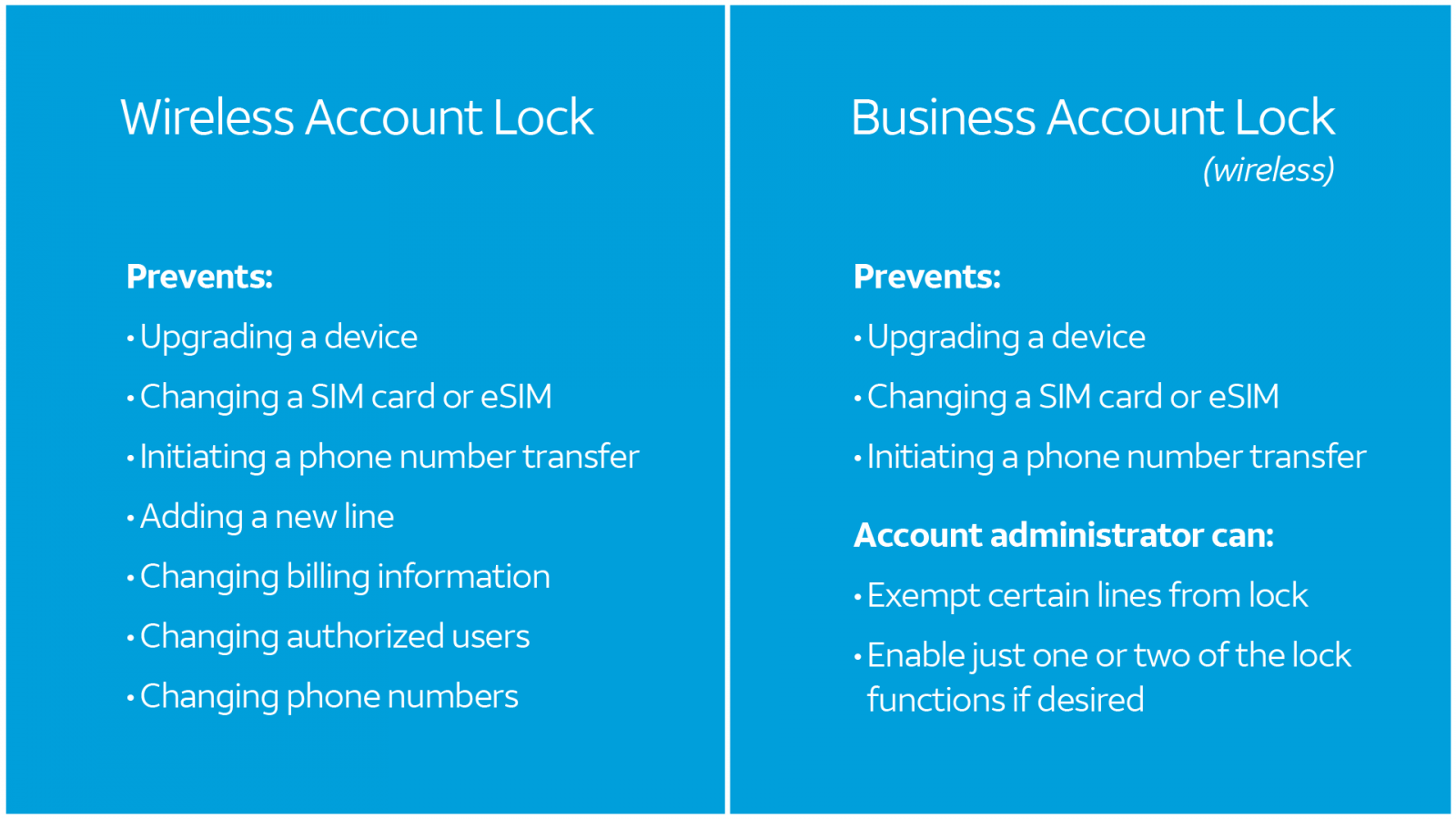
AT & T has launched a new security facility called “wireless lock” that prevents customers from changes in their account information and SIM swapping attacks while stopping the phone number porting, while the facility is enabled.
This new feature is available for some customers for about a year and is now rolled out to all AT and T customers.
SIM swap attacks occur when cyber criminal port, or move, a target phone number on a device under their control. This allows them to disrupt the target calls, texts and multi-factor authentication code to dissolve further accounts, such as email, banking and cryptocurrency wallets.
In some cases, actor of danger conducts the SIM swap attacks by transferring telecom employees to transfer the number from customers’ SIM card to a new device or by bribing.
with New AT and T featureCustomers can log in to “lock” their number on the company’s mobile app or website, anyone, including AT & T employees, can prevent the number from porting to a new SIM card or transfer to another provider until the setting is incompetent first.
This feature also protects other types of information, such as changing billing information, changing authorized users and phone numbers. Professional accounts receive additional features, which include the ability to exempt some lines from lock or restrained specific account changes when capable.
Source: AT & T
Although it is good to see that AT&T finally released this feature, it comes late, other carriers, such as Verizon, have done it for about 5 years.
The SIM swap attacks have been linked to several security incidents in the last five years.
In 2020, Joseph James O’Coner, aka ‘plugwalkjok’, convicted the SIM swap attacks, resulting in a $ 794,000 stolen in Cryptocurrency.
In 2021, T-Mobile warned some customers that the attackers organized the SIM swap attacks, which were to compromise on other accounts owned by them. In 2023, hackers exploited a data breech in Google Fi to swap sim.
The danger actors, like the scattered spider -associated people, have been charged in the US to use SIM swaps to infiltrate the corporate network.
Other recent attacks include the ESIM kidnapping campaign where criminals activated the electronic SIM on the names of the victims to seize the control of numbers.
However, it is not always a third-party hackers who conduct SIM swap attacks.
Last year, Verizon and T-Mobile Employees began to receive their personal and work on the phone, trying to bribe them with $ 300 to swap SIM.
In 2023, FCC adopted new rules for the need for strict identity verification during SIM swap and number transfer.



