
A weakness in Apple’s Safari web browser allows danger actors to avail fullscreen browser-in-a-mid-middle technology so that they can steal account credentials from unheal users.
By misusing fullscreen API, which instructs any material on a webpage to enter the browser’s fullscreen viewing mode, hackers can exploit a decrease in chromium-based browsers and trick victims to decrease in typing sensitive data in an attacker-controlled window.
Squarex researchers used this type of malicious activity and said that such attacks are particularly dangerous for safari users, as Apple’s browser fails to consume users properly when a browser window enters fullscreen mode.
“Squarex’s research team has seen several examples of the browser’s fullscreen API, which has been exploited to address this defect by displaying fullscreen bitmal window, which covers the address bar of parent window, as well as a limit for safari browsers that specially assures the fullscreen bitter attacks,” Describes the report,
How the bite works
A common Bitm attack shows a valid login page that includes users in interaction with an attacker-controlled distance browser. It is obtained through devices such as Novnc – an open -Source VNC browser client, which opens a remote browser at the top of the victim’s session.
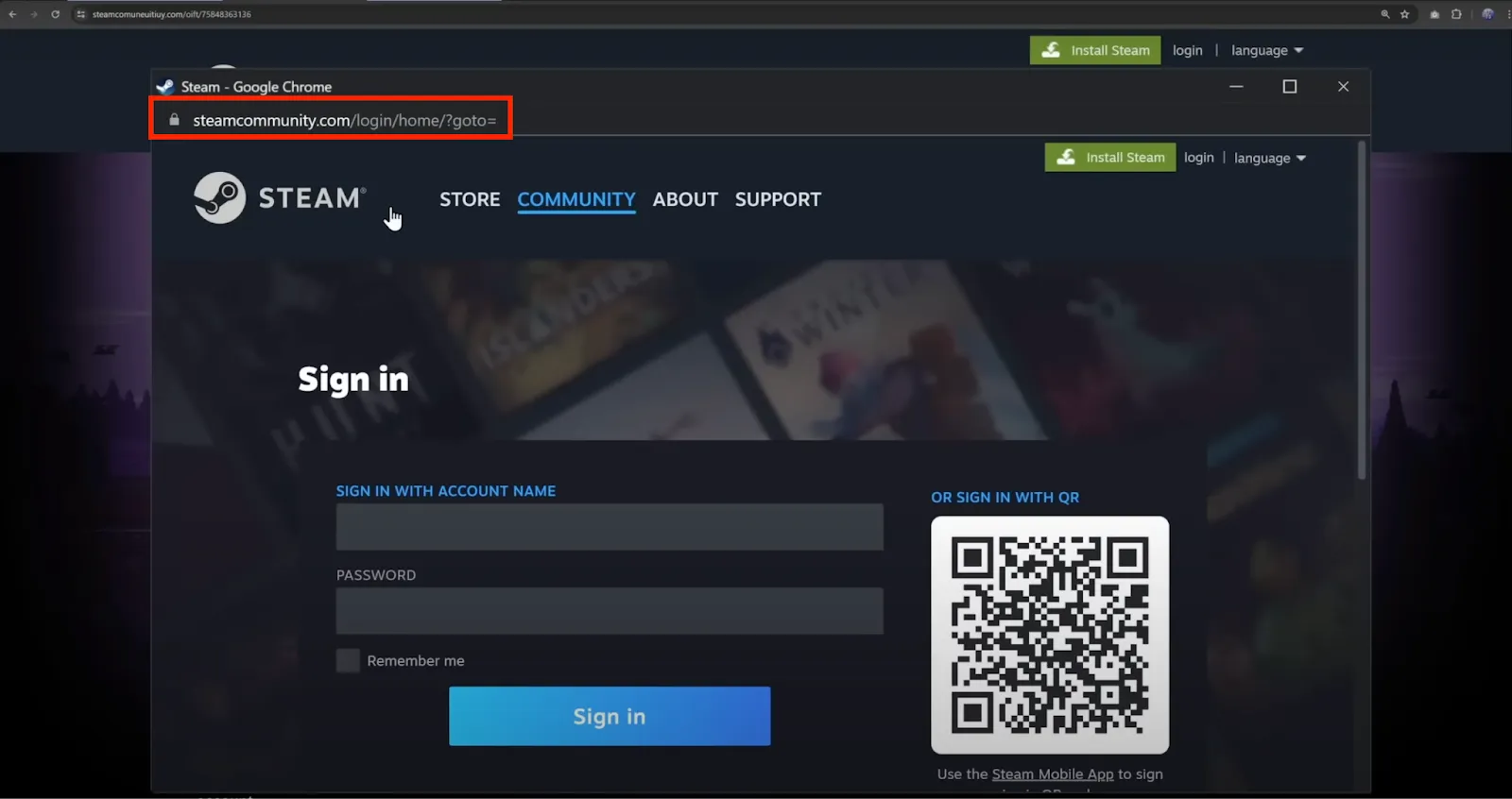
Source: Squarex
Since the login process occurs in the browser of the attacker, credentials are collected, but the victim also successfully access his account unknown to theft.
In the attack, the victim still needs to click on a malicious link that redirects them to a fake site that applies the target service. However, it can easily be obtained through advertisements sponsored in web browsers, social media posts, or comments.
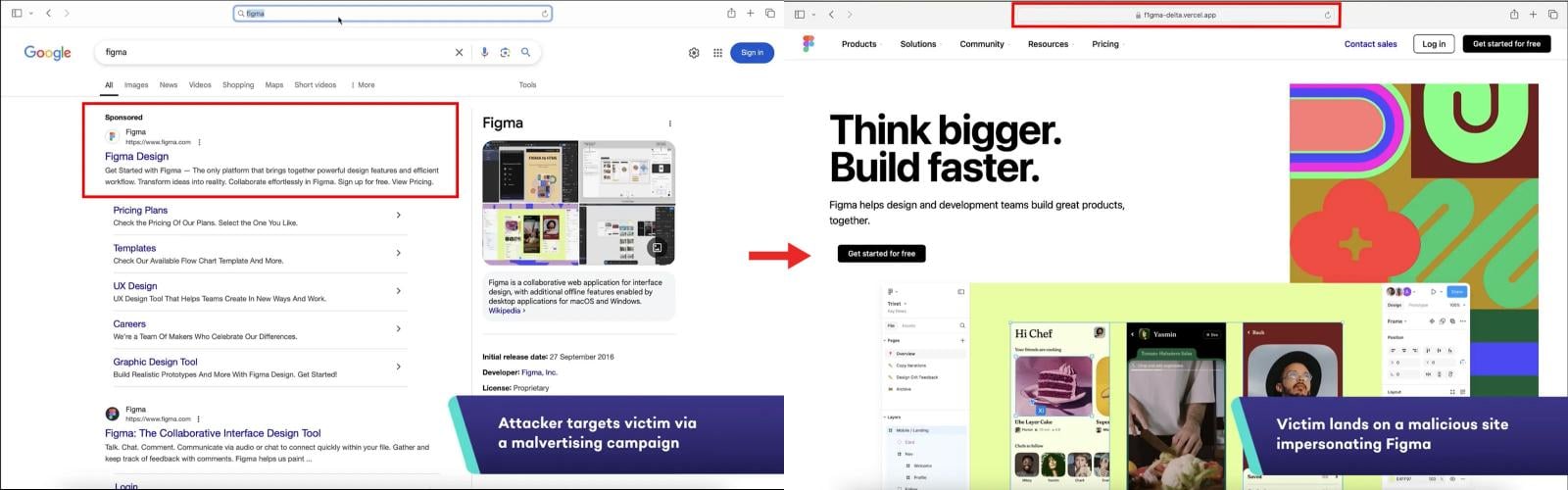
Source: Squarex
Fulscreen deception
If the users recall the suspected URL in the browser bar and click on the login button, the BITM window becomes activated. Till the trigger, the window was hidden from the victim in minimal mode.
If the users recall the suspected URL in the browser bar and click on the login button, which activates the bitmal window that was hidden in the minimum mode from the victim.
Once active, the attacker-controlled browser window enters the fullscreen mode and covers the fake website, which wanted to reach the valid website to the user.
Security solutions like EDRS or SASE/SSE will not trigger any warnings if this happens, as the attack abuses standard browser API.
Researchers suggest that firefox and chromium-based browser (eg chrome and edge) whenever fullscreen is active, shows alerts. Although many users can recall warnings, it is still a railing that reduces the risk of the bitmal attack.
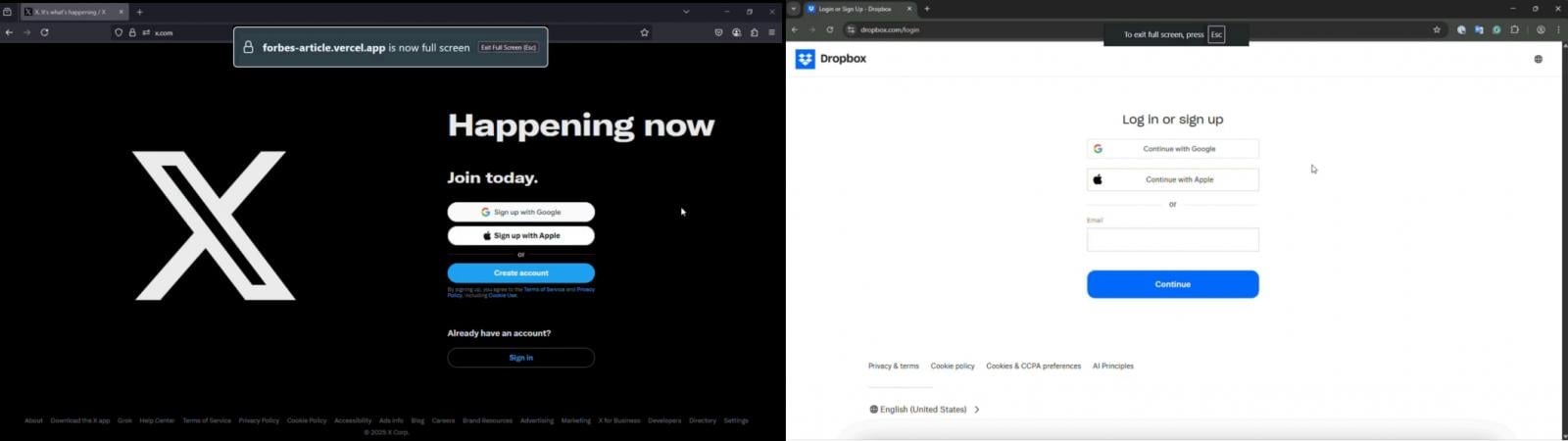
Source: Squarex
However, there is no alert on the safari and the only sign of a browser entering fullscreen mode is a “swipe” animation that can be easily remembered.
Squarex researchers say, “While the attack works on all browsers, the fullscreen bite attacks are reassured due to the lack of clear visual signals, especially on the safari browsers.”
https://www.youtube.com/watch?v=9c4jrabg2cy
Squarex approached Apple with its findings and received a “wontfix” answer, obtained clarification that animation is present to indicate changes, and it should be enough.
Bleepingcomputer has also reached Apple for a comment, but we are still waiting for their response.



