
Two new spyware expeditions that researchers lured the prosy and toes to steal sensitive data to Android users with fake upgrade or plugins with fake upgrade or plugins.
To give a sense of validity to malicious files, the danger actor distributed them through websites that transplicated two communication platforms.
The signal is a popular end-to-end messenger with more than 100 million downloads on Google Play.
Totok has been developed by the UAE-based Artificial Intelligence Company G42 and was excluded from Apple and Google App Stores in 2019 following allegations of being a detective equipment for the United Arab Emirates government.
Currently, Totok is available for download from its official website and third-party app store.
Silent and firmness
Researchers at Cyber Security Company ESET discovered the prosy campaign in June, but believe that the activity could begin at least 2024. Based on their analysis, the malicious campaign is targeting users in the United Arab Emirates.
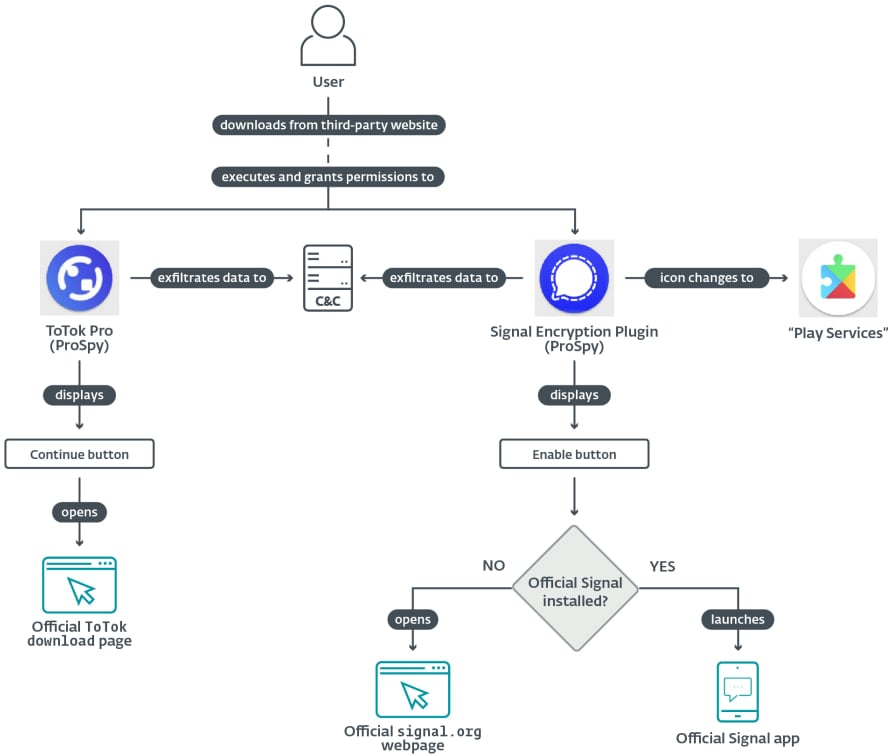
During the investigation, he discovered “two pre -specified spyware families”, pretending to be a pro -variant of a signal encryption plugin and Totok app, none of which are present.
The operator of the spyware campaign distributed malicious APK files through web pages, which implemented the official signal website (https: //signal.ct (.) WS And https: //encryption- plug-n-signal.com-aE (.) Net/) And Samsung Galaxy Store (store.Latestversion (.) AI And https: //store.appupdate (.) AI,
Source: ESET
Bleepingcomputer tried to reach the website of fraud, but most of them were offline and were redirected to an official Totok website.
When executed, samples of Prospy malware request access to contact list, SMS and files, which are specific permissions for the Messenger app.
Once activated on the device, the malware exfers the following data:
- Device information (hardware, operating system, IP address)
- Stored SMS texts, contact list
- Files (audio, document, picture, video)
- Totok backup files
- List of installed applications
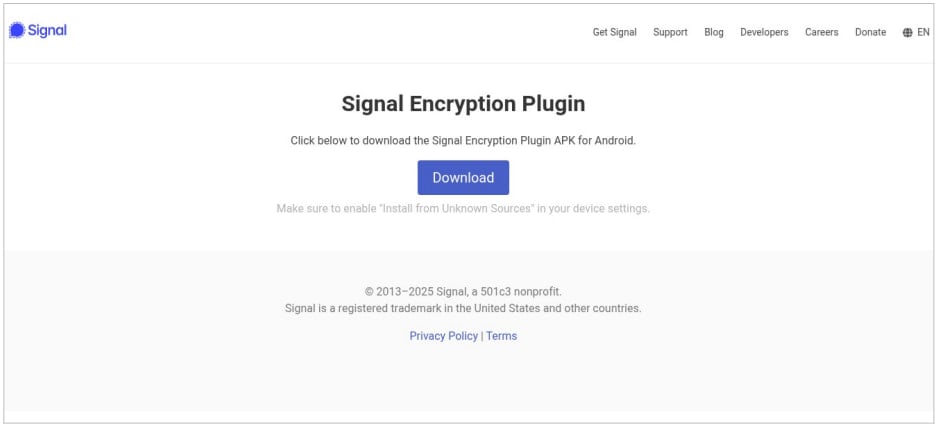
To stay hidden, the signal encryption uses ‘play services’ icons and labels on the plugin home screen. In addition, the screen will open the information of a valid Google Play service app while tapping the icon.
The diagrams below explain how a prospace agreement works. The danger tried to avoid increasing the user’s suspicion by redirecting them on the official download site when the valid app disappeared on the device.
Source: ESET
TOSPY campaign may be generated in 2022
According to research, the TOSPY campaign is still ongoing, based on the active condition of the command-end-control (C2) infrastructure.
The ESET notes that this activity may be behind as 2022, as they pointed to that period and found several indicators: May 24, 2022, a developer certificate made on May 24, 2022, the distribution of registered distribution and domain used for C2 on 18 May that year, and the samples uploaded on the wirestotle scanning platform on 30 June.
Source: ESET
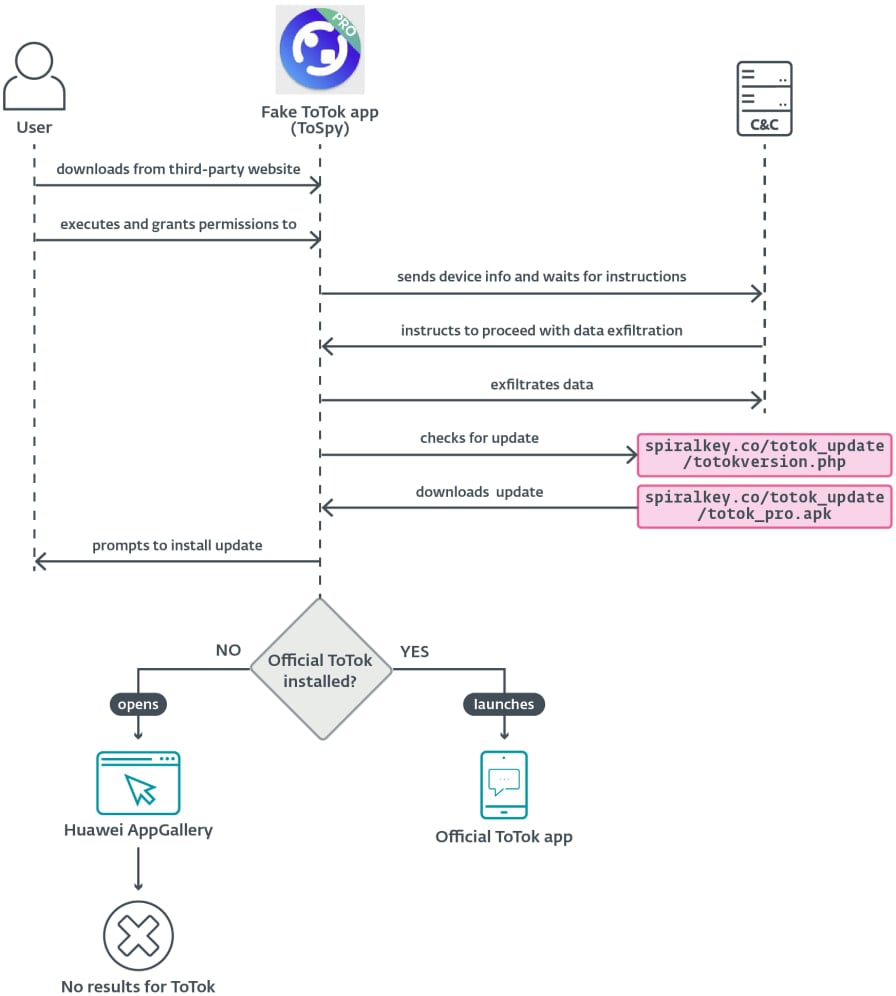
The fake totoque app distributed in this campaign motivates victims to give contact and storage access permissions, and collects related data, focuses on documents, images, videos, and totoque chat backup (.ttkmbackup files).
The ESET report stated that all exfiltrated data has been encrypted using the AES symmetrical encryption algorithm in the first CBC mode.
For Chupke, Tospy launched the Real Totok app when it was opened, if it is available on the device.
If the app is not present, the malware tries to open the Malware Huawei Appgallery (either a valid app or default web browser) so that the user can get the official totoque app.
Source: ESET
Both spyware families use three perseverance mechanisms on infected equipment:
- If killed when killed automatically, ‘alarmmanager’ misuse of Android System API.
- Use a foreground service with frequent notifications so that the system considers it as a high-ethics process.
- Register to achieve boot_completed broadcasting events so that it can restart spyware on the device reboot without user interaction.
ESET shared a comprehensive list Compromise indicators ,
Android users are recommended to download the app only from official or reliable repository, or directly from the publisher’s website. They should keep the play protect service active on their device to disable already known dangers.



