
An important Citrix Netscaler vulnerability was tracked as the CVE-2025-5777 and dubbed “Citrixbled 2”, exploited about two weeks before the proof-off-concept (POC) exploits about two weeks before.
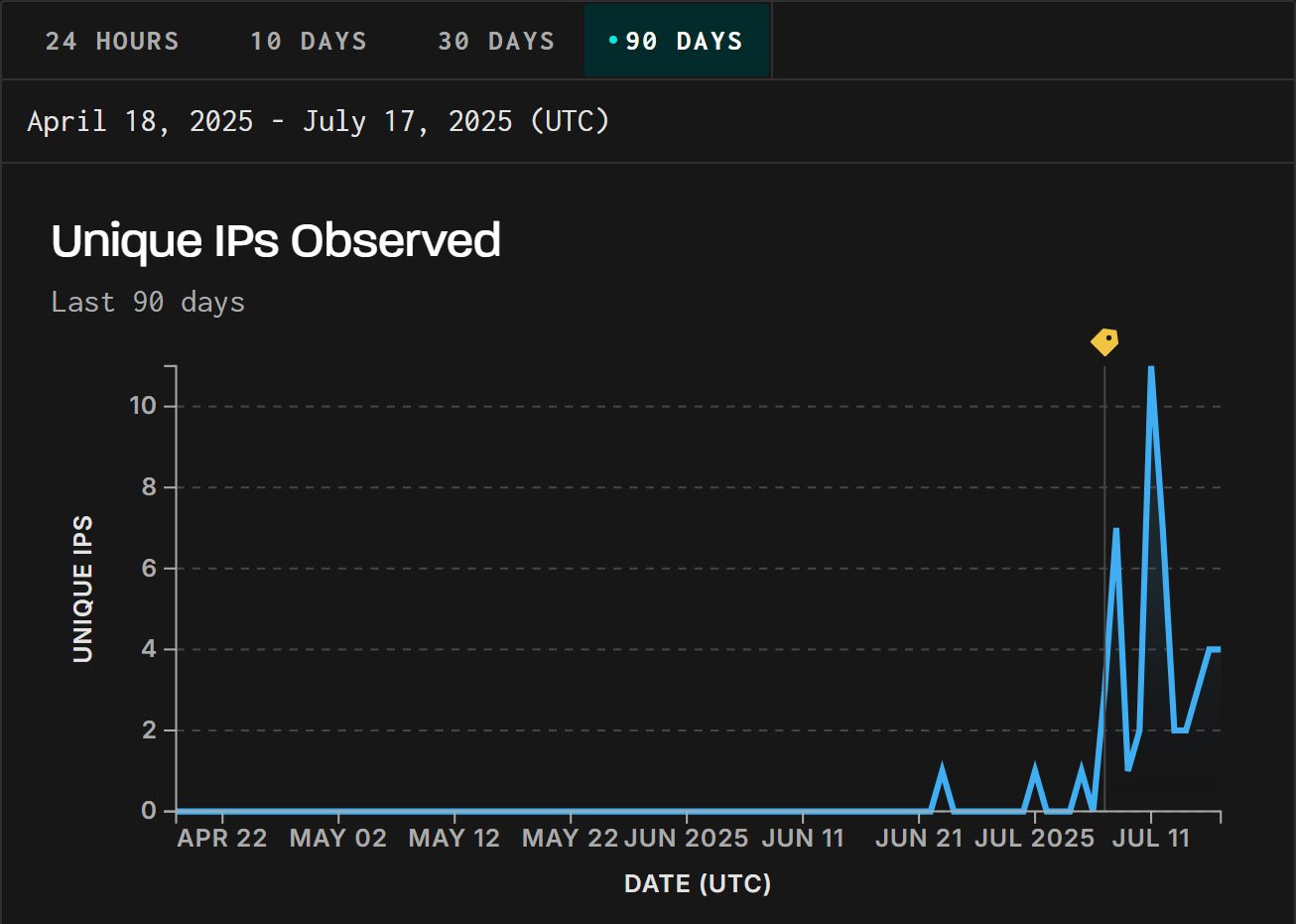
GRIYNOISE has confirmed its honeypots to detect targeted exploitation from IP addresses in China on 23 June 2025.
“Greynoise has seen active exploitation efforts against CVE-2025-5777, a memory overdade in Citrix Netscaler started on June 23. The exploitation began on June 23-a public proof-hop (POC) was released two weeks ago,” was released on 4 July, ” Greynoise explains,
“We have created a tag on 7 July to track this activity. Because GRYNOISE RERNOISE RESTORACTION affiliates pre-tag traffic with new tags, prior exploitation efforts are now visible in Greynoise Visualizer.”
Source: Bleepingcomputer
Granois confirmed the US Cyber Security and Infrastructure Security Agency (CISA) on 9 July that the defect was actively exploited, adding it to the cyber agency added it to its known exploited weaknesses (KV) catalogs and gave it to federal agencies a day.
Greynoise shared the exploitation used with bleepingcomputer in June attacks and we can confirm that it is one for Citrix Bleed 2, showing that the danger actors were actively exploiting it before the POCS was released.
Despite these early signs and Repeated warnings From security researcher Kevin Buomont, Citrix still did not accept its active exploitation Security Advisor for CVE-2025-5777It was only quietly updated 26 June blog post On July 11, it was seen in the KV database a day earlier.
Citrix finally released Another blog post How to evaluate Netscaler logs for indicators of the agreement on 15 July.
However, even with this, the company has been set on fire to not be transparent and share IOCS that researchers have stated that Bleepingcomputer was first shared with the company.
Citrix has also not responded to the questions of bleepingcomputer that the original CVE-2025-5777 advisor still does not still accept exploitation.
Citrix gives blood to 2 vulnerability
Citrix Bleed 2 is an important 9.3 severity vulnerability caused by insufficient input verification, which allows the attackers to send a perverted post requests to Netscaler equipment during login efforts.
This “login =” is exploited in the parameter leaving the same symbol, leaking 127 bytes of memory. Researchers at Horizon3 and Watchtower displayed that frequent requests can be used to highlight sensitive data such as valid sessions tokens.
These tokens can then be used to kidnap Citrix sessions and achieve unauthorized access to internal resources.
Security researcher Kevin Beomont has earlier said that repeated post requests /doAuthentication.do Netscaler log is a good indication that someone is trying to take advantage of the defect, especially when the request involves a material-length: 5 header.
Other signals include log entries that show users logoffs, where the user names have unusual characters, such as “#”, or printed memory material printed in the wrong field.
Buomont also warned that the guidance of Citrix fails to clarify the fully compromised sessions.
While ICA and PCOIP recommends abolishing sessions using Citrix kill icaconnection -all And kill pcoipConnection -allBeomont advised to abolish other sessions types, which may have kidnapped sessions:
kill pcoipConnection -all
kill icaconnection -all
kill rdpConnection -all
kill sshConnection -all
kill telnetConnection -all
kill connConnection -all
kill aaa session -all
Admins must review all sessions before finishing them to examine the suspected login, such as unexpected IP address changes or unauthorized users.
Citrich 15 July blog post Identification of signs of exploitation shows more guidance, such as log entrys the following messages:
- “Is dismissed for certification”
- “AAA Message”
- Non-ASCII Bite value (0x80–0XF)
The session logs can be manually inspected for unusual IP address changes associated with the same session. For example, in the VPN log, a mismatch between client_ip and source IP address may indicate that a session was kidnapped.
In a recent post, Buomont said that he has been monitoring exploitation since June, in which more than 120 companies have already compromised the defect.
“Access began on 20 June 2025, with ramping with ramping from June 21 with ramping,” with ramping, ” Warns the boom,
“I think the activity I see can be a threat an actor group – they can be more. They are careful in choosing the victims, to make sure that it is a real box – as if they do not fall into any of my honeypots.”
Researcher also warns that Citrix’s own web application firewall does not currently detect exploitation of CVE-2015-5777. However, Employee report His product has detected more than 11.5 million attempts to take advantage of this defect, with 40% of the financial sector targets.
Citrix has released patches for Netscaler ADC and Gateway versions and is strongly urging immediate upgradation.
There are no mitigation beyond the patching, and customers running the EOL version (12.1 and 13.0) should upgrade to the build supported.



