
Forescout Vedere Labs Safety Researchers have added ongoing attacks, which targets maximum severity vulnerability that affects Sap Netwever examples to a Chinese danger actor.
SAP released an out-of-band emergency patch on 24 April, so that this informal file upload safety defects (can be tracked as Cve-2025-31324) Sap netweaver in visual musician, a few days later of cyber security company Reconsideration The vulnerability to be targeted in the first attacks was detected.
Successful exploitation enables informal attackers to upload malicious files without logging in, leading them to achieve distance code execution and potentially to complete the system agreement.
RLIAQUEST reported that the system of many customers was violated through unauthorized file uploads on SAP Netwever, in which the danger actors uploaded JSP web shell to public directors, as well as the Bruute Ratel Red Team Tool at the later stages of their attacks. The compromised SAP Netwever server was fully patted, indicating that the attackers used zero-day exploitation.
This exploitation activity was also confirmed by other cyber security firms, including the watchtower and OpasisWho also confirmed that the attackers were uploading web shell backdoor on unexpected unexpected examples online.
Unrighteous Also saw The CVE-2025-31324 zero-day attacks dating at least in mid-March 2025, while Onapsis updated its original report, stating that his Honeyipot had captured reconnaissance activity and payload test for the first time from January 20, with exploitation efforts starting from February 10.
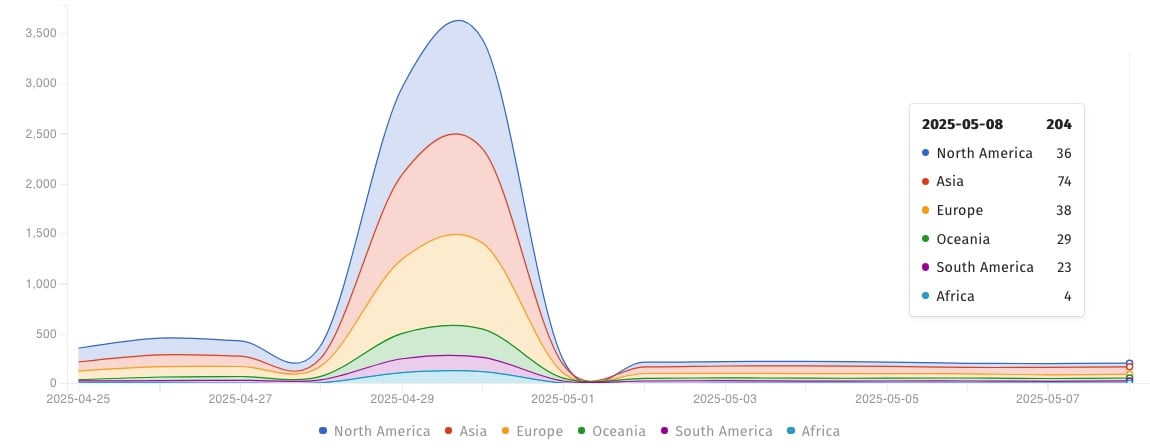
Shadowseerver Foundation is now Tracking 204 SAP Netwever Server Online and unsafe for CVE -2025-31324 attacks.
Onyphe CTO Patriss Affret also told Bleepingcomputer at the end of April that “20 Fortune 500/Global 500 companies are somewhat unsafe, and many of them are compromised,” at that time, 1,284 weak examples were revealed online, out of which 474 already agreed.
Attacks related to Chinese hackers
More recent attacks on April 29 have been linked to a Chinese threat actor. Vedre Labs of Forescout Chaaya_004 as.
These attacks were launched from IP addresses, using an anomalous self-composed certificates that affect Cloudflair, many of them belonged to Chinese cloud providers (eg, Alibaba, Shenzhen Tensant, Huawei Cloud Service and China Unicom).
The attacker also deployed Chinese-language equipment during violations, including a web-based reverse shell (superchel) developed by a Chinese speaking developer.
“As part of our investigation into the active exploitation of this vulnerability, we highlighted the malicious infrastructure related to a Chinese danger actor, which we are currently tracking as Chaaya_004 – after our conference for anonymous danger actors, said” Forescout said.
“Infrastructure includes a network of servers hosting the supercale backdoor, often deployed on Chinese cloud providers, and various pen test equipment, many of Chinese origin.”
SAP admins are advised to immediately patch their netweaver examples, restrict access to metadata uploader services, monitor suspected activity on your server, and consider disabled to visual musician service if possible.
Sisa is also couple CVE-2025-31324 Security Dosha for this Known exploitative weaknesses catalog A week ago, we were ordered by federal agencies to secure our system against these attacks by 20 May, as was necessary. Binding Operational Directive (BOD) 22-01,
“These types of weaknesses are frequent attack vectors for malicious cyber actors and pose significant risks for federal enterprises,” Sisa warned.



