
Over 46,000 internet-focus graphs examples are unaffected and come in contact with a client-side open redirect vulnerability that allows a malicious plugin and account takeover to execute.
Is tracked as a defect Cve-2025-4123 And influences several versions of the open-source platform used to monitor and imagine infrastructure and application matrix.
Bug bunty huter discovered vulnerability Alvaro Balada And was addressed in Safety update The Greffana Labs was released on 21 May.
However, as it is, one of all graphs has not been available on more than one third of the public internet, according to the researchers of the application security company Ox Security, who refer to the bug as ‘The Grafana Ghost’.
Analysts told Bleepingcomputer that his work focused on demonstrating Balada’s discovery to make weapons.
After identifying unsafe versions for the attack, he accepted the exposure by coringraizing data with the distribution of platforms in the ecosystem.
He found that 128,864 examples were exposed online, still running weak versions with 46,506 which can still be exploited. It corresponds to a percentage of about 36%.
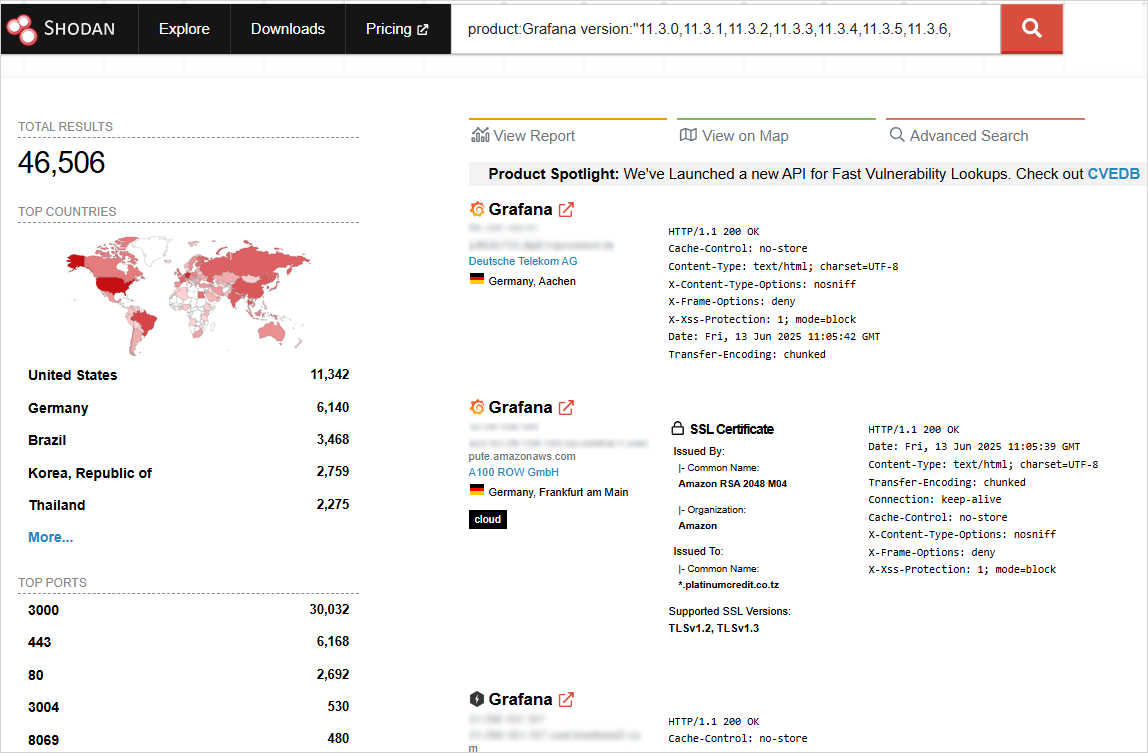
Source: Bleepingcomputer
The intensive analysis of Ox Security by CVE-2025-4123 revealed that, through a series of exploitation stages of combination of client-side path traverse with open redirect mechanics, the attacker can suffer in clicking the URL to click on the URL that leads to loading a malignant grafana plugin from a site controlled by the actor with danger.
Mulnerable links can be used to arbitrarily perform JavaScript in the user’s browser, Researchers say,
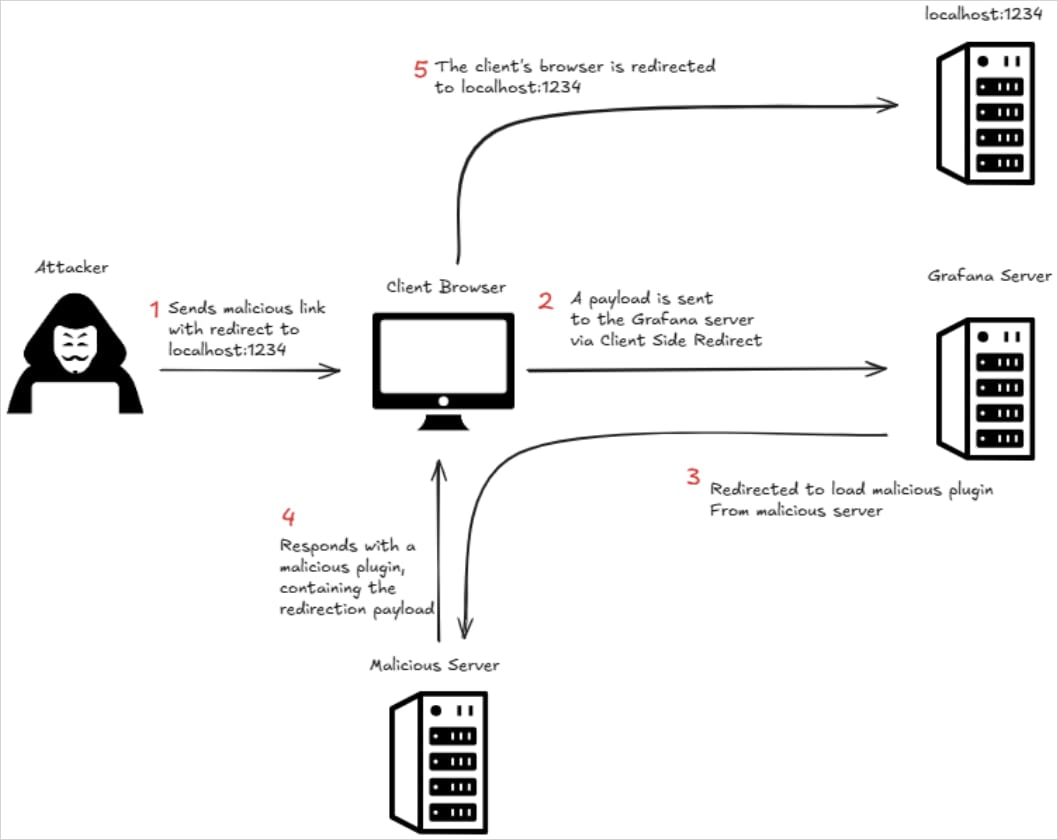
Source: Bull Security
Exploitation does not require high privilements and may work even if it is able to reach anonymous.
The blame allows the attackers to abduct user sessions, replace account credentials, and, in cases where graphna image render plugins have been installed, server-side request forms (SSRF) to read internal resources.
While the default material safety policy (CSP) in Grafana provides some protection, it does not prevent exploitation due to boundaries in client-side enforcement.
The exploitation of ox security suggests that client-side of CVE-2025-4123 can be exploited and it can be leveraged to bypass modern browser generalization mechanisms through JavaScript routing logic indigenous graphana.
This allows the attackers to exploit URL handling discrepancies to serve malicious plugins, which in turn modify the email addresses, causing the account kidnapping through the password reset.
Although the CVE-2025–4123 has many exploitation requirements, such as user interaction, an active user session when the victim clicks on the link, and the plugin feature is enabled (default is enabled), creates a significant attack surface.
To reduce the risk of exploitation, it is recommended that the graphna administrator version 10.4.18+ security -01, 11.2.9+ security -01, 11.3.6+ security -01, 11.4.4+ security -01, 11.5.4+ security -01, 11.6.1+ security -01, and 12.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.



