
Cyber criminals are rapidly misbehaving to produce a fishing page, malware-dropping portal and various fraud websites to create AI-operating cute website and hosting platforms.
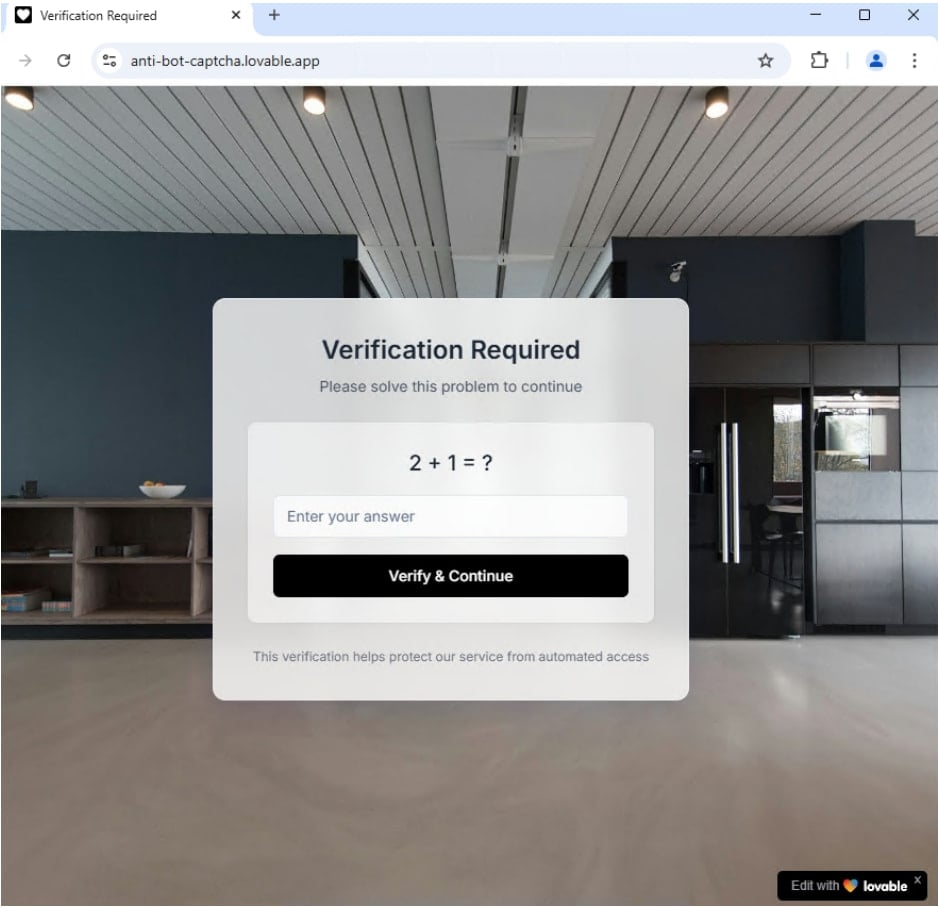
Malivedy sites created through the platform affect large and recognizable brands, and facilitates traffic filtering systems such as captcha to keep the bots out.
While Lovable has taken steps to better protect its platform from misuse, as the AI-operated site increases the number of site generator, there is a hindrance in entering cyber crime.
Source: Proofpoint
Cute-operated campaign
Since February, Cyber Security Company Proofpoint observed “tens of thousands of cute URLs”, distributed in email messages and marked as a threat.
Today in a report, researchers describe four malicious Campaigns that misused the cute AI website builder,
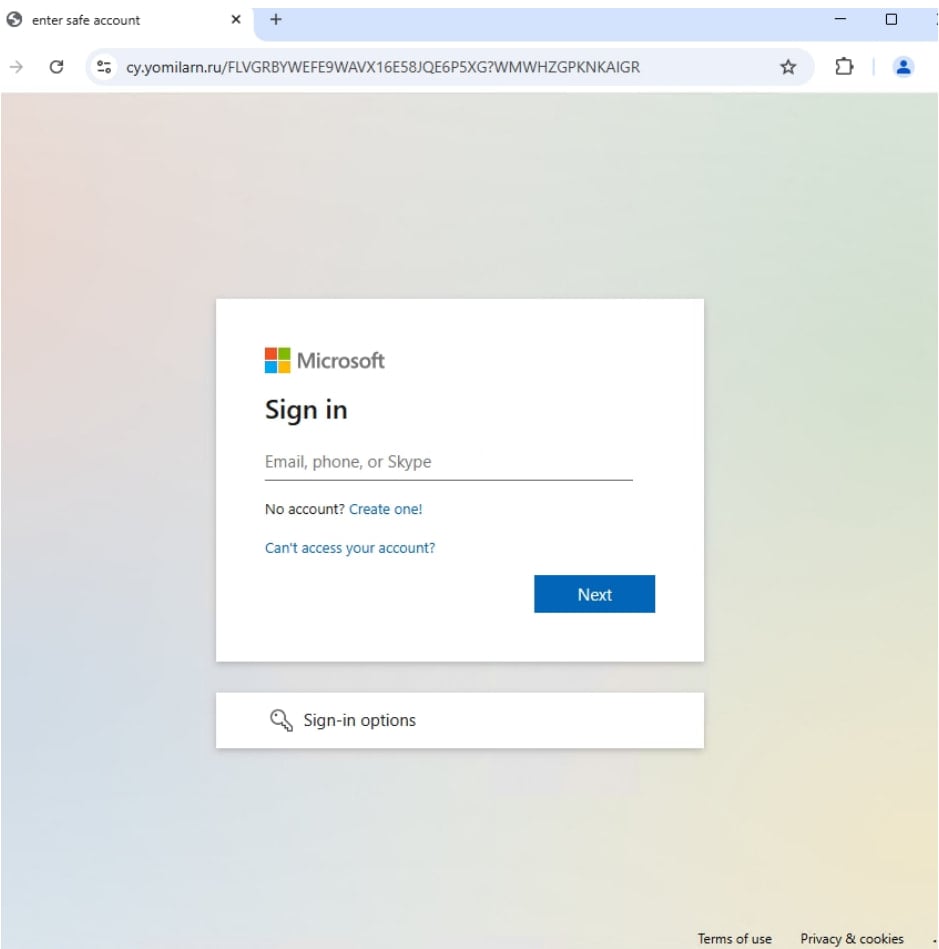
An example is a massive operation that depended on the Fish-e-Service platform known as a tycoon. The email included cute-hosted links that were opened with a captcha and then the users were redeemed to fake the Microsoft Login pages that characterized the azure advertisement or Okata branding.
These sites cut user credentials, multi-factor authentication (MFA) tokens, and session cookies through adverse-in-media techniques. During the campaigns, the threatening actor sent hundreds of messages to 5,000 organizations.
Source: Proofpoint
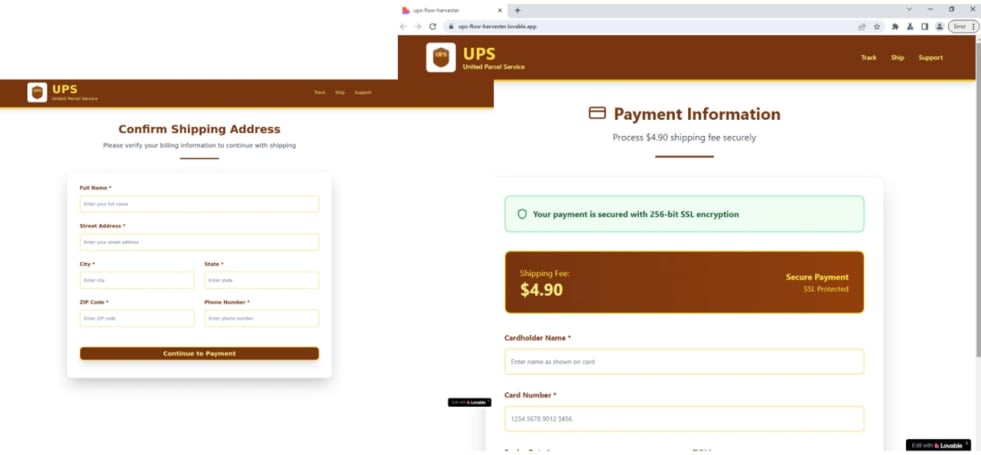
Another example was a payment and data theft campaign, which implemented UPS, who used to send about 3,500 fishing emails, directing the victims to the fishing sites.
The sites asked visitors to enter individual details, credit card numbers and SMS codes, which were then sent to the Telegram channel controlled by the attacker.
Source: Proofpoint
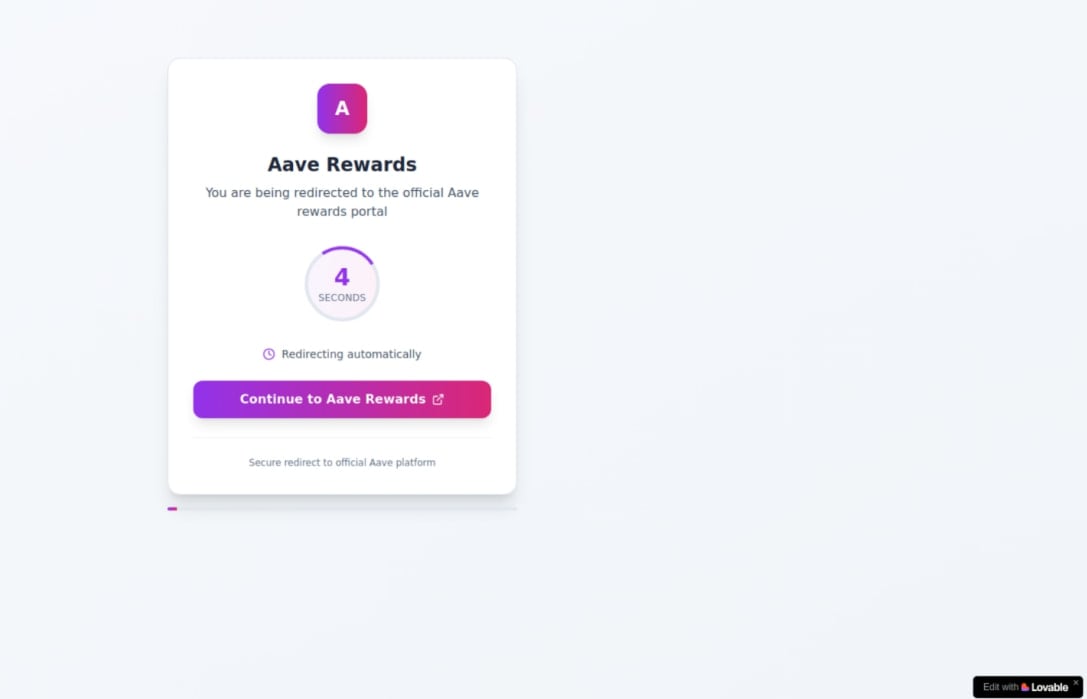
The third is a cryptocurrency theft campaign that implemented the Defi platform aave, sending 10,000 emails through Sendgrid.
The targeted users were led to the cute-generated redirect and fishing pages, designed to prepare them to add their purse, possibly after asset drainage.
Source: Proofpoint
The fourth case worries about a malware delivery campaign distributed to the remote access Trojan Zagrat.
The email consists of links that pose cute apps in the form of invoice portals, which distributed to the RAR archives hosted on the dropbox.
A valid signed executable in the files was launched with a trounted DLL -the duelider was launched, which eventually loaded the ZGRAT.
Reply
Lovable explored real -time of malicious site building in July, and scanned the projects published daily to spot and remove any fraud attempts.
The developer also said that it is planning to provide additional protection to this decline, which would identify and block out derogatory accounts on the platform.
Guardio Labs confirmed the Blapping computer that Luvbal could still be used to create malicious sites. In a recent test, researchers generated a fraud site to implement a large retailer and did not object from the stage.
Bleepingcomputer has contacted Lovable to ask about the effectiveness of existing anti-abusive measures on the platform, but a comment was not immediately available.



