
Researchers have disrupted an operation responsible for the Russian state-proposed threat group Midnight Blizard, seeking access to Microsoft 365 accounts and data.
Also known as APT29, the hacker group in a watering hole campaign enrolled the websites to redirect the targets “Microsoft’s device coded in a watering hall campaign compromised for the malicious infrastructure designed to authorize the attacker-controlled equipment through authentication flow.”
The Midnight Blizzard Threat actor has been linked to Russia’s Foreign Intelligence Service (SVR) and is well known for its clever fishing methods, who have recently influenced European Embassy, Hewlet Packed Enterprises and Teamviewer.
Random selection
Amazon’s threats discovered the domain names used in the Watering Hole campaign after creating an analytical for the infrastructure of APT29.
An investigation revealed that hackers had compromised several legitimate websites and disrupted malicious code using Base 64 encoding.
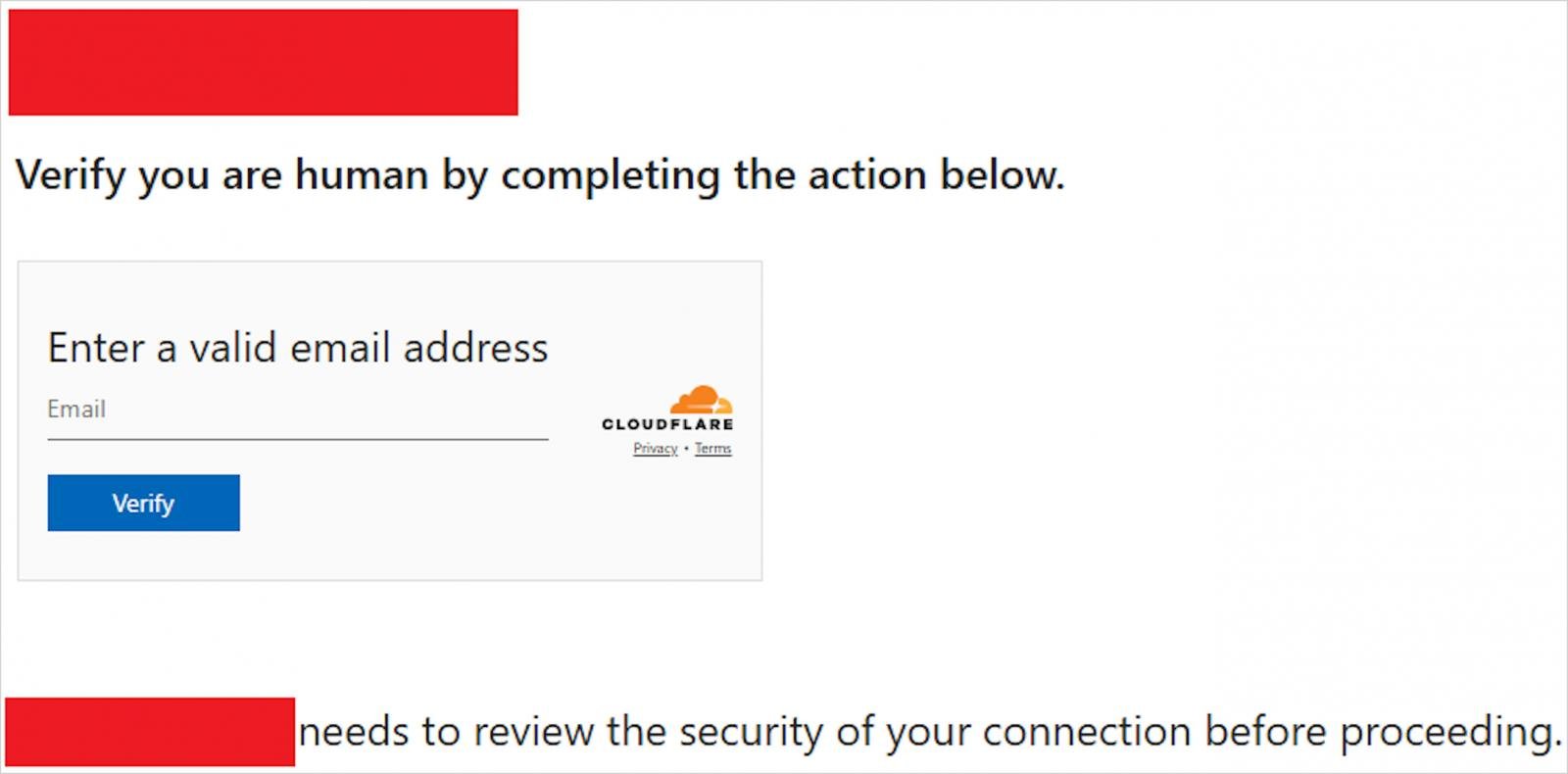
Using randomization, APT29 for approximately 10% of the domains of the visitors of the compromised website that mimics cloudflair verification pages Findcloudflare (.) Com Or Cloudflare (.) Redirectpartners (.) Com,
.jpg)
Source: Amazon
Amazon as Tells in a report On recent action, the danger actors used a cookies-based system to prevent the same user from being redirected several times, which reduced doubts.
The victims who landed on the fake cloudflare pages were directed to a malicious Microsoft device code authentication flow, which attempts to authorize them-invasive devices.
Source: Amazon
Amazon notes that the campaign was once discovered, its researchers separated the EC2 examples, used to a danger actor, which participates to disrupt the domain identified with cloudflair and Microsoft.
Researchers noticed that APT29 tried to transfer its infrastructure to another cloud provider and register new domain names (eg) Cloudflare (.) Redirectpartners (.) Com,
Amazon Chief Information Security Officer CJ Musa says that the researchers continued to track the actor’s movement and disrupted the attempt.
Amazon underlines that this latest campaign reflects a development for APT29 for the same purpose of collecting credentials and intelligence.
However, there are “refinery to their technical approach”, which no longer rely on domains that attempts to bypass APS or social engineering multi-factor authentication (MFA), which by tricking the goals in creating an app-specific password.
Users are recommended to verify the device authority requests, enabling multi-factor authentication (MFA), and avoid executing commands on their system copied from webpages.
Administrators should consider disabled of unnecessary device authority defects, where possible, apply conditional access policies, and closely monitor for suspected authentication events.
Amazon stressed that this APT29 campaign did not compromise on its infrastructure or affected its services.



