
The Russian state-proposed danger group Apt28 is using signal chat to target government goals in Ukraine, which is called Beardshel and Slimzant with two already unspecified malware families.
To be clear, this is not a security issue in the signal. Instead, the danger actors are more commonly using messaging platforms as part of their fishing attacks because due to its increased use by governments worldwide.
The attacks were first discovered by Ukraine’s computer and emergency response (authentication required) In March 2024, although limited details about the transition vector were exposed at that time.
A year later, in May 2025, ESET informed the certified-UA of unauthorized access to a Gov.UA email account, inspiring a new event response.
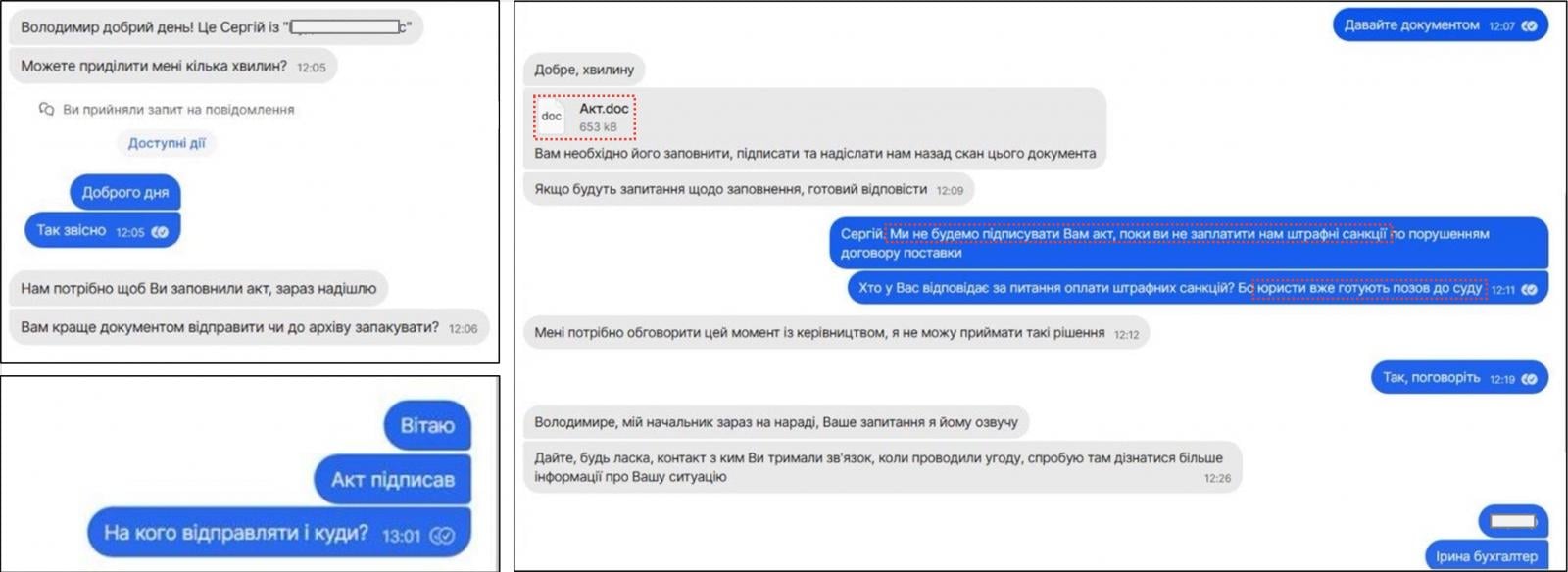
During this new investigation, CERT-UA found that messages sent via the encrypted messenger app signal were used to give a malicious document for the target (акт.doc), which uses the macro to load the Memory-Rejidant Backdor called Covenant.
Source: Certificate-UA
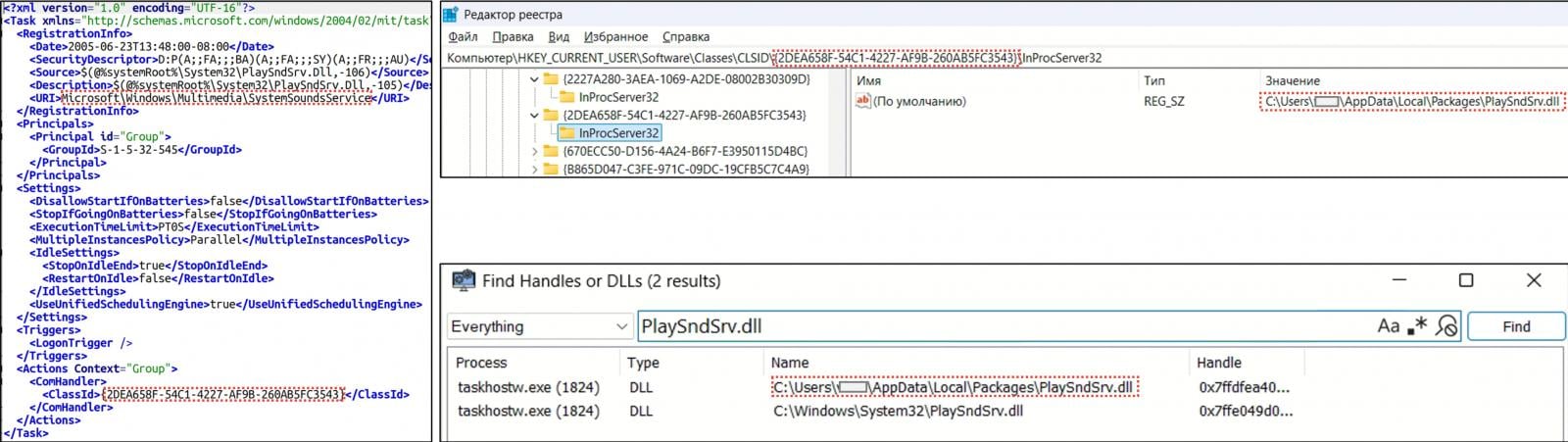
The coven acts as a malware loader, downloads a DLL (playsndsrv.dll) and a shellcode-ride WAV file (sample-03.wav), which loads the pre-specified C ++ malware.
For both loader and primary malware payload, firmness is secured via com-Hijacking in the Windows Registry.
Source: Certificate-UA
The main functionality of Beardshell is to download the Powershell script, decrypus them using ‘Chacha20-Poly1305’, and execute them. The execution results are attached to the command-end-control (C2) server, with the communication with the convenience by the ICEDRIVE API.
In 2024 attacks, Certificate-UA also saw a screenshot Graber called Slimagant, which uses an analysis of Windows API functions (enumdisplaymonitors, createcompatibledc, createcompatibitbitmap, createcompatibitbitmap, bitblt, gdpsaveimagetostram) Capture the screenshot.
Those images are encrypted using AES and RSA, and locally stored, possibly exflated by a separate payload/tool for the C2 server of APT28.
CERT-UA credits this activity for APT28, which they track as UAC -0001, and recommend that potential targets monitor network interactions with app.koofr.net and api.icedrive.net.
Apt28 has a long history of targeting other major organizations in America and Europe along with Ukraine, mainly for cyberpation.
They are one of the most advanced danger groups in Russia, exposed by Ovelexity to use a novel “nearest neighbor” technology in November 2024, which violated the targets from distance by exploiting the nearby Wi-Fi network.
In 2025, the hint unexpectedly became central for cyber attacks associated with Russia and Ukraine.
The popular communication platform has been abused in the javelin-fishening attacks, which misuses the device-linking facility of the platform in the distribution of kidnapping accounts and dark crystal rats against major goals in Ukraine.
At some point, representatives of the Ukraine government Expressed disappointment That sign stopped cooperating with him in an attempt to block Russian attacks. Ukrainian officials later voiced disappointment over the lack of cooperation of the signal in blocking Russian operations.
However, the president of the signal, Meerdith Whitekar That claim was surprisedSaying that the platform has never shared communication data with Ukraine or any other government.



