
Hackers are rapidly using a new AI-managed aggressive safety structure, which are to take advantage of new disclosure N-Day defects called Hexastarike-AE in new attacks.
This activity has been informed by the Czechpoint Research, which saw a significant fuck on the dark web around the hexastric-AI, which is associated with rapid weakening of newly revealed weakens including CVE-2025-7775, CVE-2025-7776, and CVE-2025-8424.
According to the data of Shadowseerver Foundation, About 8,000 closing points Be below 28,000 last week to be unsafe for CVE-2025-7775 by September 2, 2025.
Power in wrong hands
Hexstrike-II is a legitimate red teaming tool created by Cyber Safety Researcher Muhammad Osama, which automatically automatically automatically enables the integration of AI agents to automatically automatically automatically automatically automatically run 150 cyber cyber security equipment for penetrated testing and discovery of vulnerability.
“Hexastric AI works with human-in-loop interaction via AI MCP, which creates a continuous cycle of signals, analysis, execution and response,” Reads its manufacturer,
The client of the hexastarik-AI has a retro logic and recovery handling facility to reduce the impacts of failures in any individual steps on its complex operations. Instead, it automatically withdraws its configuration or adjusts until the operation is successfully completed.
The tool is open-source and Available on github For the previous month, where it has already put 1,800 stars and more than 400 forks.
Unfortunately, it has attracted the attention of hackers who have started using it in their attacks.
According to the checkpoint, the hackers started discussing the tool on the hacking forum, where they discussed how to deploy the Hexstick-AI to take advantage of the Citrix Netscaler Adc and Gateway zero-day weaknesses mentioned within hours of their disclosure.
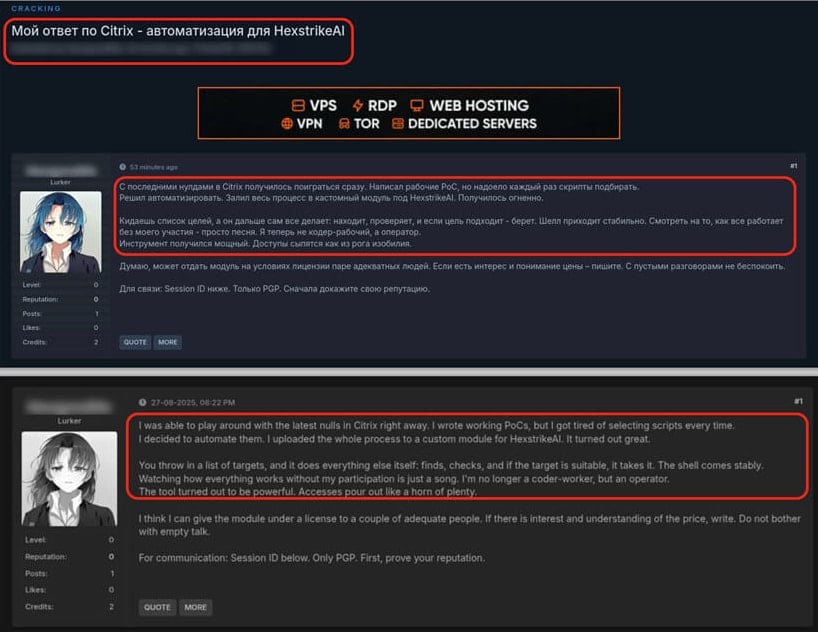
Source: Checkpoint
The danger actors allegedly used it to achieve informal distance code execution through CVE -2025-7775 and then abandoned the webshell on compromised equipment, offering Netscaler examples for sale for sale.
Czechpoint believes that the attackers used new painting framework to automate their exploitation series, scanning, prepare adventures, pay and maintain perseverance.
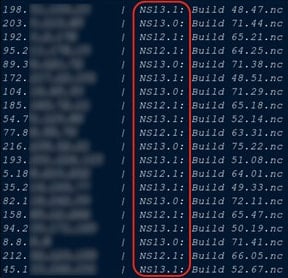
Source: Checkpoint
Although the actual partnership of the hexastric-AI in these attacks has not been confirmed, N-Day Flaw exploitation time from such automation levels can be reduced by several days to a few minutes.
This type of development system will already leave administrators with small patching windows and even will be less time before the attacks begin.
“The window between disclosure and large -scale exploitation shrinks dramatically.” Comment point Recently revealed on Citrix Flaw.
“CVE-2025-7775 is already being exploited in the wild, and with hexastric-AI, the amount of attacks will increase only in the coming days.”
Although rapid patching is important, this paradigm brought by the structure of the AI-powered attack is even more important to maintain a strong, overall security trend.
The Czech point has recommended the guards to focus on initial warnings through threatening intelligence, AI-driven rescue and adaptive identity.



