
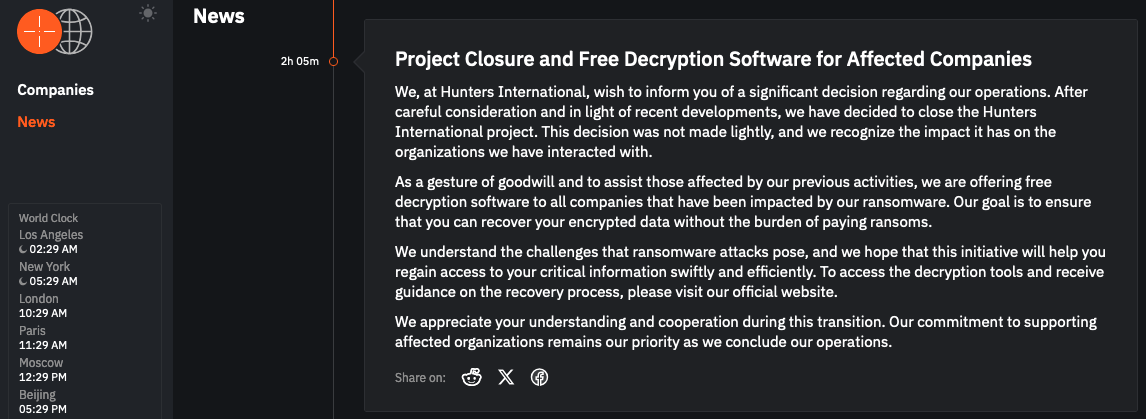
The Hunters International Rainsmware-e-Service (RAAS) today announced that it had officially shut down its operations and would offer free decripters to help the victims recover their data without ransom.
In a statement published on its dark web leakage, a cybercrime gang said, “In the light of carefully considering and recent developments, we have decided to shut down the Hunters International Project. This decision was not made lightly, and we affect the organizations with which we have interacted with.”
“As a gesture of goodwill and to assist people affected by our previous activities, we are offering free decryption software to all companies that are affected by our ransomware. Our goal is to ensure that you can restore your encrypted data without the burden of ransom.”
The danger actors also removed all entries from the Extortion portal and said that companies that were encrypted into Hunteers International Rainmware attacks could request a decrying tool and recovery guidance on the official website of the gang.
While the ransomware group does not suggest that the “recent developments” suggests that today’s announcement follows a statement of 17 November, stating that Hunters International will soon be closed due to increase in law enforcement investigation and decline in profitability.
Threat Intelligence firm Group-Ib also revealed in April that Hunteers was rebranding with a plan to focus on international data theft and forced recovery-recovery, and started a new forcible recovery-revolving operation known as “World Leaks”.
“Unlike Hunters International, which combines encryption with forced recovery, the World Leaks operates as a forced recovery-revolving group using a custom-made exfering tool,” Group-IB said at that time, saying that the new tool storing software exhibitions appears to be an advanced version of the tool. Is done from ransomavar.
Hunters emerged at the end of International 2023 and sent as a possible rebrand of the high due to the code equality by security researchers and ransomware experts. The ransomware group’s malware targets a wide range of platforms including Windows, Linux, FreeBSD, Sunos and ESXI (VMware Server), and it also comes with support for X64, X86 and ARM architecture.
In the last two years, Hunters International has targeted companies of all sizes, demanding ransom ranging from hundreds of thousands to millions of dollars, based on the size of an organization violated.
The Rainmware Gang has claimed responsibility for around 300 attacks worldwide, which is one of the most active ransomware operations in recent years.
Notable victims claimed by Hunters International include US martial service, Japanese optics giants Hoya, Tata Technologies, North American Automobile Dealership Autochada, US Navy Contractor Austral USA, and Integris Health, Oklahoma.
In December 2024, Hunters International also hacked the Fred Hutch Cancer Center, threatening to leak the stolen data of more than 800,000 cancer patients, if they were not paid.



