
The forensic investigation has confirmed the use of paragon’s graphite spyware platform in zero-click attacks targeting at least two journalists’ Apple iOS devices in Europe.
Researchers at Citizen Lab say that the victim was a prominent European journalist who requested Anonymity and Siro Palegrino, a journalist from Italian Publication Fanpage.
“Our analysis provides a prominent European journalist (who requests an oblivion), and Italian journalist Ciro Pellegrino, a prominent European journalist evidence that confirmed with high confidence. Citizen Lab Report,
At the beginning of 2025, there were attacks, and Apple sent a notification to both the victims on 29 April, stating that they were targeted by “advanced spyware”.
The danger actor used paragon’s graphite spyware platform to target the iPhone devices of victims running iOS 18.2.1 and exploited the CVE-2025-43200, which was a zero-day vandalism at that time.
Apple has described the defect as “an argument issue that shared a maliciously prepared picture or video through the iCloud link.”
The seller addressed the vulnerability by adding better checks on 18.3.1, 10 February in the next iOS release. However, cve was identifier Added to security bulletin before today ,
Bleepingcomputer has reached Apple to clarify the date of healing, but has not received the time of publication.
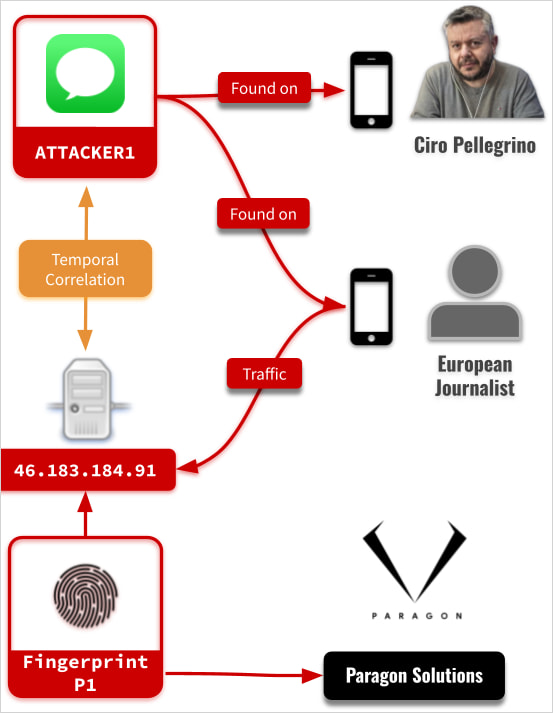
According to the analysis of Citizen Lab, the delivery vector of graphite was IMessage. The attacker used an account, which was labeled ‘attacker 1’ in research, to send specially prepared messages that exploited CVE-2015-43200 for remote code execution.
It achieved delivery of spyware without any conversation with the target, called zero-click attack, and without producing any visible signals to alert the victim.
Once active, spyware contacts a command-end-control (C2) server to obtain further instructions. In the case confirmed by Citizen Lab, the infected phone is linked to HTTPS: //46.183.184 (.) 91, a VPS that is associated with the infrastructure of Paragon.
This IP address was hosted on Edes Global and was minimal active till 12 April.
Source: Citizen
Although a slight trace was left on the equipment, the citizen lab was able to recover some logs with high confidence with sufficient evidence to characterize attacks for paragon graphite spyware with high confidence.
Earlier this year, the same spyware family “caught” was exploited a zero-day vulnerability in WhatsApp in another zero-click attack which targeted other Italian victims.
Italian officers have Confirmed earlier this month Several attacks against individuals in the country, in which journalist Francesco cancelato and activist Luka Casserini and Dr. Gusepp “Beppe” Cassia. However, parties responsible for those attacks are not publicly known.



