
Actor with danger associated with low-knowledge ransomware and malware projects now now use AI tools to infect victims with malicious payloads.
This development follows a trend that has been growing since last year, begins with advanced danger actors using deepfec content generators to infect victims with malware.
They have become lures widely adopted Attempts to dissolve the corporate network by information-information malware operators and ransomware operations.
Cisco Talos Researcher Found out After the same technique, small ransomware teams are now known as cyberlock, lucky_GH 0 $ T, and a new malware called Numero.
The malicious payload is promoted via SEO poisoning and the search engine results for specific terms are malwarting to rank high in the results.
AI Equipment Immunity
Cyberlock is the powerrashel-based ransomware given through a fake AI tool website (Novaleadsai (.) Com), which presents as valid novaleads.app.
.jpg)
Source: Cisco Talos
The victims are lured by a free 12 -month membership proposals, leading them to download a .NET loader that deploys the ransomware.
Once the victim is executed on the machine, the cyberlock encrypted files in several disk division, which adds. Cyberlock Extension on locks.
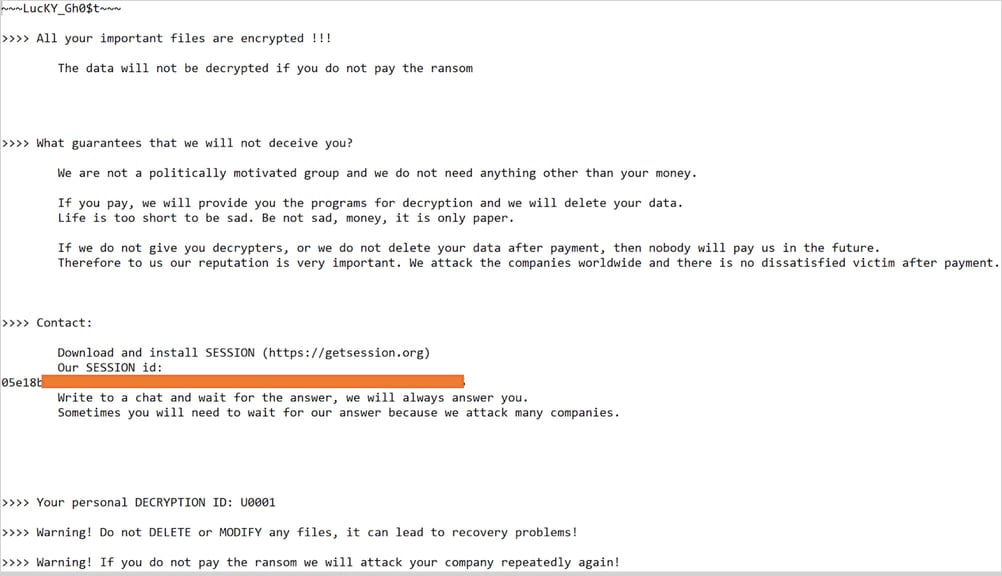
The Ransum Note Hard-to-Treas Monero demands a ransom of $ 50,000 in cryptocurrency, claiming that money would support human causes in Palestine, Ukraine, Africa and Asia.
Source: Cisco Talos
Lucky_gh0 $ T is a new ransomware strain taken from Yashma, which is based on the chaos ransomware itself.
Cisco analysts noticed that it is being distributed as a fake chatgpt installer (“” Chatgpt 4.0 Full Version – Premibum.exe “) is packed in a self -evidence collection.
The package includes a valid microsoft open-source AI tools with ransomware payload, which is likely to detect antivirus.
If executed, it encryps the files smaller than 1.2GB, which combines random four-ornament extensions, while large files are replaced and removed with the same size junk file.
Victims of Lucky_gh0 $ T receive an individual ID and are instructed to contact the attacker through a safe messenger platform session safe for ransom talks and decryption.
Source: Cisco Talos
Finally, a new malware, as an invoideo AI installer, is called Numero Muscanders, but is designed to attack the Windows system.
Malware is an executable in a dropper called a batch file, VB script, and an executable wintitle.exe.
It executes an infinite loop, constantly corrupted the victim’s graphical user interface by the content, button, and numeric string “by the material with 1234567890.
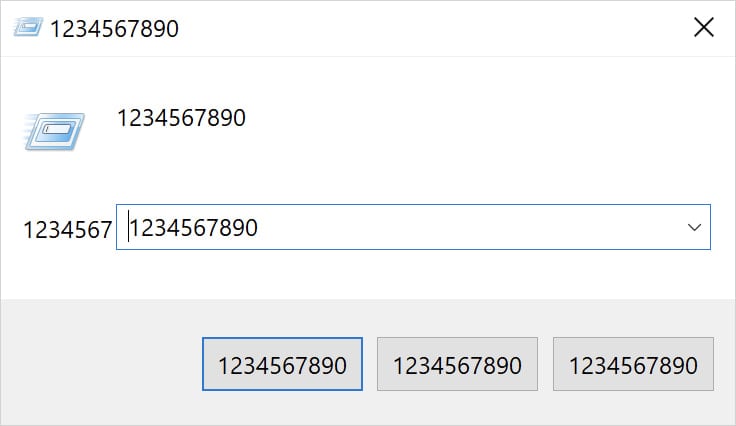
Source: Cisco Talos
Although no data is destroyed or encrypted by the nambbo, the malware presents the Windows system that makes it completely unusable. At the same time, the infinite loop that runs ensures that the system is “lock” in this blind corrupt state.
Since more cyber criminals try to take advantage of people’s increasing interest in AI Tools, it is advisable to take precautions with files downloaded from suspected websites.
It would be more prudent to stick to major AI projects instead of using new tools and sources instead of following the link from promoted results or social media posts.



