
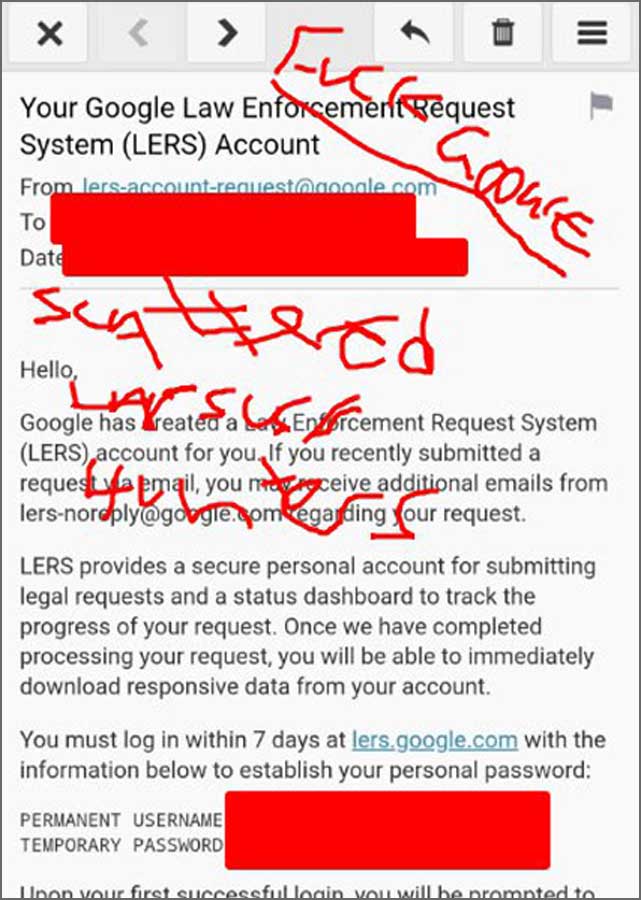
Google has confirmed that hackers created a fraud account in their law enforcement request system (LERS) platform that uses to present the official data request to the law enforcement company
Google told Bleepingcomputer, “We have identified that a fraud account was created in our system for law enforcement requests and disabled the account.”
“No requests were made with this fraud account, and no data was accessed.”
The FBI refused to comment on the actor’s claims.
The statement comes after a group of actors of the danger, calling themselves “scattered lapsus $ Hunters”, claiming Telegram that Google’s Lers Portal and FBI’s echeck background check system have access to both.
The group posted screenshots of their alleged access soon after the announcement on Thursday that they were “getting dark.”
Hackers’ claims raised concerns as the ACIC system of LER and FBI is used by police and intelligence agencies worldwide to present Sabponas, court orders and emergency disclosure requests.
Unauthorized access may allow attackers to apply law enforcement and achieve access to sensitive user data that must be protected normally.
The “scattered lapsus $ Hunters” group, which claim to be containing members associated with shiny hunters, scattered spider, and forcible recovery groups, this year is behind the massforce data stolen attacks targeting dataforce data.
The danger actors initially used the social engineering scam to trick employees to connect the data loader tools of the salesforce to the corporate salesforce instance, which was then used to steal data and remove companies.
The danger actors later violated the Githb Repository of the salesloft and used Turphalhog to scan for mysteries exposed in the private source code. This allowed them to find authentication tokens for salesloft drifts, which were further used to conduct salesforce data theft attacks.
These attacks have affected many companies, including Google, Adidas, Qantas, Allianz Life, Cisco, KerningLouis Wuiton, Dyer, Tiffany & CoCloudflare, zscaler, Elastic, Proof point, Jfrog, RubricPalo Alto Network, and Too much,
Google Threat Intelligence (Mandiant) is a fork in favor of these danger actors, which is the first to overcome their defense to disclose salesfors and salesloft attacks and warning companies.
Since then, the danger actors have been taunting the FBI, Google, Mandiants and security researchers in the posts of various telegram channels.
Late Thursday night, the group posted a long message for a domain associated with a bruechforams, believing that the danger actors were retiring.
“This is why we have decided that silence will now be our strength,” Write actor of danger,
“You can see our names in the new databrech disclosure report from other multi -billion dollars companies, which yet to disclose a violation, as well as some government agencies, including extremely safe people, does not mean that we are still active.”
However, cyber safety researchers who talk with Blapping computers believe that the group will continue to attack quietly despite dark claims.



