
The Python Software Foundation has warned the victims of a new wave of fishing attacks using a fake python package index (PYPI) website to reset credentials.
S’s accessible on pypi.org, PyPI is a default source for management tools, host hundreds of thousands of packages and provide developers to distribute third-party software libraries with a centralized platform.
Python Software Foundation Developer Seth Larsen said that Fishing Email “requested” to “verify their email address” for “account maintenance and safety procedures”, threatened them with an account suspension and reproduced on a fishing landing page on the PyPI-MIRROR (.) Org.
“If you have already clicked on the link and provide your credentials, we immediately recommend changing your password on PyPI,” Larsen said“Inspection the safety history of your account for anything.
The aim of the danger actors aims to steal the credibility of the victims, which will probably be used to compromise on the packages in later attacks that they have published with malware on pipi or to publish new malicious packages.
These attacks are part of a phishing campaign, in July the Pypj (.) Organ domain was used to trick potential victims to the potential victims to log on to the fake PyPI site.
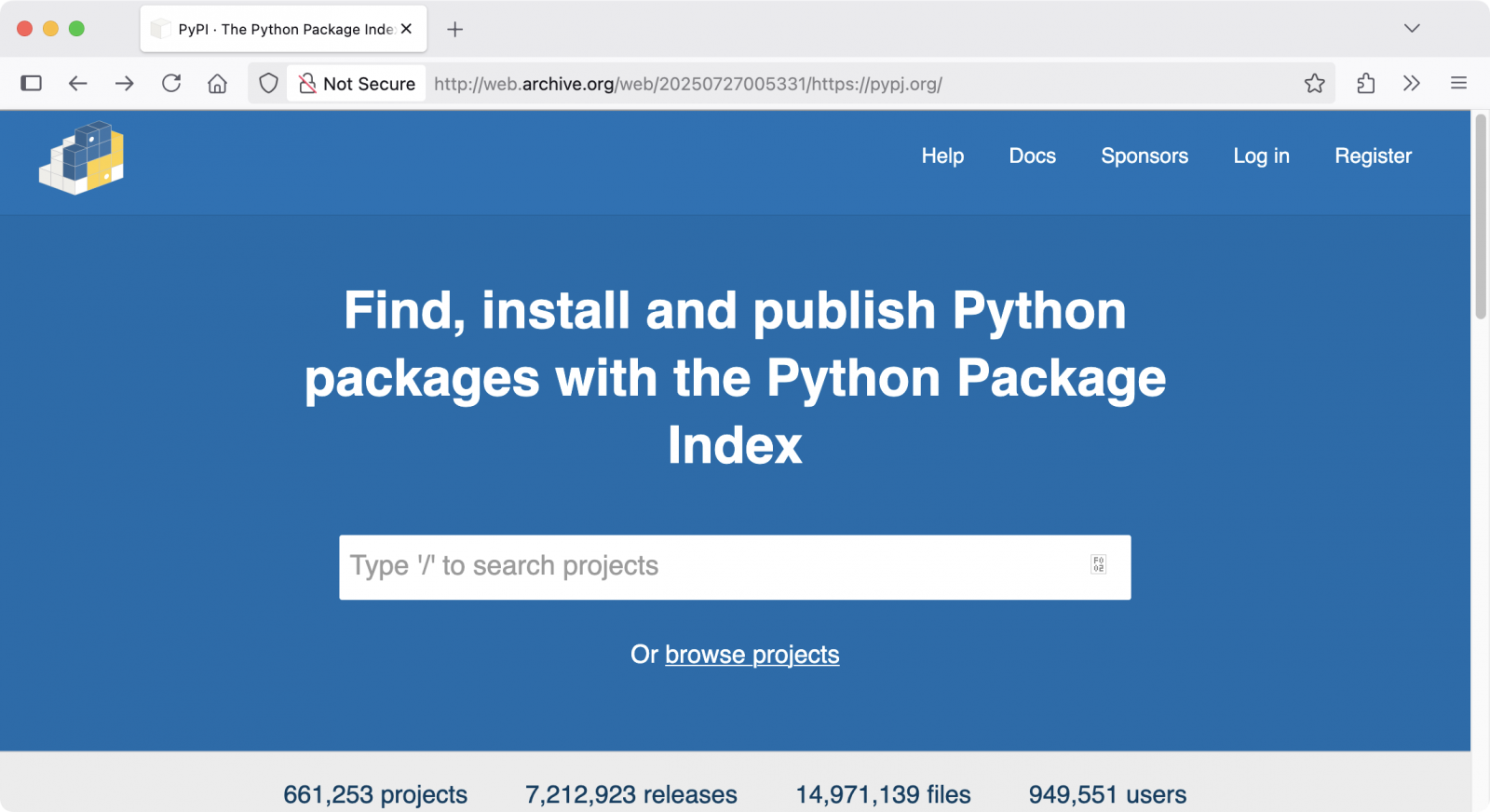
Larsen advised the maintenancers of the PyPI package to click on the link at any time and use password managers who use auto-filled credentials based on domain names.
Further to ensure that their accounts are preserved against hacking efforts, they should also use two-resistant two-factor authentication (2FA) methods such as hardware keys, and also to share suspicious emails with others before taking action.
Users can help to take these phishing campaigns down as malicious to take down these phishing operations and to remove the domains to remove the domains to contact the registrar, to block the efforts of the attackers to trick other PyPI users.
Last week, the Python Software Foundation Team also invalid all the PyPI tokens stolen in the Ghostection Supply Chain Attack in early September, confirming that the danger actors did not abuse them to publish malware.
In March 2024, PyPI also temporarily suspended user registration and new project creation, when danger actors disguised hundreds of malicious packages as valid.



