
To reduce the speculation of cyber attacks or BGP hijack phenomenon due to a recent 1.1.1.1 resallver service outage, Claudflair explains in a post -mortem that the incident occurred due to an internal misunderstanding.
The outage took place on July 14 and influenced most of the users of service worldwide, unavailable in many cases internet services.
“The root cause was an internal configuration error and did not result in attack or BGP kidnapping,” Cloudflare says in declaration,
This statement came on social media after the information of people that the outage was due to BGP Hijack.
Global outage unfolding
Cloudflare’s 1.1.1.1 Public DNS was launched at the resolver 2018, promising users worldwide promise a private and sharp internet connectivity service to users worldwide.
The company suggests that the outage was a configuration change for the future data localization suits (DLS) made on June 6, which accidentally connected the 1.1.1.1 resolver IP prefixes to a non-producing DLS service.
On July 14, on 21:48 UTC, a new update added a test space to the passive DLS service, refreshed the network configuration globally and implemented misunderstandings.
This withdrew 1.1.1.1 resolver prefixes from Cloudflare’s production data centers and rooted them to the same offline, which made the service unattained globally.
After less than four minutes, the DNS traffic began falling on the 1.1.1.1 resolver. Up to 22:01 UTC, Cloudflare discovered the incident and revealed it to the public.
The misunderstanding was returned to 22:20 UTC, and Cloudflare withdrew BGP to recreate the prefixes. Finally, complete service restoration at all places was achieved at 22:54 UTC.
इस घटना ने कई आईपी रेंज को प्रभावित किया, जिसमें 1.1.1.1 (मुख्य सार्वजनिक डीएनएस रिज़ॉल्वर), 1.0.0.1 (सेकेंडरी पब्लिक डीएनएस रिज़ॉल्वर), 2606: 4700: 4700 :: 1111 और 2606: 4700: 4700 :: 1001 (मुख्य और माध्यमिक IPV6 DNS RESLAST, और मल्टीपल IP Ranges Clolding के लिए कई IP Ranges includes.
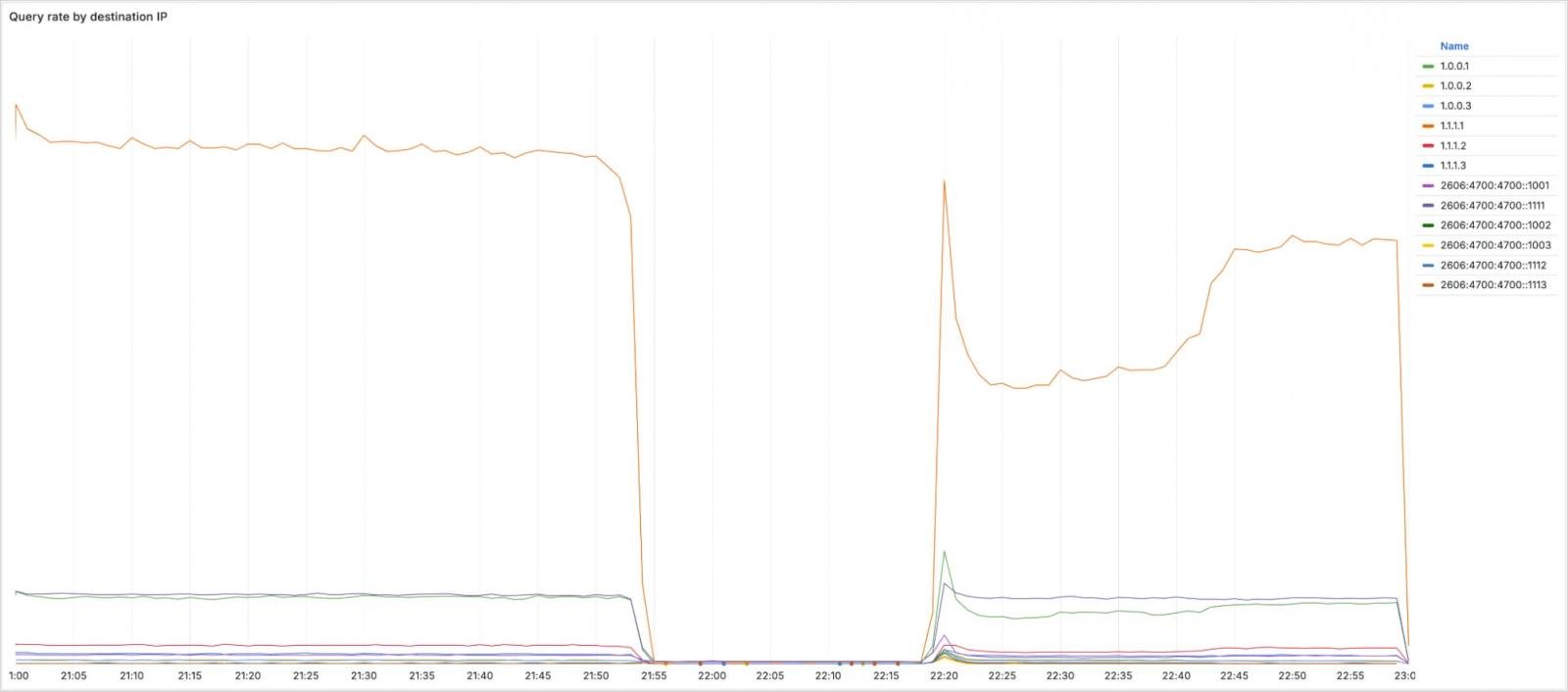
Source: Cloudflare
Regarding the effects of the incident on the protocol, the Quarries saw a significant decline in the volume at the UDP, TCP, and DNS-over-TLS (DOT), but the DNS-Over-Https (DOH) traffic was largely unaffected as it follows a different routing through cloudflare-dens.com.
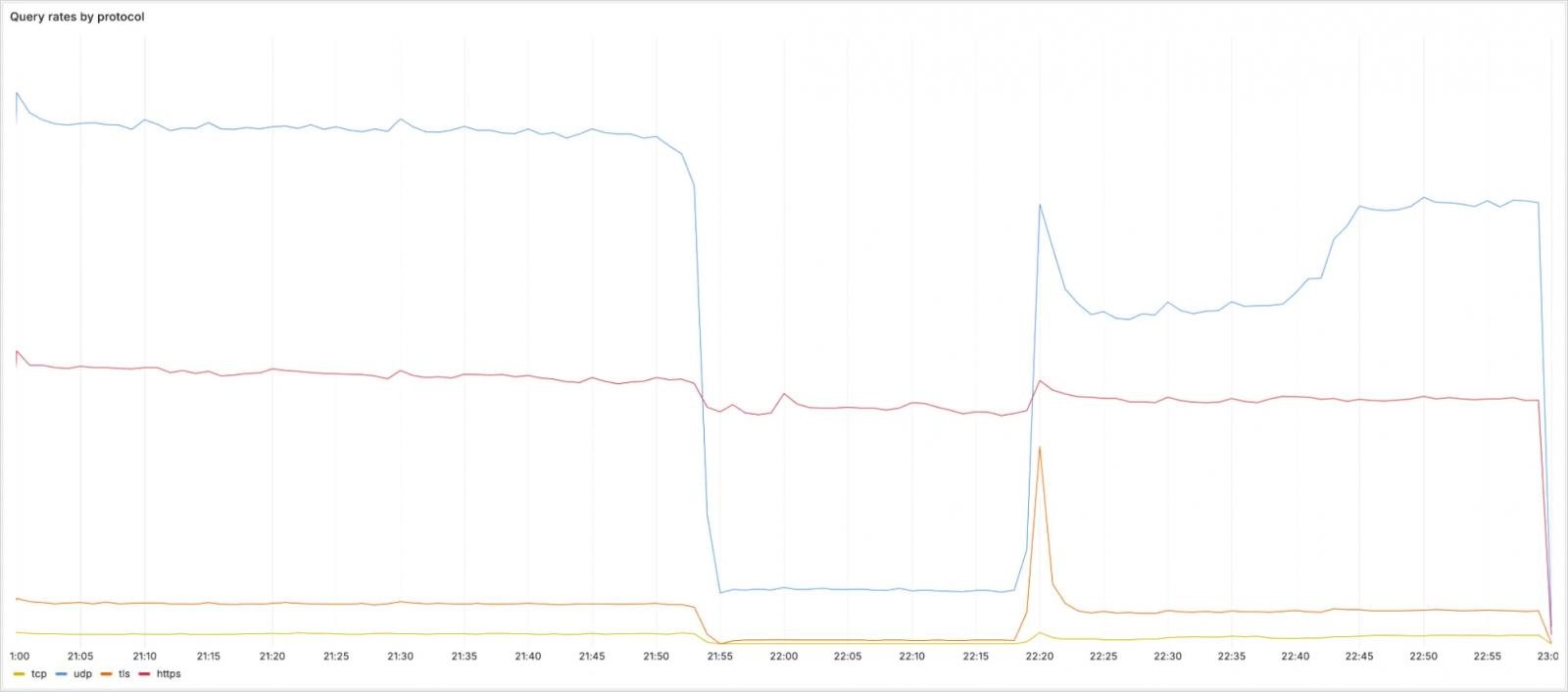
Source: Cloudflare
Next step
Misconfiguration could have been rejected. If Cloudflare used a system that performed a progressive rollout, the Internets believe that the Internet believes, blame the use of heritage systems for this failure.
For this reason, it is planning to designate the heritage systems and accelerate migration in the new configuration system, which using abstract service topology instead of stable IP binding, allow for gradual deployment, health monitoring in each stage, and in this event quick rollbacks that cause problems.
Cloudflare also suggests that Misconfiguration had passed a colleague reviews and was not caught due to insufficient internal documentation of service topology and routing behavior, an area that the company also plans to improve.



