Disclaimer: The materials presented in this article are particularly publicly available, based on unclapsed information and open-source research. It does not draw on any classified or proprietary data. The analysis is completely as a technical idea practice to detect potential cyber security ideas in terms of heritage aircraft systems and industrial control systems. This article also does not represent the official policy, guidance or recommendations of any government or agency, nor is it to inform the acquisition, security policy or national defense decision making. All the opinions expressed are of the author in a personal ability.
I recently attended an Industrial Control System (ICS) Cyber Security Conference, where we learned how information technology (IT) cyber security strategies and equipment should be used to address operational technology (OT) security. It noted me that the original design of aircraft control systems is similar to the OT system that we have just learned.
Cyber security professionals are asked to secure a system designed for rapid modern hazards. Inspired by the news of The US government is evaluating a foreign-dominated Boeing 747-8 for use as Air Force (AF1), I felt that the retrofit of a heritage aircraft for national security use provides a unique lens in the IT/OT convergence problem, and why physical access and heritage protocols should now be considered as front-line risks.
Daniel Hoffman
Heritage aircraft, modern risk
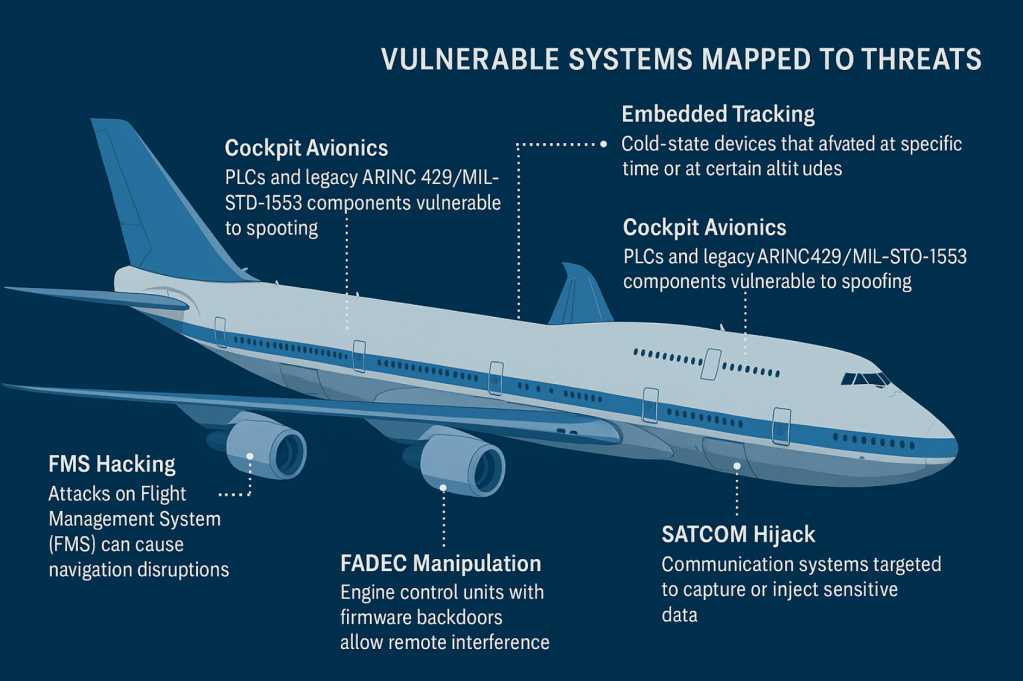
While 747–8 is a technical leap beyond 747–400, it still retains the inheritance protocol and architecture that introduces the risk, especially when the top-level national security missions are rebuilt. Many of these aircraft systems are mixed with industrial control systems (ICs), such as used in significant infrastructure. Like heritage supervisory control and data acquisition (SCADA) system, aircraft avionics often consider reliable internal communication, a trust model is not enough in today’s danger scenario.
In factory settings, these systems were often “air-gap”-they were isolated from other networks, as as a line of defense and only employees were allowed to have physical access. The aircraft developed equally. One of the main rows of defense was burial in cables and components in the torso, where unauthorized personnel could not access them.
Since the aircraft we are accessing, it was retropheated in a foreign country, we should assume that there is a possibility of transplanted, inactive equipment or tampering with common devices.
Major weaknesses exposed
| Threatening type | Effect | Activation system | Detection method |
| Hardware transplant | Engine/control sabotage | RF trigger, preset logic | X-ray, tear |
| Firmware backdoor | Navigation/System Overrid | GPS/Time Trigger Code | reverse engineering |
| Cold-state trackers | Location exfoliation | Height or temporary | Environmental simulation |
| Radar-based exfIs | Secret data leak | Wave modulation | Discrepancy/radar signal analysis |
| Satcom hijack | Comss interception | RF signal kidnapping | Spectrum monitoring, verification |
| Toolchen exploitation | Persistent access | Malicious clinical equipment | Source and firmware audit |
| Mitm on avionics buses | Command injection, replay attack | Cable Tapping/Sprowing | Signal integrity/time analysis |
| Cellular subcontum | Audio or GPS Leak | Passive baseless payload | Spectrum forensic, tearing |
Inheritance protocols create new attack surface
One of the OT World’s restrictions is dependence on heritage technology that cannot be easily patching or upgraded without large disruption. Similarly, Boeing 747–8 a hybrid simply appoints architecture. While it integrates modern flight management technologies such as Thales Topflight Flight Management System (FMS), many subcontrem still rely on ARINC 429 and MIL-STD-1553, protocols that lack certification or encryption.
As mentioned Arxiv: 1707.05032This code can release weaknesses such as injections and manipulation, data injections, data leaks and dos. Even the new Ethernet-based systems using AFDX (ARINC 664) lack cryptographic safety measures. As we have just mentioned, traditionally, 747 depends on physical controls such as restricted physical access. In this case, that control has already been compromised.
These channels highlight the aircraft to mitm, spuofing and reply attacks, especially during retrofiting or maintenance cycle. Ukwandu et al. (2022) Highlight the safe protocol of the avionics industry at a slow adoption. In the industrial control environment, the encryption can reduce the identical dangers, but the concern of the delay makes this approach difficult to apply to real -time flight systems, where delays can lead to serious consequences due to delay in flight control response.
Daniel Hoffman
Retrofit transplantation
Physical access during retrophitting shows other opportunities to opponents: embedding secret transplants, which is often designed to activate under specific environmental triggers. Munro (2020) underlines the scenarios where small computers (eg, raspberry PI-class) is hidden inside the avionics bey or power rail, without tearing, signal analysis or undesirable without X-rays. These devices can be used for different purposes.
Transplant and embedded monitoring
Monitoring implants can be introduced during retrofit, as mentioned above. Inactive RF microphones, compromises can capture tools sensitive audio or telemetry such as the compromise baseless transport or converted inflite entertainment system. Haller, Bittan and Shabtai (2022) Show how these systems oppose traditional identity methods, which makes post-finance audit extremely difficult. These transplants avoid standard EM sweeps and require tearing or X-ray inspection to detect.
Monitoring danger vector
- Inactive RF Microphone. These devices can harvest the ambient audio and transmit it using severed electromagnetic energy, making them extremely difficult to detect using traditional EM sweeps.
- Agreement Basband Trebors. These satellites are found in phones, LTE modem or embedded SIM and can quietly leak GPS coordinates, conversations or system data.
- Tampered Inflit Entertainment System (IFE). IFES may appear benign, but often fragmented still sits on the accessible network backplanes. If an agreement is made, they can find passenger interface with avionics.
Non-traditional data exFILTION Channel
When it comes to data exfoliation in a traditional IT/OT environment, we often rely on how to get out of transmission methods and catch them on how to get out. It becomes very complicated on our 747. Radar emission modulation has been secretly identified as a viable vector for exfIs. As mentioned in NSA Tempast Guidance (2023), such techniques mimic and avoid detection. Additional routes include Saatcom kidnapping, Bluetooth beacon or optical LED flicker, which are all heritage aircraft under-monitor. Tightening this aircraft for use as AF1, we will need to consider these routes.
Supply chain as a soft goal
The aviation supply chain presents an important cyber security risk. Important components such as firmware, clinical utilities and maintenance processes can be converted or compromised during manufacturing or integration, especially when foreign vendors are included. Malibly transplants or latent, persistent weaknesses are being introduced upwards, limited suppliers are enhanced by visibility and insufficient cyber security controls. (Aerospace Industries Association, 2023),
A widely quoted example is 2020 solarwinds breech, with the attackers compromised the Orion software update system to distribute malware to over 18,000 organizations, including American federal agencies and Fortune 500 companies. This incident revealed
Internal agreement
The cabins offer significant risks, especially in classified missions. Seats, partitions and power outlets can hide passive monitoring devices or logic circuits.
To align with Schif And Template Demand for standard, best practices:
- Full tears and internal components reconstructed
- X-rays and RF scanning of structural cavities
- Chen-of-Custody Verification for All Replacement
- RF preservation and acoustic integrity test
Standards like RTCA Do-355, Do-356A and Cnsam Tempes/1-13 are required to complete the mandate of executive transport and continuity-government, Baker, Arlane and Parkinson, Paul. (2018).
Strict retrofitted aircraft: actionable steps
- Apply the best practices RTCA and Nist. Standard lifestyle risk framework, encryption recommendations and audit mechanisms such as RTCA Do-355/356A and Nist SP 800-53. Although a complete-stack encryption may be infected, the surface of the attack can reduce the surface without compromising the corresponding performance performance.
- Copy every subcontam. Each avionics and support subcontum will have to undergo a tearing against reliable base lines, high-resolution imaging and verification. The components that fail this investigation should be replaced with certified domestic counterparts.
- Secure toolchainSellers will have to meet DFARS cyber security requirements and ideally to cmmc level 2 or higher. Firmware developers and diagnostic engineers should work within a verified safe development life cycle (SDLC).
- Apply frequent telemetry and monitoringStatic scans are insufficient. Running network behavior analysis, discrepancy detection and forensic auditing are important. This 2023 airborn system costs the cost approximately with DOD recommendations in the estimated guide.
Cost and acquisition realities
While a donated airframe may seem affordable, retrofitting costs corresponds to new aircraft purchases or may be higher. DODs and Gao benchmarks suggest that the price of safe retrofits can be hundreds of crores and can still be reduced by purpose assurances.
Domestic control still matters
The residual risk remains with foreign original systems, even after complete review. This VC -25B (next AF1) underlines the argument behind the purchase, a platform, which is built domestically under safe conditions. The project was slate to complete in 2024, Boeing Now estimates that 2027–2028. Which will still deliver with a retrofit project, or to conform to further, which may take 2-4 years One defense And Aviation source news,
Take a look at what will happen in trying to secure this aircraft, read Sample blue team playbook,
Conclusion: A Playbook/OT convergence for this
This landscape inheritance serves as a high-hand case study in securing cyber-physical systems. Cyber security leaders will face rapidly unconventional challenges. Whether it is a power plant, an inheritance fleet or a retrofitted aircraft, which can bridge it and OT Worlds, they will shape the future of safety strategy.
This article has been published as part of the foundry expert contributor network.
want to join?


