
Actor is actively exploiting the WordPress theme ‘Alone’ to achieve a remote code execution and acquire a full site.
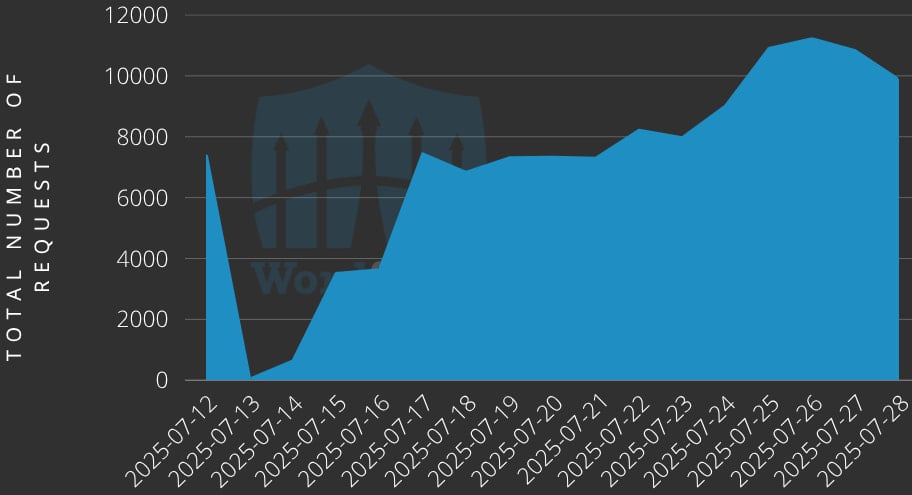
Wordfense is reporting malicious activity, saying that it has blocked more than 120,000 exploitation efforts to target its customers.
WordPress Security Firm also reports that the attacks began several days before the public disclosure of the attack defect, indicating that the actor of the danger is monitoring Changelogs and Patch to search for trivials before the website is sent an alert.
The vulnerability tracked under the CVE-2025-5394 affects all versions up to 7.8.3 alone. The seller, Bearsthemes, fixed it alone in version 7.8.5, released on 16 June, 2025.
The problem stems from the theme ‘alone_mport_pack_install_plugin ()’ function, which lacks non -checked and is exposed through WP_ajax_nopriv_ hook.
The function allows plugin installation through AJAX, and a distant source in post data admits the URL, allowing uncontrolled users to trigger plugin installation from distance URL.
According to Wordfense, the attackers take advantage of the defect for uploading the webshal inside the zip archives, deploy the password-protected PHP backdoor that allow constant remote command execution through HTTP requests, or make hidden administrator users.
In some cases, the attackers also install a full-convenient file manager that gives them complete control over the database of the site.
Given the above, signs of compromise include the presence of new administrator users, suspected zip/plugin folders, and ‘administrator- Ajax.php? Action = Request of ‘alone_Mport_Pack_Install_Plign’. ,
Wordfhens made thousands of exploitation efforts from IP address to 193.84.71.244, 87.120.92.24, 146.19.213.18, and 2A0B: 4141: 820: 820: 752 :: 2, so they must be blocked immediately.
Source: Wordfense
Is almost a premium theme alone 10,000 sales on Envato marketMainly used by non-profit such as charity, NGOs, money raising organizations and social organizations.
Although WordFense presented a report to Bearsthemes in early May 30, 2025, he did not hear back, he carried forward the issue for the Envato team on 12 June.
Four days later, the seller released a certain version of the V7.8.5 alone, which is the recommended update target for all users.
Last month, another premium WordPress theme, motors were targeted by hackers, who exploited a user verification defect to hijack the administrator’s accounts on weak websites.



