China-based purveyors of SMS Fishing Kit are enjoying remarkable success. Apple And GoogleUntil some time ago, so -called “to harass“Mainly toll road operators and shipping companies have been implemented. But experts say that these groups are now targeting customers from international financial institutions, while dramatically expanding their cybercrime infrastructure and support staff.

An image of an iPhone device form was shared by one of the tried members shared on Telegram. Picture: Prodaft.
If you are the owner of a mobile device, the possibilities are excellent that in the last two years at some point you have found at least a quick message that warns a criminal toll road fee, or a free package from American Postal Service (USPS). Those who click on the promoted link are brought to a website that spoils the USPS or a local toll road operator and asks for the payment card information.
The site will then complain that the visitor’s bank needs to “verify” the transaction by sending a code through SMS. In fact, the bank is sending that code to the mobile number on the file for its customer as the fraudsters have tried to nominate the victim’s card details in the mobile wallet.
If the visitor supplies the code once, their payment card is then added to a new mobile wallet on an Apple or Google device that is physically controlled by fishers. Fishing gangs usually load several stolen cards in a digital wallet on a single Apple or Android device, and then sell the phones to scammers in bulk that use them for fraud e-commerce and tap-to-pe-pay transactions.
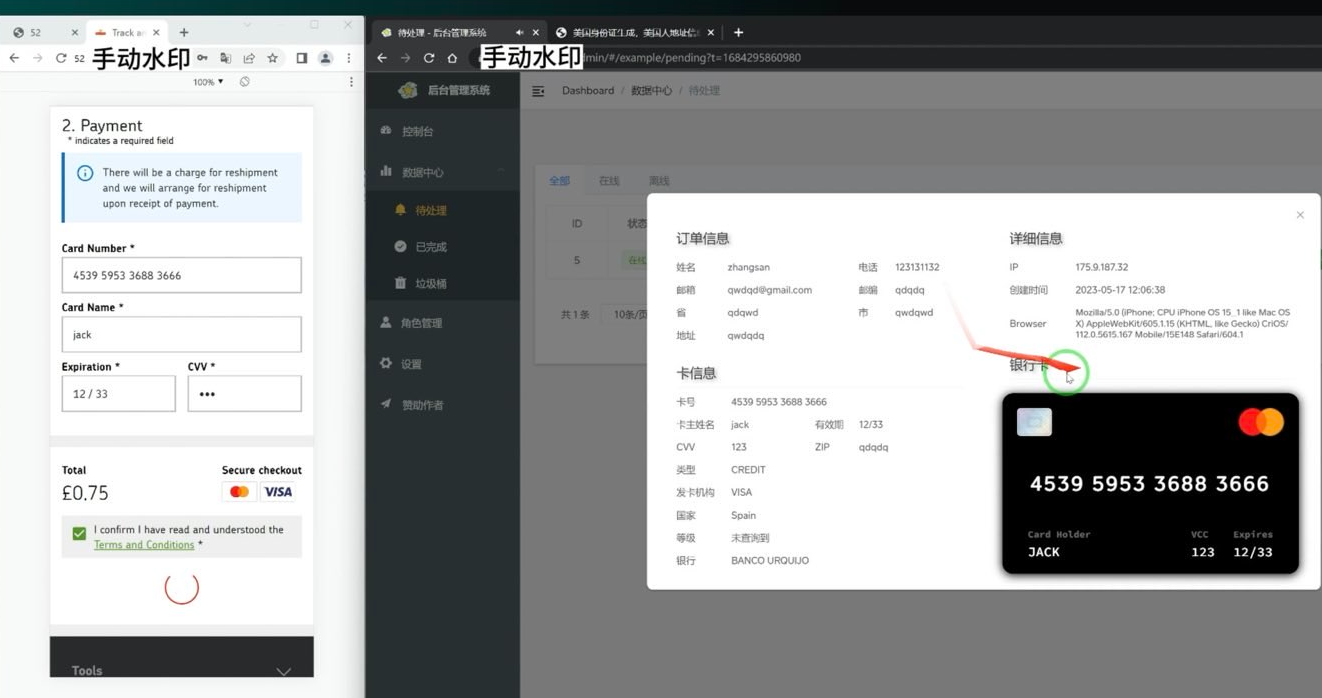
A screenshot of the administrative panel for a smoching kit. On the left, there is (test) data recorded on the fishing site. On the right, we can see that the fishing kit has superpreted the card number supplied on the image of the payment card. When the fishing kit created the image of the card in Apple or Google Pay, it triggers the victim’s bank to send a bar code. Picture: Ford Merryl.
Monikar comes from “Smoing Triad” ReconsiderationWhich was among First to report in August 2023 On the emergence of three separate mobile fishing groups in China, which appeared sharing some infrastructure and innovative phishing techniques. But this is a false name because the fishing lews exploded by these groups do not have SMS or text messages in the traditional sense.
Rather, they are sent through IMESSAGE To Apple Device user, and through RCS Google Android equipment. Thus, missiles completely bypass mobile phone networks and enjoy 100 percent delivery rate (at least until Apple and Google Spamy suspends accounts).
In a report Published on 24 March, The Swiss Threat Intelligence Firm Male Extend the rapid pace of innovation coming from smoothing tride, with names such as a lax union group of Chinese phishing-e-servis operators. Darwla, LightAnd this Zinxine group,
Prodaft stated that they are seeing a significant change in the underground economy, especially among Chinese speaking danger actors who are historically operated in shadow compared to their Russian -speaking counterparts.
“Chinese -speaking actor is starting innovative and cost -effective systems, enabling them to target large user base with refined services,” Proudaft wrote. “His approach marks a new era in underground trade practices, emphasizing scalability and efficiency in cyber criminal operations.”
A New report From researchers in security firm Silypush Smishing Triad members have expanded to sell mobile fishing kits targeting customers from global financial institutions City group, Master card, Papail, stripAnd VisaAlso banks in Canada, Latin America, Australia and the widespread Asia-Pacific region.

Fishing Triall Spufing Paple from Fishing Lers. Picture: Silentpash.
Silentpash found that smoothing trident now spoils identified brands in various types of industries in at least 121 countries and a large number of industries, including postal, logistics, telecommunications, transport, finance, retail and a large number of industries.
According to silentpash, the domains used by Smuthing Triad are often rotated, about 25,000 fishing domains are activated during any 8-day period and most of them are sitting in two Chinese hosting companies: Tencent (As132203) and Alibaba (As45102).
Silentpush wrote, “Triads targeted by almost two-thirds countries of the world have been targeted, it is safe to say that they are essentially targeting every country with modern infrastructure outside Iran, North Korea and Russia.” “Our team has observed some possible targeting in Russia (such as domains that refer to their country code), but anything sufficiently enough to indicate Russia is a continuous goal. Interestingly, interestingly, even though these Chinese threats are actors, we have seen the examples of targeting in both specialized administrative areas of Macau and Hong Kong, China.”
Silent Zach Edwards It is said that his team found a vulnerability, in which data was exposed from one of the phishing pages of the sminging trident, which revealed the number of each day receiving each day in thousands of phishing domains that were activated at that time which were active at that time. Depending on that data, silentpash estimates that those fishing pages received more than one million trips within 20-day time.
The report stated that the Sminging Triad claims that it has a “300+ front desk staff worldwide” which is included in their more popular fishing kit-lighthouse-staff, mainly used to support various aspects of group fraud and cash-out schemes.
Sming Triad Members maintain their own Chinese -language sales channels on Telegram, who often work hard at work of their employees and photos of their employees. Some of those images include huge walls of the phone used to send a fishing message, in which human operators are sitting directly in front of them, which are ready to get any time-sensitive one-time code.
As mentioned in the February story of the February, how fish data turns into Apple and Google Wallet, one of those cash-out plans includes an Android app called called. Z-NFCWhich can relay a valid NFC transaction from one of these compromised digital wallets anywhere in the world. For a $ 500 -month subscription, the customer can wave his phone at any payment terminal that accepts Apple or Google Pay, and the app will relay the NFC transactions on the Internet from a stolen wallet on a phone in China.
https://www.youtube.com/watch?v=ekqzjpaxb4c
Chinese citizens were recently trying to use these NFC apps to buy high end electronics in Singapore. And in the United States, California and Tennessi officials arrested Chinese citizens accused of using NFC apps to buy gift cards from retailers.
Prodaft researchers said they were able to find the previously unspecmik backnd management panels ObviousA Smothing-e-Service Operation is associated with the Zinxine Group. The panel included the victim’s figures that suggest that the smoching campaign maintains an average success rate of about five percent, with some domains receive more than 500 trips per week.
“In an observation example, a single phishing website captured 30 credit card records from 550 aggrieved interactions during the 7-day period,” Wriended.
Prodout’s report shows how Smishing Triad has achieved such success in sending its spam messages. For example, a phishing seller appears to send a message using dozens of Android devices running parallel on a machine.
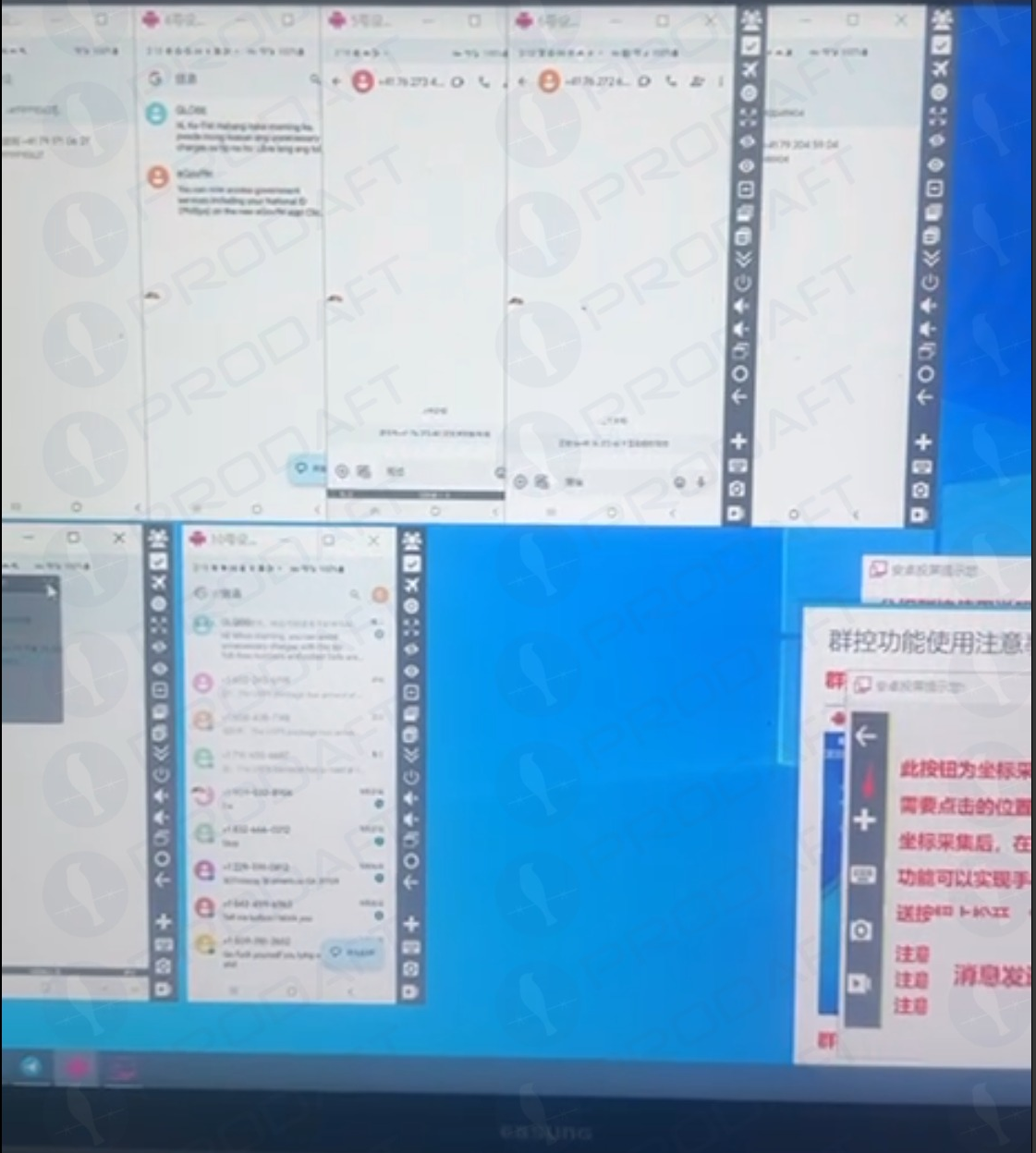
Fisters using several virtuous Android devices to orchestrate and distribute RCS-based scam campaigns. Picture: Prodaft.
According to Proudaft, the danger actors first get phone numbers through various means including data violations, open-sources intelligence, or lists purchased from underground markets. They then take advantage of technical intervals in sender ID verification within both messaging platforms.
“For IMESSAGE, it involves creating temporary apple ID with impering display names, while RCS exploitly takes advantage of carrier implementation discrepancies in verification,” Prodaft wrote. “Message distribution occurs through automatic platforms using VoIP number or compromised credentials, which is often deployed in multi-wave operations at accurate time to maximize effectiveness.
In addition, embedded phishing links in these messages use time-limiting single-utility URLs that were finished or redirected based on device fingerprinting to get out of safety analysis, they found.
“Economics is strongly advocated by the attackers, as neither RCS nor IMESSAGE messages are traditional SMS to the costs, which enables high-virtue campaigns at minimal operating expenses,” Proudft continued. “The overlap in the template, target pool, and strategy between these platforms underlines an integrated danger landscape, with Chinese speaking actors running innovation in the underground economy. Their ability to score and the technology of theft faces significant challenges for cyber security.”
Ford meril Works in safety research SolitudeA CSIS Security Group Company. Meril said that he has observed at least one video of a Windows binary that wrap chrome and it can be used to load in target phone numbers and blast messages through RCS, IMES, Amazon, Instagram, Facebook and WhatsApp.
Meril said, “The evidence we have seen suggests the ability to send about 100 messages per second to the same device.” “We also believe that the volume has a capacity for the source Country Specific SIM card that allows them to register individual online accounts, which require verification with specific country codes, and even provide those SIM cards long-term for physical equipment so that services that rely on the appearance of a phone number or SIM card on a mobile network.”
Experts say that this rapidly growing wave of card fraud persists as many financial institutions are still default to send a bar code through SMS to validate card enrollment from Apple or Google to mobile wallet. Krebsonsecurity interviewed several security officers in non-American financial institutions who spoke on the condition of anonymity because they were not authorized to talk to the press. Those banks have since worked with an SMS-based one-time code and now customers need to log in to the bank’s mobile app, before they can link their cards to digital wallets.


