
Building automation giant Johnson Control is informing individuals whose data was stolen on a large -scale ransomware attack, which affected the company’s operations worldwide in September 2023.
Johnson Control is a multinational group that develops and produces industrial control systems, safety equipment, HVAC systems and fire security equipment for buildings. The company employs more than 100,000 people through its corporate operations and subsidiaries in 150 countries, reporting $ 27.4 billion in 2024.
As Bleepingcomputer first reported, Johnson Controls was killed by a ransomware attack in September 2023, in February 2023 after the company’s Asian offices violations and its network later after the lateral movement.
“Based on our investigation, we determined that an unauthorized actor accessed some Johnson Control System from 1 February 2023 to September 30, 2023 and inquired from those systems,” the company They say In the data breech notification letters, the data breeted with the Attorney General of California, what information was stolen in the attack, was re -prepared to hide it.
“After being aware of the incident, we ended the reach of the unauthorized actor for the affected systems. In addition, we attached the third-party cybercity experts to further investigate and solve the incident.
The cyber attack forced Johnson to close a large part of his IT infrastructure, as the danger actors encrypted several devices, which affected the system around the world and the customer-supporting systems.
Johnson Controls confirmed in the SEC filing in January 2024 that Cyberlack was orchestrated by a ransomware gang, stoleing documents from the system of compromised during the breech.
While the firm did not characterize the incident for a specific ransomware operation, the attack was linked to the Dark Angels ransomware group based on a sample of a VMware ESXI encrypter posted during the breech, stating that it was used against Johnson control.
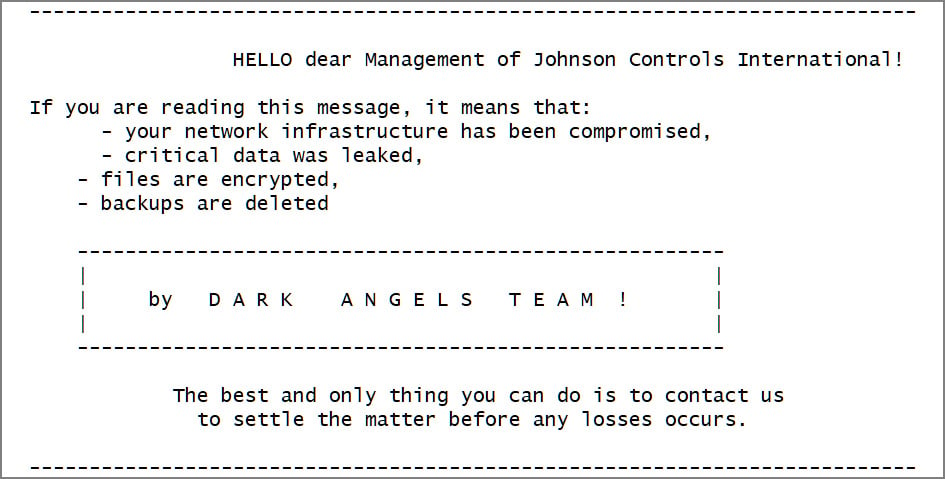
Bleepingcomputer was also reported that the ransom note was associated with a dialogue chat, where the Rainmware Gang demanded $ 51 million for the decryptor and to remove the stolen data from Johnson Controls Network.
The ransomware operators also encrypted the company’s VMware ESXI virtual machines during the attack and claimed that more than 27 TB of documents with corporate data have been claimed.
At that time, the company had said that the expenses related to the reaction of the incident and treatment had already reached $ 27 million, but also mentioned that it is expected that the amount would increase as the efforts of investigation and treatment have increased.
Dark Angels, Johnson Control’s 2023 Breach, the ransomware operation, surfaced in May 2022, when he began to target organizations worldwide in double expansion attacks. In these attacks, the group steals sensitive data and uses it for pressure under the risk of publishing victims online on their dark web leak site, called Dangle Leak.
They also deploy ransomware to encrypt all equipment on the network after achieving access to Windows Domain Controller, using Windows and VMware ESXI Encripters based on leaked babbbook ransomware source code.
However, Cyber Safety Researcher Malware Hethtem told Bleepingcomputer that the Linux Encripter used in Johnson Controls Attack was similar to others used by the raganar locker ransomware since 2021.



