
Threat actors are exploiting a zero-day vulnerability (CVE-2025-11371) in Gladinet CenterStack and Triofox products, which allows a local attacker to access system files without authentication.
At least three companies have been targeted so far. Although no patch is available yet, customers can apply mitigations.
CenterStack and Triofox are Gladinet’s commercial solutions for file sharing and remote access that allow the company’s own storage to be used as a cloud. According to the vendor, Centerstack is used by “thousands of businesses in more than 49 countries.”
No fix, all versions affected
The zero-day vulnerability CVE-2025-11371 is a local file inclusion (LFI) flaw that affects the default installation and configuration of both products, affecting all versions including the latest release, 16.7.10368.56560.
Researchers at managed cybersecurity platform Huntress discovered the security issue on September 27 when a threat actor successfully exploited it to obtain machine keys and remotely execute code.
A closer analysis revealed that the problem was caused by LFI being leveraged to read Web.config and extract the machine key. This allowed the attacker to exploit an old deserialization vulnerability (CVE-2025-30406) and achieve remote code execution (RCE). viewstate,
The CVE-2025-30406 deserialization bug in CenterStack and Trifox was also wildly exploited in March, and was caused by a hardcoded machine key. An attacker knowing the key can execute RCE on the affected system.
“After subsequent analysis, Huntress discovered the exploitation of an unauthenticated local file inclusion vulnerability (CVE-2025-11371) that allowed a threat actor to retrieve machine keys from the application Web.config file to perform remote code execution via the above viewstate deserialization vulnerability” – huntress
Huntress contacts Gladinate to inform him of the discovery. The vendor confirmed that it was aware of the vulnerability and said it was in the process of notifying customers about the workaround until a patch is available.
The researchers shared the mitigation with the targeted customer and published the following recommendations to protect against CVE-2025-11371:
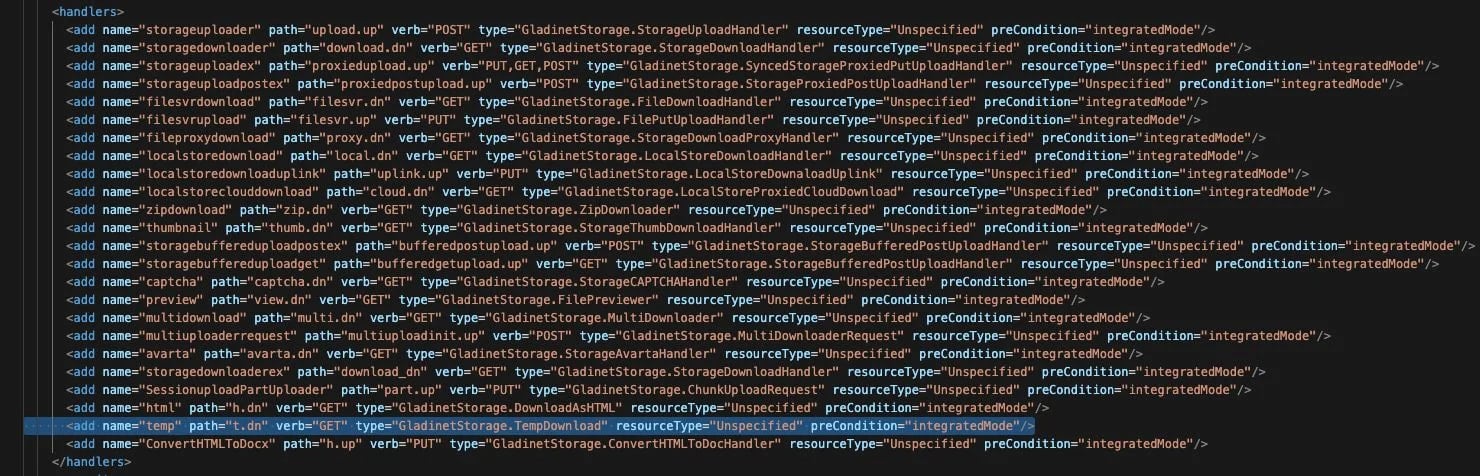
- Disable the temporary handler in the Web.config file for the UploadDownloadProxy component at “C:\Program Files (x86)\Gladinet Cloud Enterprise\UploadDownloadProxy\Web.config”
- Locate and delete the line that defines the temp handler – it points to t.dn
Source: Shirika
This line enables vulnerable functionality that attackers exploit via local file inclusion, so removing it could prevent the exploitation of CVE-2025-11371.
The researchers warn that the mitigation “will impact some functionality of the platform”, but ensure that the vulnerability cannot be exploited.



