
Hackers are beginning to exploit CVE-2025-49113, a significant vulnerability in the widely used roundcube open-source webmail application that allows remote execution.
The safety issue has been present in the roundcube for more than a decade and affects versions of the roundcube webmail 1.1.0 through 1.6.10. It received a patch on 1 June.
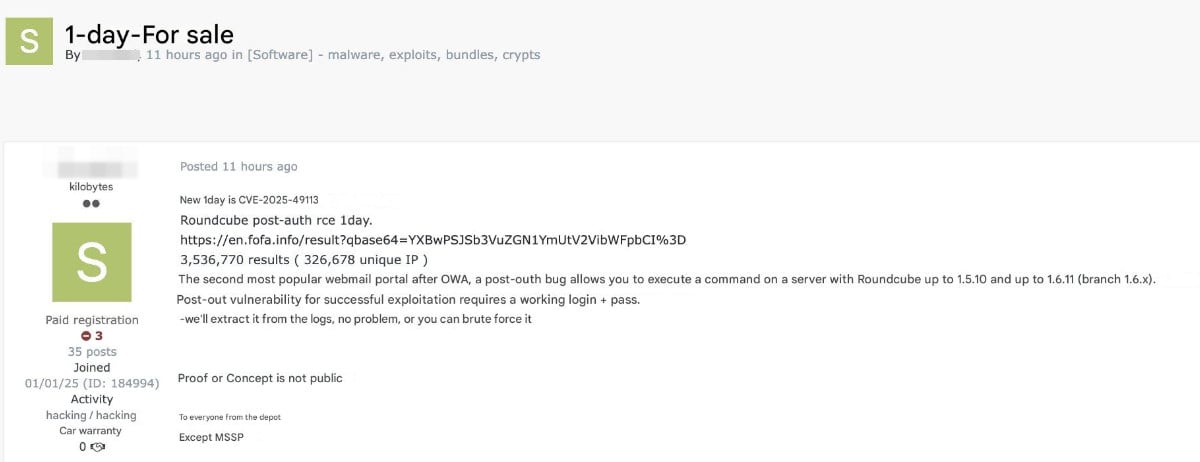
It took only a few days to fix the attackers, reverse the fix, making arms to arms and selling one work on at least one hacker forum.
Roundcube is one of the most popular webmail solutions as the product is included in proposals of famous hosting providers such as Godaddy, Hostinger, Dreamhost, or OVH.
“Email Armagadon”
CVE-2025-49113 is a post-authentication remote code execution (RCE) vulnerability that has got a significant seriousness score of 9.9 out of 10 and is described as “email arms”.
It was discovered and reported by Cybecity Company CEO Kiril Ferresov ScaryWho decided to publish technical details before the end of the responsible disclosure period as an exploitation was available.
“Looking at the active exploitation and evidence of exploitation being sold in underground forums, I believe it is in the best interest of defenders, blue teams and comprehensive security community, which is to publish a full technical breakdown but without full POC for now” – – Kiril Firceov
There is a lack of hygiene at the root of safety problem $ _GET (‘_ to’) Parameter, which leads to PhP object deserialization.
In the technical report, Ferresov explains that when an exclamation mark starts a session variable name, the session is contaminated and object injection becomes possible.
After receiving a patch to the roundcube, the attackers analyzed it, developed an exploitation, and advertised it on a hacker forum, given that a working login is required.
However, login credentials do not seem like a preventive, as the actor with exploitation says that they can remove it from the log, or it may be forced.
Firsov says that credential combinations can also be obtained through cross-site request forgery (CSRF).
Source: Kiril Firceov
According to Firesov, at least one vulnerable broker Pays up to $ 50,000 For an RCE exploitation in the roundcube.
The researcher published a video to showcase how vulnerability could be exploited. It should be noted that the researcher uses vulnerable identifier CVE-2025-48745 in performance, which is currently rejected as one. Duplicate candidate For cve-2025-49113.
https://www.youtube.com/watch?v=tbktbmjwhjy
Despite having a low-following application among consumers, the roundcube is very popular, mostly because it is highly adapable with more than 200 options, and it is freely available.
Apart from hosting the providers and bundled in web hosting control panels (CPANEL, PLESK), many organizations in the government, educational and technical fields use roundcube.
Firsov also says that there is such a wide presence of this webmail app that a paintter is more likely to find a roundcube example than the SSL misconfiguration.
Keeping in mind the omnipresent of the application, the researcher says “The surface of the attack is not large – it is industrial.”
Indeed, a quick look at the search engines for the discovery of internet -related equipment and services show at least 1.2 million roundcube hosts.



