
Scan the developers system to steal two malicious packages, cryptocurrency private keys and other mysteries with about 8,500 downloads in the official crate repository of the rest.
Rust crates are distributed through a central registry Crates.ioFor JavaScript, equal to NPM, pipi for python, and ruby gem for ruby.
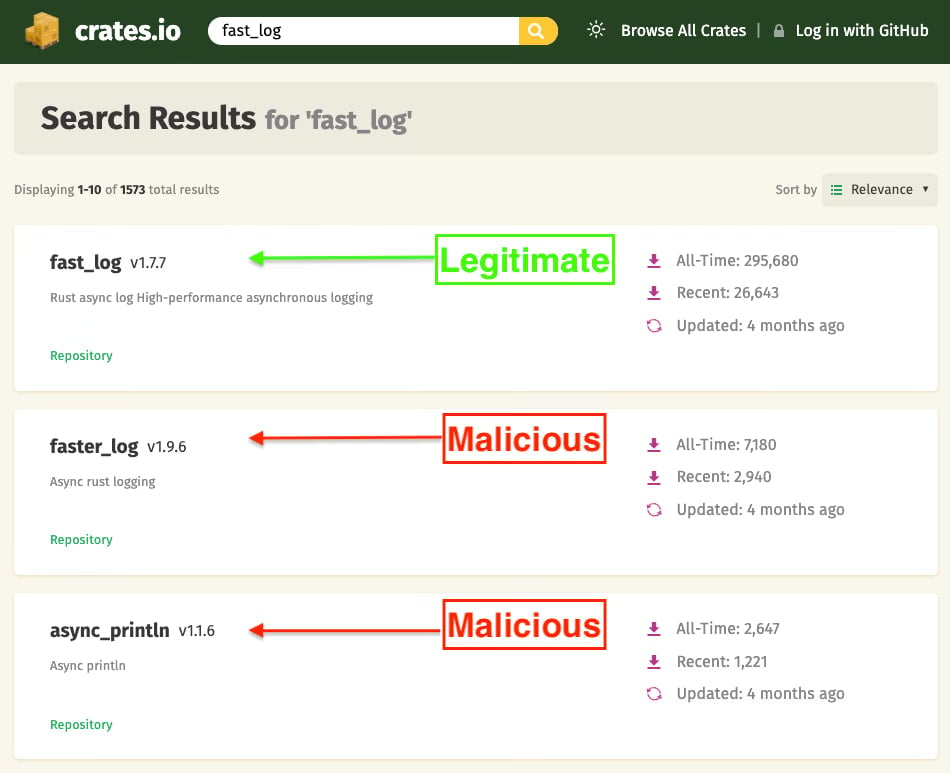
Malicious boxes, names Rapidly And async_printlnThe stage was published on the stage on 25 May and downloaded 7,200 and 1,200 times respectively.
Researchers at the Code Security Company socket discovered malicious boxes and informed them to Cret .io. The forum removed both and suspended the publication accounts, ‘Rustaguruman’ and ‘Damband’ on 24 September.
Target crypto mystery
The socket explains in one Report That two crates applied the legitimate ‘fast_log’ crate, its readme file, copying the repository metadata, and maintained the logging functionality of the real project to reduce doubts.

Source: socket
The attackers exploited log file packing functionality to scan for sensitive information.
A payload hidden in malicious boxes executed on runtime to scan the victim’s environment and project source files for the following three items types:
- Hex strings that look like atherium private keys
- Base 58 strings that resemble solana keys/addresses
- Braketed byte arrays that can hide keys or seeds
When the code was found, he tied it with a file path and line number and exformed the data on a hardcoded cloudflair worker URL address (Mennet (.) Solana-RPC-Pool (.) Labor (.) Dev,
The socket confirmed that the concluding point was live and accept the post requests during its tests, given that the host is not an official Solana RPC closing point.
Crate.io Mentioned in his announcement There was no dependent downstream crate of malicious boxes on the stage, and two banned publishers had not presented any other projects, so the attack has now been approved.
Source: socket
Developers who have either downloaded crates need to transfer their digital assets to a new wallet to clean up a system and prevent theft.
Before downloading the rust crate, developers should verify the reputation of the publisher. Another defense is re -examining the building instructions to ensure that they do not bring malicious package on their own.



