
CTM360 The discovery of a new global malware campaign is called “clicktok”, which spreads sparkcitty spyware through fake tickets shops to steal cryptocurrency wallets and drain funds.
Unique unique spyware Trojan Discovered by CTM360 Especially the worldwide is an engineer to take advantage of Tikkok Shop users worldwide.
Dubbed as “clicktok”, this highly coordinated scam operation appoints a hybrid scam model that connects fishing and malware to cheat buyers and concerned programs on Tiktok’s growing e-commerce platforms.
In the clicktok campaign, Tiktok shops were identified embedded with sparkkitty spyware, which is intended from Sparkcat, which was previously identified by Kaspersky.
Once installed, it infiltrates the user’s device, reaches the photo gallery, and extracts the screenshot that may contain cryptocurrency wallet credentials. The unique that makes the clicktok unique is the simultaneous use of fishing and malware strategy, which has greatly increased its effects and secrets.
The scam begins with a copying of the commercial ecosystem of Tiktok, including the Tiktok Shop, Tiktok wholesale and Tikkok Mall. Threatened actors create fake tikktok websites that closely mimic the official interface, cheating users thinking that they are interacting with the real platform.
The victims are lured to log in and make shopping. During the checkout process, they are directed to pay through the cryptocurrency wallet.
Once paid, the Trojanized app captures embedded, embedded with sparkkitty spyware, which includes wallet credentials, by reading the images stored on the screenshots and devices, ultimately enable the theft of digital funds.
CTM360 has run a deep analysis of the clicktok scam and has published a detailed report on Clicktok Trojan.
Learn how sparkcitty spyware spreads through troined apps, phishing pages and AI-operated scams.
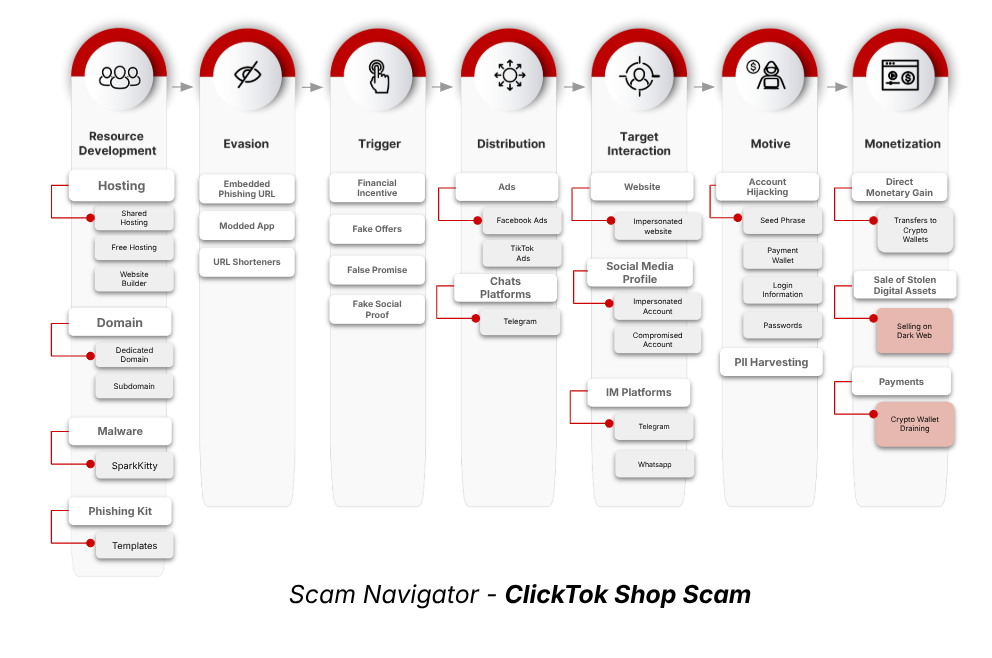
The motive behind clicktok – a hybrid scam structure
The attackers have two main objectives:
Fishing website:
They provoke users to open fake shop URLs distributed through meta advertisements, inspired users to enter login credentials, payment details or seller information, all of which are quietly cut.
CTM360 The worldwide tickek shop users have tracked a unique spyware trojan especially to exploit users.
Dubbed as “clicktok”, this highly coordinated scam operation appoints a hybrid scam model that connects fishing and malware to cheat buyers and concerned programs on Tiktok’s growing e-commerce platforms.
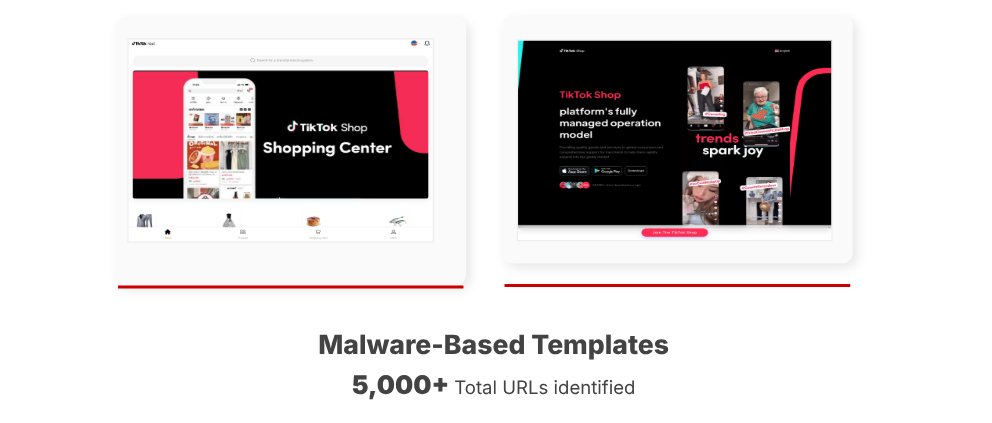
Troined apps:
On mobile, site urges users to install revised Ticketocok apps that are infected with sparkcitti, a malicious spyware variant that is capable of deep device monitoring, clipboard scraping and credential theft.
These fake apps have accurate user interfaces as the original ticket shops, to believe that they are interacting with a valid tickek app, while quietly surrounds sensitive data in the background.
Fake advertisement, AI video and Luklaic Domain
Clicktok scammers use fake AI-related videos and meta advertisements to reach wide audiences. These advertising users have been designed to directly look like real -tickek URLs for fake cyberswentad domains.
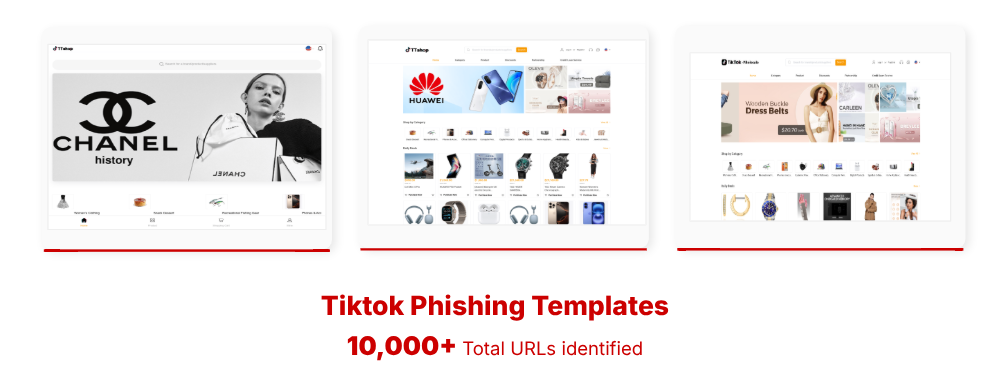
To date, CTM360 has seen:
-
10,000+ implemented Tikkok websites, many free or inexpensive TLDs such as .top, .Shop, .ICU, and others.
-
Spread through more than 5,000+ unique malicious app instance, QR code, messaging apps and in-app downloads.
Not only the shop of Tiktok, but also a fake campaign affecting Tikok wholesale and Tikok Mall.
Motive
The clicktok campaign uses fake tickek shop login pages for harvesting of user credentials and malware distribution through Troined apps that are able to kidnap the account. It applies an alternative payment structure that excludes traditional card transactions, instead requires payment through cryptocurrency wallets.
Victims are often encouraged to “top up”, fake tickek wallets or digital currencies such as USDT, Eth and more.
CTM360 recommendations
CTM360 urges users and organizations to be vigilant and take the following precautions:
-
Avoid downloading moded, torn, or unknown software especially from torrent sites and telegram.
-
Always verify the domain authenticity before entering login or payment information, and manually check for spelling errors or suspected domain extensions.
-
Report any suspected tiktok-related material, advertisement or apps directly to Tiktok or Cyber Security Officers in your country.
-
Brands and vendors should monitor brand misuse and copy trends regularly using danger intelligence platforms.
-
Strong antivirus or EDR solution to prevent sparkkitty spyware violations.
-
If you use a crypto wallet, go for a clipboard-protected.
Find 24/7 cyber threats with CTM360
Monitor, analysis and immediately reduce the risk in your external digital scenario with CTM360.
Sponsored and written by CTM360,


