
A danger actor has been tracked as ‘Hausi Hawk’, which has been abandoned cloud services, leaving cloud services, which has been left to distribute scams, fake apps and malicious advertisements about reliable sub -domains of governments, universities and fate 500 companies.
As Infoblox researcherThe Hagy Hawk CNAME scans first to the domain with a record, which is left out of cloud andpoints, which they determine through passive DNS data verification.
Subsequently, they register a new cloud resource with the same name that occurs as one in the abandoned CNAME, inspiring the subdoman of the original domain to solve the new cloud-host site of the actor with danger.
Using this technique, the danger actors kidnapped several domains to host malicious activities, host scam content, or used them as a redirect hub to operate the scam.
Some notable examples of the kidnapped domain include:
- Cdc.gov – U.S. Centers for Disease Control and Prevention
- honeywell.com – multinational conglomerate
- Burkeley. Du – University of California, Berkeley
- Michelin.co.uk – Michelin Tire UK
- Ey.com, pwc.com, deloitte.com – Global “Big Four” consulting firm
- ted.com – Famous non -profit media organization (TED talks)
- health.gov.au – Australian Health Department
- Unicef.org – Funds of United Nations Children
- nyu.edu – New York University
- Unilever.com – Global Consumer Goods Company
- ca.gov – California State Government
The complete list of compromised domains can be seen in the Infoblox report.
Once the actor receives control over a subdomain, they produce hundreds of malicious URLs below it, which appear valid in the search engine due to the high trust score of the original domain.
The victims clicking on the URL are redirected through layers of domains and TDS infrastructure that profile them to qualify the victims based on their devices, IP addresses, VPN uses, etc.
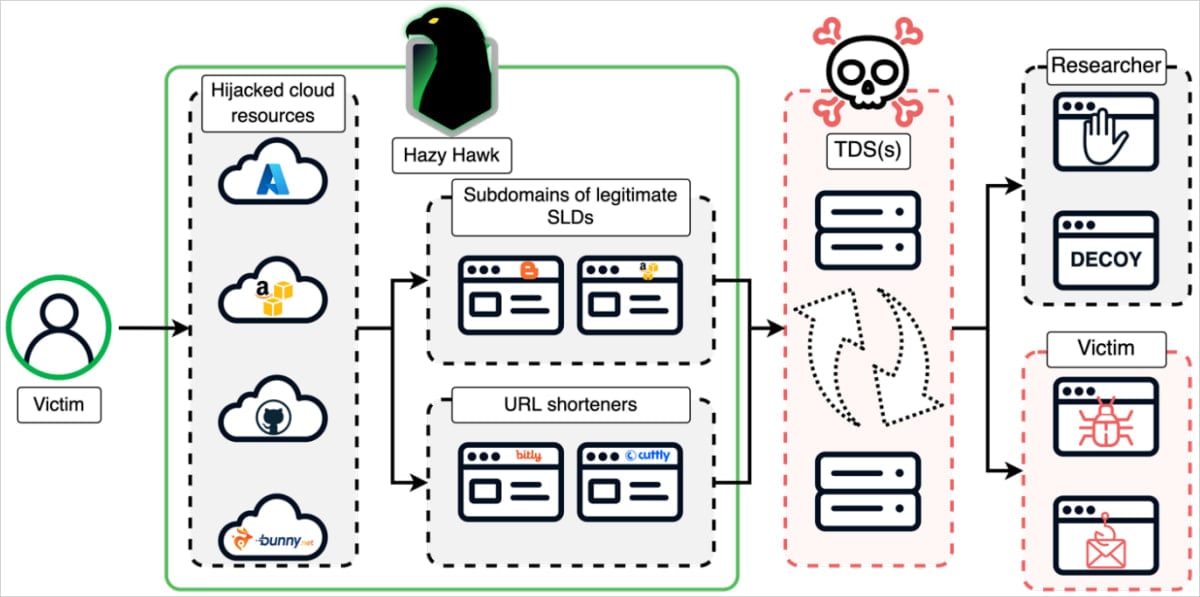
Source: Infoblox
Infoblox reports stated that sites are used for tech support scams, fake antivirus alerts, fake streaming/porn sites and fishing pages.
Users cheated to allow browser push notifications, as they continuously receive alerts even after leaving scam sites, which can generate significant revenue for Hawk Hawk.
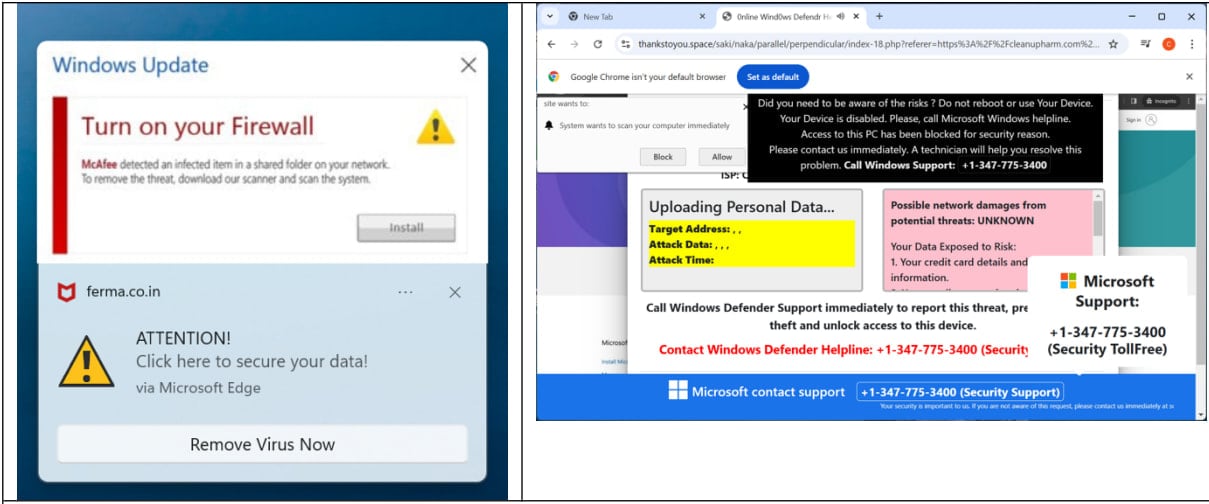
Source: Infoblox
The same researchers earlier explained another danger actor, ‘Savi Sehors’, who also misused CNAME records, which was done to build an etipical TDS, who re -resurrected users to fake investment platforms.
CNAME records are easy to ignore, so they are prone to misbehaving secretly, and it appears that the increasing number of danger in danger makes actors realize it and attempts to take advantage.
In the case of Hausi Hawk, the success of the operation also depends on organizations that fail to remove the DNS record after decreasing cloud services, which allows the attackers to repeat the original resource name without authentication.



