Even though people often think that Mac is safe from malware, it is definitely not true. In the case, a new atomic theft campaign, which is being used to infect the best MacBook and other Apple computers with information-dictation malware, has been observed online.
As reported Hacker newsThe campaign was discovered by Cyber Security firm Claudsac and is believed to have the work of Russian hackers due to comments in the source code of malware.
This campaign makes this campaign particularly interesting, this is the fact that in addition to typtosting, it also uses social engineering to unheard the Mac users to fall for it. For those unfamiliar people, typosketing is a type of attack, where cyber criminals register a look domain to laying nets for potential victims, incorrectly incorrect the URL of a popular site in the address bar of their browser. Although they may think that they are on the website of a popular company, instead, they are actually on a fake site designed to mimic the real, which is also used to spread dangerous malware.
Once the atom is infected with the theft, the malware can steal personal and sensitive data from your Mac such as your Apple kitchen, browser cookies, login credentials, credits, credit card details and more stored passwords.
You need to know about some tips and tricks about this new malware campaign, so that you can prevent it from falling prey to other cyber attacks.
Not the spectrum you were looking for
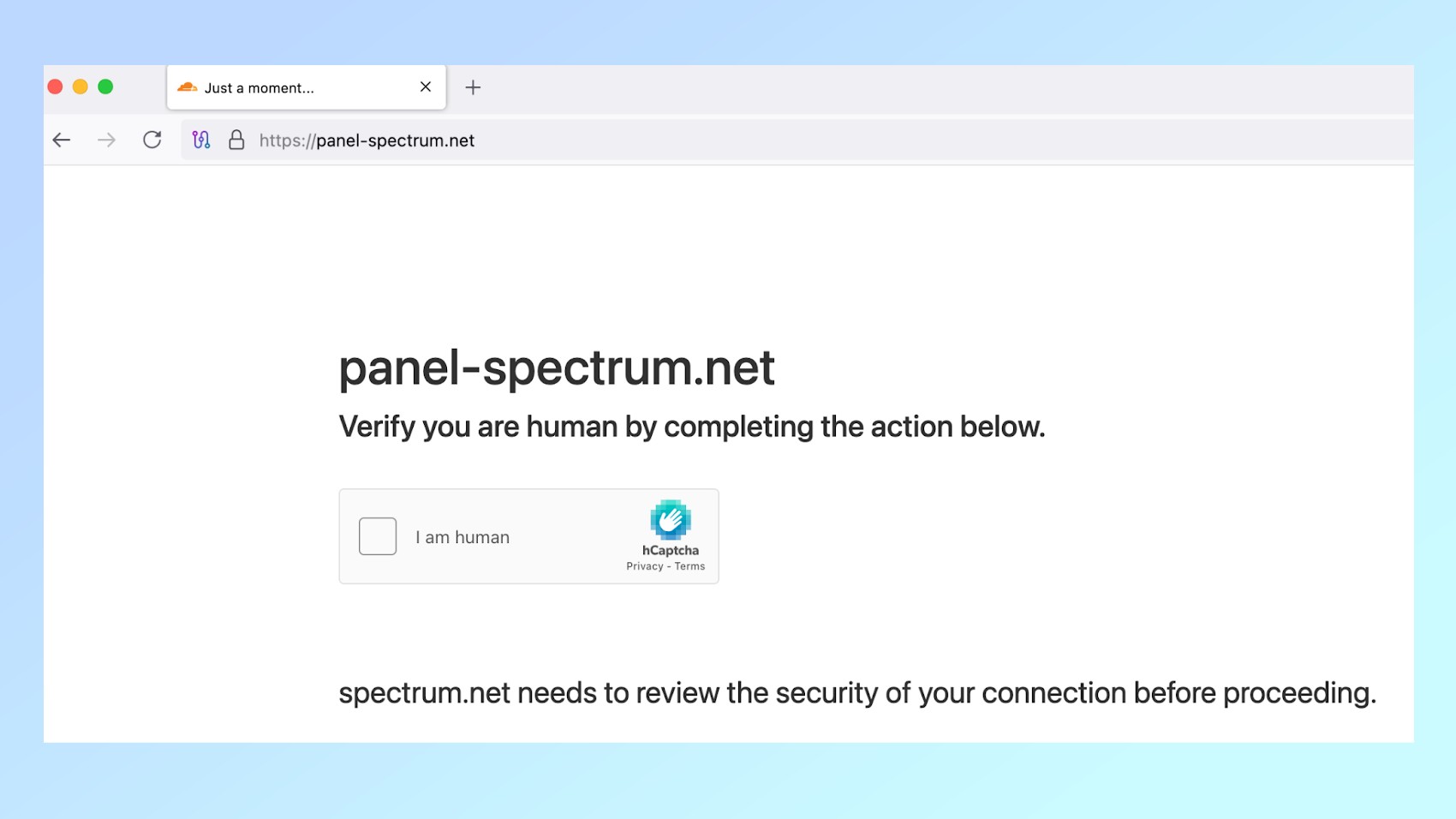
According to Claudsac, the hackers behind this new campaign are implementing American Internet and cable provider spectrum using many different fake sites. While the official website of the spectrum can be seen in the spectrum (.) Com blog postThe firm highlights one of these fake sites that uses the URL panel-spectrum (.) Net.
Once on this fake site, potential victims are asked to complete a recaptcha to verify that they are not bots. Since many sites use the same forms of this or similar verification, many people cannot think twice when they are said to check a box that they are human. However, on the fake site shared by Claudsac, once the verification fails, potential victims are asked to complete an alternative verification instead.
However, when a “optional verification” clicks on the reading button, a command is copied on their clipboard without their knowledge. A set of instructions appears that asks them to open a command prompt, paste the code that was copied on their clipboard and to hit the “Enter” to run on Windows. If someone is using Mac, slightly different instructions are shown that lead for the same result, they are getting infected with the malware that informs the computer.
On Mac, a malicious shell script is used to steal the system password and download a version of the nuclear stealing malware. As in Cloudsek security researcher Kouoshik Pal Company reports, the script uses the native MACOS command, which is commanded to bypass the safety mechanisms, bypassing the safety and perform malicious binergies. “
How to be safe from Mac Malware

Given that hackers use all types of different tricks to take potential victims to fake sites spreading malware, always typing the company’s website manually in their browser’s address bar. However, you should also check that you have written it correctly.
If you do not know the official site of a company, you can use a search engine to find it. One thing you want to be careful about that you are not clicking on the first link you see. The reason for this is that on Google and other search engines, links on top are often advertising, while it is often necessary to find the company’s actual website that you scroll a little more under the page. The problem with clicking an advertising or sponsored search results is that cyber criminals often use malicious advertisements to take users to fake sites rather than a company’s actual site, as anyone (even hackers) can buy advertising space online.
From here, it is a matter of knowing how to identify a clickfix attack. Many sites asks that you complete a recurrence or other form of verification before entering. However, if a site asks you to open the command window and paste something from your clipboard before hitting “enter”, it is a major red flag. A legitimate company can ask you to choose all images that are cars, but they will never copy the code on your clipboard without your knowledge and then ask you to paste and run it elsewhere.
Although your Mac Apple comes with the underlying safety software as your xprotect, it is still a good idea to consider investing in one of the best Mac Antivirus software solutions. Unlike free antivirus software, these paid options are updated more often and are more likely to be spotted and helps you avoid new malware strains such as atoms stolen.
Given that attacks using this clickfix technique have proved both successful and profitable for hackers and other cyber criminals, they are not going anywhere soon. This is why it makes sense to educate yourself and your family members about such dangers so that you can see any red flag before getting infected with your Mac or PC with malware.


