gerostertal. They note that this can be a research project, a proof-off-concept, or an early version of the cybercrime tool that is still under a limited trial.
Nevertheless, ESET states that its presence is still another example (with Blackalotus, Bootcist and Hyper-V Backdor) that UEFI bootkit with safe bypass functionality is a real danger.
Hybridptia contains the characteristics of both Petya and Notepya, including the visual style and attack chain of these olderware strains.
However, the developer added new things such as installation in the EFI system division and the ability to bypass safe boots by exploiting CVE -2024–7344 vulnerability.
The ESET discovered the defect in January this year, with the Microsoft-Sign Apps in the issue, which can be exploited to deploy bootkits even with safe boot protection active on the target.
Source: ESET
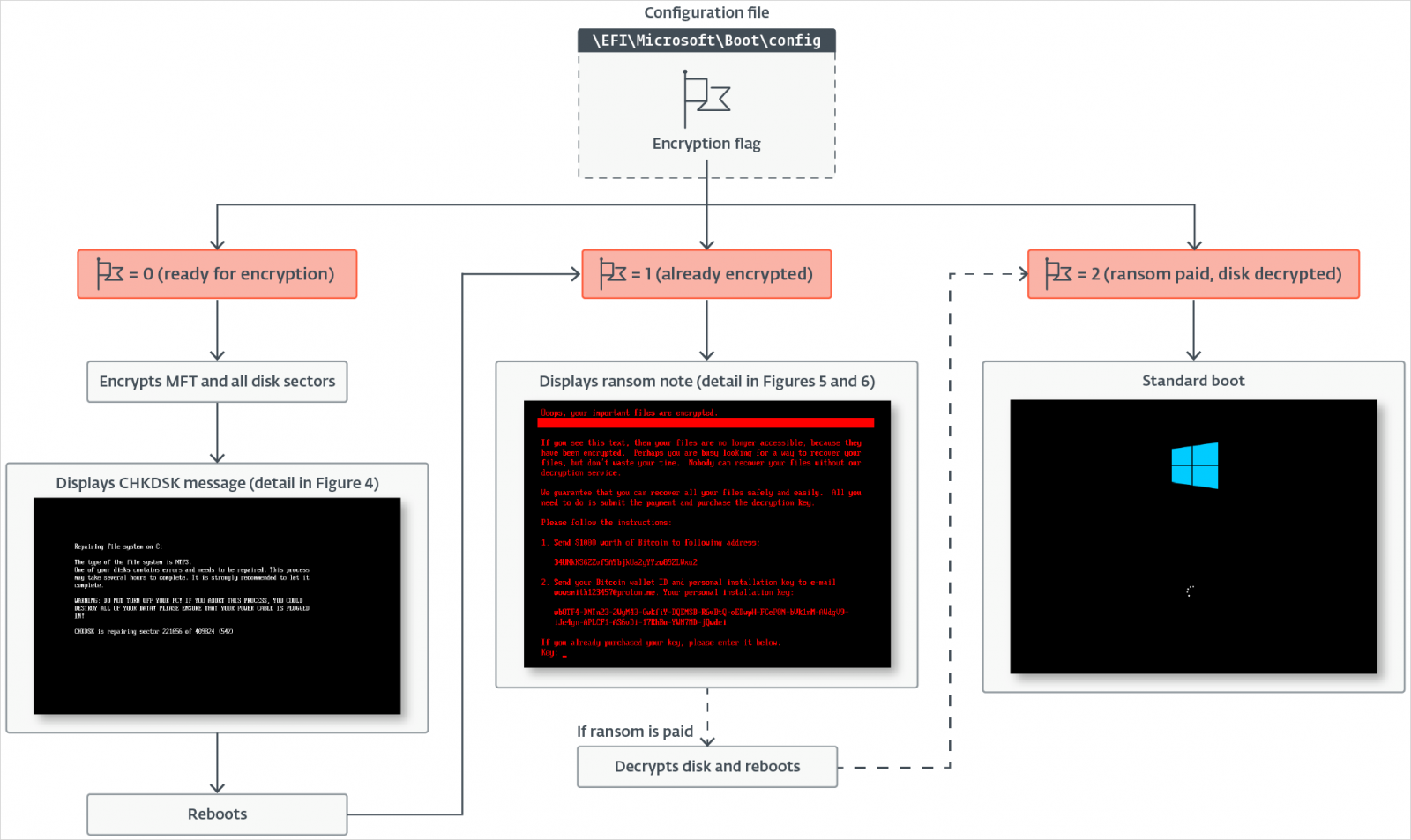
When launching, Hybridptia determines whether the host uses UEFI with GPT division and leaves a malicious bootkit in the EFI system division containing several files.
These include configurations and verification files, a modified bootloader, a follow -up UEFI bootloader, an explosive payload container and a position file that tracks the encryption progress.
The ESET lists the following files used in the analyzed variants of Hybridpetya:
- \ Efi \ Microsoft \ Boot \ Config
- \ Efi \ Microsoft \ Boot \ verified (used to validate the correct decryption key)
- \ Efi \ microsoft \ boot \ counter (progress tracker for encrypted cluster)
- \ Efi \ microsoft \ boot \ bootmgfw.efi.old (original bootloader backup)
- \ Efi \ microsoft \ boot \ cloak.dat
In addition, the malware \ Efi \ Microsoft \ Boot \ Bootmgfw.efi replaces with a weak ‘Rellow -Efi’ and removes \ Efi \ Boot \ Bootx64.efi.
The original Windows bootloader is also saved to be active in a successful restoration case, meaning that the victim paid the ransom.
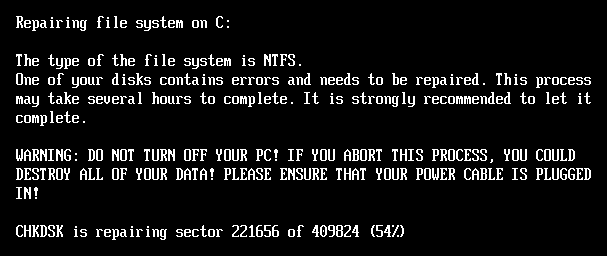
Once posted, Hybridptia displays a BSOD a fake error, as Petya did, and a system forces the reboot, allowing malicious bootkits to execute the system boot.
In this phase, the ransomware encrys all MFT clusters using a Salsa20 key and encrypse the non -extracted nonsus from the configure file when displaying fake Chkdsk messages like Notpetya.
Source: ESET
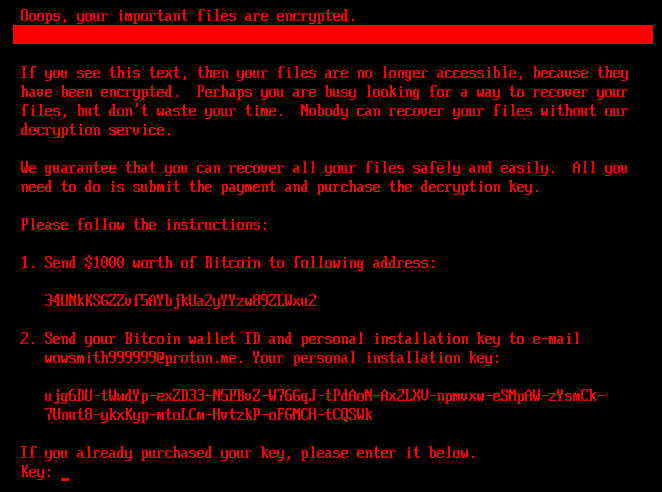
Once the encryption is completed, another reboot is triggered and the victim is served a ransom note during the system boot, seeking bitcoin payments of $ 1,000.
Source: ESET
In turn, the victim is provided a 32-ornament key that they can record on the ransom note screen, restoring the original bootloader, decrying groups, and motivating the user to reboot.
Although Hybridpetya has not been seen in any real attack in the wild, similar projects can use it in comprehensive campaigns that target POCs and target unprotected Windows systems at any time.
The agreement indicators to help protect this danger are provided on it. Jethb repository,
Microsoft set the CVE-2024-7344 with a January 2025 patch on Tuesday, so Windows systems that implement it or later are protected from security updates updated hybridptia.
Another solid exercise against ransomware is to keep the offline backup of your most important data, allowing free and easy system to be restored.



