Researchers have released a report, stating that Winrar Path Traversal Vinnerability was recently tracked as Cve-2025-8088, which was explained by the Russian ‘Romcom’ hacking group to leave various malware payloads.
Romcom (aka Storm-0978 and Tropical Scorpion) is a Russian Cyberpassing Threat Group, which has a history in zero-day exploitation, including Firefox (CVE-2024-9680, Cve-2024-49039) and Microsoft Office (Cve-2023-36884).
The ESET found that Romomom was exploiting an unintended path traversal zero-day vulnerability in the winner on July 18, 2025, and informed the team behind the popular archive equipment.
“The analysis of exploitation led to the discovery of vulnerability, now assigned to CVE-2015-8088: a path traversal vulnerability, made possible with the use of alternative data currents. New report Published by ESET today.
Winner issued a fix for the blame, which was assigned with the identifier CVE-2025-8088 on 30 July 2025 Version 7.13However, there was no mention of active exploitation in the advisor.
The ESET confirmed malicious activity for the Blapping computer at the end of last week, which was believed to be used when the user opens a specially designed collection, is used to remove dangerous executionable in the autorun tracts.
Another path in the vulnerable Winrar was similar to traversal defects, revealed a month ago, was tracked as cve-2015-6218.
The ESET report states that the malicious RAR archives include several hidden advertisements (alternative data stream) payloads that are used to hide a malicious DLL and Windows shortcuts, which are extracted into the attacker-free folder when opening the target.
Many of the advertisements are for invalid paths, which ESET believes that the presence of malicious DLL, ExE, and LNK file paths was deliberately added to generate harmful -looking Winrar warnings, hiding deep into the file list.
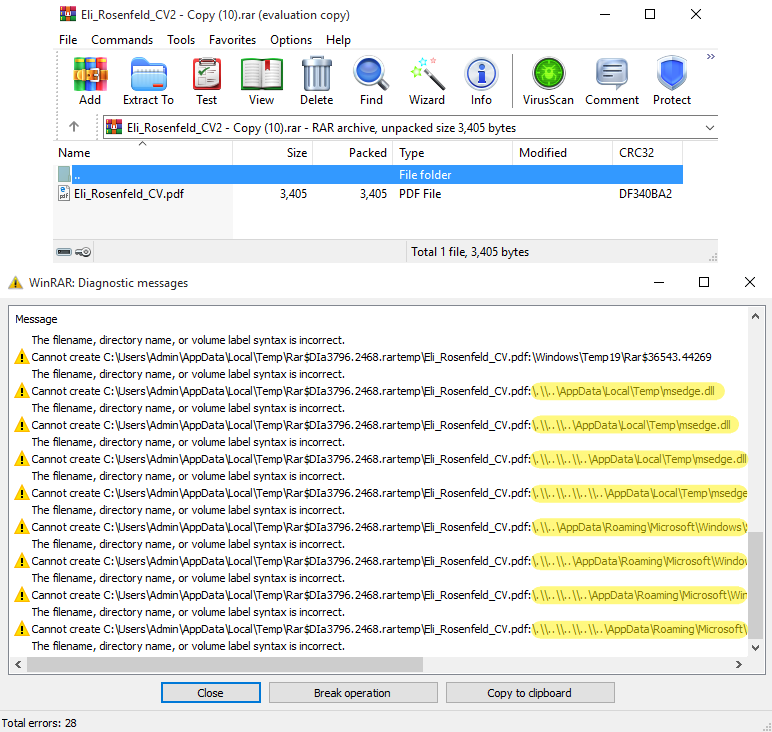
Source: ESET
The execution is placed in the % TEMP % or % Localappdata % directors, while the Windows shortcut (LNK files) is dropped in the Windows Startup Directory to execute them on the latter login.
ESET documentation of three separate attack chains, distributes to all known Romcom Malware families:
- Myth agent – Updater.lnk msedge.dll adds to com hijack registry location, which decipses AES Shellcode and only moves when the system domain matches a hardcoded value. Shelcode launched the myth agent, which enables C2 communication, command execution and payload delivery.
- SnipboT – Display Settings. LNK Runs Avxhelper.exe, a modified putty cac with an invalid certificate. It checks the shellcode for the recently opened documents for Shell69 before decrying the shellcode that downloads the additional payload from the attacker server.
- MaltingClav – Settings.lnk started the complaint.
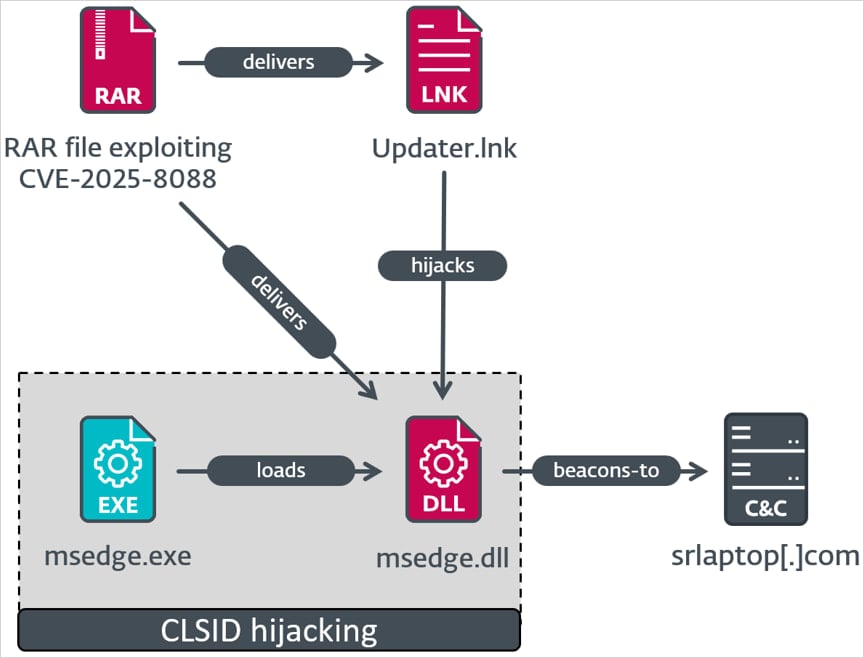
Source: ESET
Russian cyber security firm BI.Zone also reports While observing a separate activity cluster, which they track as ‘paper warewolf’, as well as CVE-2025-8088, as well as CVE-2025-6218, also avail the attacks.
ESET shared full indicators of agreement for the latest firm attacks Its github repository,
Although Microsoft added native RAR support to Windows in 2023, this feature is available only for new release, and its capabilities are not as widespread as ripe people in the winner.
Therefore, many power users and organizations continue to rely on the winner for the management of the archives, making it a major goal for hackers.
Rarlab told bleepingcomputer that he did not know about the exploitation details of CVE-2025-8088, not any user report, and ESET shared with only technical information necessary to develop a patch.
Winrar does not have an auto-update feature, so users need to download and install manually Latest version from here,



