
The ransomware is re -conducted, with a gang known as a dragonforce, working to gather other operations under a cartel -like structure.
The Dragonforce is now encouraging ransomware actors with a distributed affiliated branding model, providing the other Rainmore-A-Sarvis (RAAS) operations, which is a means of completing your business without dealing with infrastructure maintenance costs and efforts.
The representative of a group told Bleepingcomputer that they were purely economically motivated, but also followed a moral compass and some health organizations were against attacking.
Typically, an RAAS has its own partners or partners of the operation, and the ransomware developer provides file-encrypting malware and infrastructure.
The collaborative encrypting package will build a type of breech afflicted network, and deploy ransomware. They will also manage decryption keys and usually interact with the victim for ransom payment.
The developer also holds a so -called data leak site (DLS), where they publish stolen information from the victims who did not pay to the attacker.
In return for using its malware and infrastructure, the developer charges a fee from the ransom receiving a fee that is normally up to 30%.
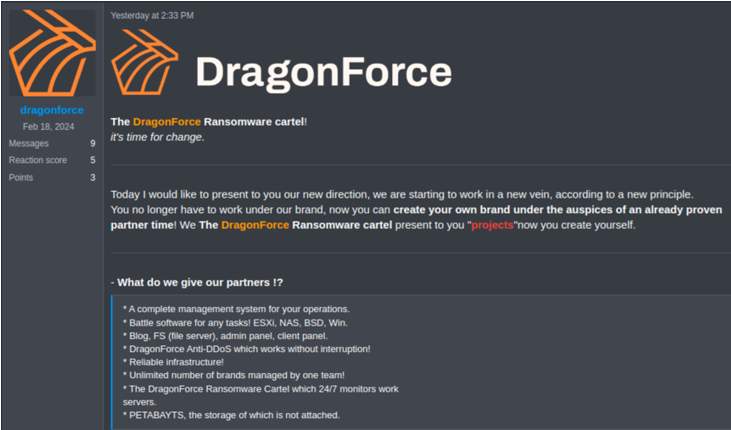
Dragonforce ransomware business
Dragonforce now calls itself a “ransomware cartel” and takes 20% of the paid ransom.
Under their model, colleagues have access to infrastructure (storage tools, stolen data, storage for malware), and use the Dragonforce Encryptor under their own branding.
The group announced the “new direction” in March, saying that allies can already make their brand under the aegis of a Siddha companion. ,
As the post below says, Dragonforce aims to manage “unlimited brands” that can target ESXI, NAS, BSD and Windows System.
Source: work safe
Dragonforce told Bleepingcomputer that their structure is from a market, where colleagues can choose to deploy attacks under the Dragonforce brand or a separate one.
Originally, groups of danger actors can use service and white label under their name, so it appears that they are their own brands.
In turn, they do not have to deal with the headache of data leaks and dialogue sites, develop malware, or deal with dialogue.
However, and the affiliates will be kicked in the first misses. “We are honest partners who respect the rules,” the dragonforce representative told us.
Dragonforce says, “They have to follow the rules, and we can control it because whatever we run is on our server, otherwise it is not understood.”
However, those rules are available only to endanger actors embracing new proposed ransomware business models.
Asked if the hospital or healthcare organizations are out of the boundary, Dragonforce said it all depends on the type of hospital, and showed what can be described as sympathy.
“We cancer patients or anything related to heart, we send them money and help them. We are here for business and money, I did not come here to kill people, nor did my partners say,” The actor told the actor the actor.
Researchers at the cyber security company say that the model of the dragonforce may appeal to a wide range of colleagues and attract less technical threats.
“Even sophisticated danger actor can appreciate flexibility which allows them to deploy their own malware without creating and creating their own infrastructure” – – – – – – – work safe
By increasing the affiliated base, the dragonforce can see the large advantage operated by the flexibility of its proposed model.
It is not clear how many ransomware colleagues have approached Dragonforce Cartel about the new service model, but the danger actor stated that the member list includes the famous gangs.
“I can’t tell you the exact number, but we have players who come to us, about whom you often write and want to cooperate with us,” Dragonforce told BlappingCopper.
A new ransomware gang called Ransombay has already subscribed to the model of dragonforce.


