Last week, Krebsanusurity collided with a near-record distributed Daniel-Off-Service (DDOS) attack, which is more than 6.3 terabits per second data (a trillion bits of a terabit data). A brief attack appears to run a test for a large -scale new Internet of Things (IOT) botnets that are capable of starting the handicapped digital attacks that can withstand some web destinations. Read for more information about botnette, attack and clear manufacturer of this global danger.

For reference, the attack of 6.3 TBPS last week was ten times the attack size against this site in 2016. Mirai Iot Botnet, which was krebsonsecurity offline for about four days. 2016 attack was so big Akamai -The Pro-Bono DDOs for Krebsonsecurity at that time were providing me to give up their service because the attack was causing problems for their paying customers.
Since Mirai Attack, Krebsonsecurity.com has been behind the conservation Project shieldA free ddos defense service Google Assistant Ara News offers websites offering material related to human rights and election. Google Security Engineer Damian Menscher The May 12 attack Krebsonsecurity reported that the largest Google has ever handled it. In terms of sheer size, it is only another for one uniform attack Cloudflare Mitigation and Wrote in April,
After comparing the notes with Cloudflare, Menscher said that the botnet launched both the attacks tolerated the fingerprints IsuruA digital siege machine that was revealed less than a year ago. Menscher said that the attack on Krebsnsurity lasted for less than a minute Big UDP data packet At random ports About 585 million data packets per second,
“This was usually an attack designed to overwhelm the network link,” said Menses’, referring to various internet service providers (ISPs) and in the middle. “For most companies, this size of the attack will kill them.”
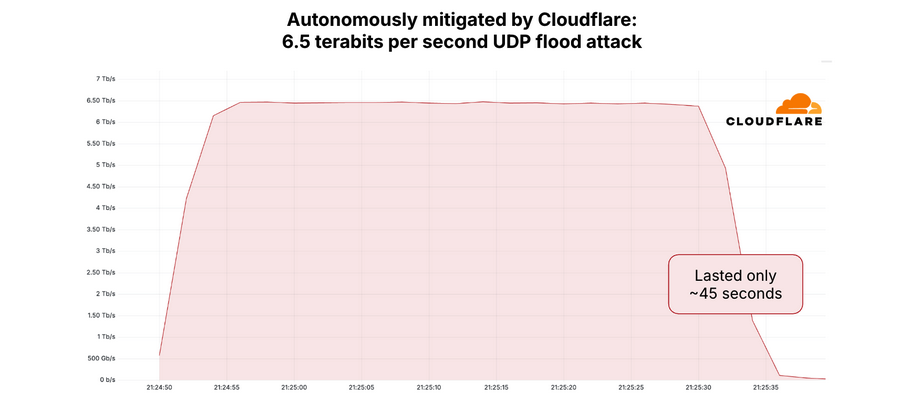
A graph depicting the 6.5 TBPS attack reduced by Cloudflare in April 2025. Image: Cloudflare.
The AISURU BOTNET includes a global spread collection of Iot devices hacked, including a router, digital video recorder, and other systems that are made commanders through default passwords or software weaknesses. As Document By researchers on Qianxin XlabBotnett was first identified in the August 2024 attack on a large gaming platform.
Aisuru allegedly became silent after that exposure, only in November to reopen with more firepower and software exploits. One in January 2025 reportXlab got a new and better Aisuruu (aka “Airashi“) The cambium network cnpilot router included an unknown zero-day vulnerability in the CNPILOT router.
Not all around
People behind Aisuru Botnet are publicly reaching their DDOS machine Wire Chat channels that closely monitor by many safety firms. In August 2024, Botnett was rented in membership tier, which ranged from $ 150 to $ 600 per week per day, offering attacks up to two terabites per second.
In August 2024, read a notice posted on Telegram by Aisuru Botet owners, “You cannot attack any measurement walls, health facilities, schools or government sites.”
Interested parties were asked to contact the Telegram handle “@yfork“To buy a subscription. Account @yfork used the first surname”Bounce“An identity that has been posting on public DDOS-focused telegram channels since 2021.
According to the FBI, the DDOS for-Hare Domain of Furki has been seized in several law enforcement operations over the years. Last year, Furki said that he was selling domains on Telegram StressiveWhich saw the FBI in 2022 as part of an ongoing international law enforcement attempt by the FBI, aimed at reducing and demanding the supply of DDOS for-Hire services.
“The operator of this service, who calls himself ‘firk’, operates a telegram channel to advertise facilities and communicate with the current and potential DDOS customers,” reads an FBI seizure warrant (PDF) released for Stressor (.). The FBI Warrant said that when the recovery was announced on the same day, Furki posted a link to a story on this blog, adding the comment to the domain seizure operation, adding the comment, “We are buying our new domain right now.”
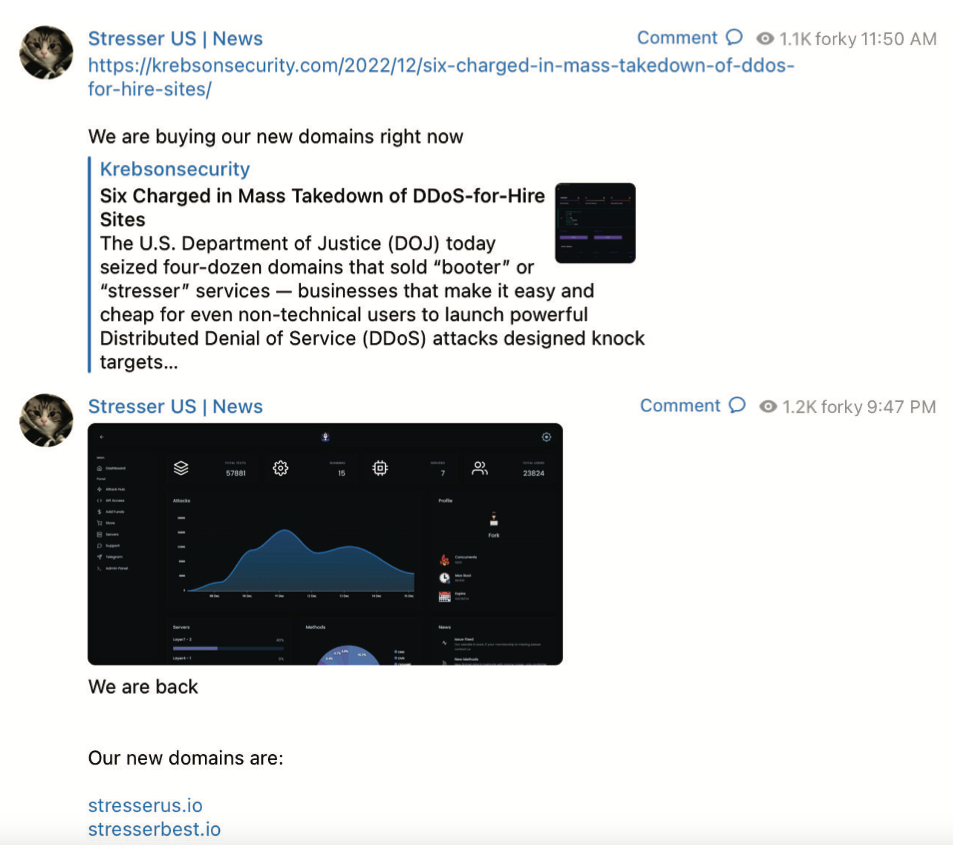
A screenshot from FBI’s seizure warrant for FBI’s DDOS-For-Hire-Hire Domain shows forky, announcing the revival of its service in the new domain.
About ten hours later, Furki posted again, including the stresser (.) The best user also includes a screenshot of dashboard, directing customers to use their saved passwords for the old website on the new website.
Review of firkery posts for public telegram channels – as indexed by cyber intelligence firms Unit 221B And Flash point -A 21 -year -old man reveals a person who claims to live in Brazil (full disclosure: Flashpoint is currently an advertiser on this blog).
Since the late 2022, the posts of Furki have often promoted a DDOS mitigation company and ISP which it operates Botshield (.) IOThe Botshield website is connected to a commercial unit registered in the United Kingdom Botshield limitedWhich lists a 21 -year -old woman from Sao Paulo, Brazil as a director. Internet routing records indicate botshields (As213613) Currently controls several hundred internet addresses allotted to the company earlier this year.
Domantools.com Reports states that Botshield (.) IO was registered in July 2022 Kaik Soutier Light In Sao Paulo. A LinkedIn Profile The same name states that this person is a Brazilian network specialist, who focuses on safety, DDOS mitigation, collection and cloud server services, “works in the plan and implementation of strong network infrastructure.”
Meet

Picture: Jacqueline Varas / Shutterstock.com
In his post of public telegram chat channels, Fourki has hardly tried to hide his hideout or identity. In countless chat conversations, averted by Unit 221B, Furki can be seen talking about everyday life in Brazil, often commenting on very low or high prices in Brazil, ranging from computer and networking gear to drugs and many goods.
Arriving through Telegram, Fourky claimed that he was “not involved in such illegal work, now,” and the project was taken by other unspecified developers. Forky initially told krebsonsecurity that he had been out of the Boteta view for years, only to accept that from the end of last year was presented with public positions on Telegram, which was clearly shown otherwise.
Forky refused to involve the attack on Krebssncree, but admitted that he helped the Aceuru botnet to develop and marketing. Forky claims that he is now only one staff member for the AISURU BOTNET team, and he stopped running the botnet two months ago after starting a family. Forekey also said that the woman named as the director of Botshield belongs to her.
Forky offered equal, evasive reactions for many questions about Aisuru Botnet and his business efforts. But at one point that crystal was clear:
“I have zero fear about you, FBI, or Interpol,” Fourki said, saying that it now focuses almost completely on his hosting business – Botshield.
Forky refused to discuss its ISP customer’s makeup, or to clarify whether the boatshield was more than a hosting provider or DDOS mitigation firm. However, Forky has posted about Botshield on Telegram, which is successfully reducing large DDOs attacks launched against other DDOS-For-HIRE services.
The registration for the domantols botshield (.) The same Sau Paulo Street addresses in the records records. IO was used to register many other domains, including Khichdi language-saving (.) Us. The email address in the WHOIS records for that domain is forkcontato@gmail.com, which it says that it was now used to register the domain for DDOS-Hire Service. Stress (.) UsOne of the domains seized in the 2023 cracks of the FBI.
On 8 May, 2023, US justice department Announced With a dozen other domains offering DDOS services, the stresser (.) We, seizure. DOJ said that ten out of 13 domain services were rebirth which were seized during one Pre -sweep in DecemberWhich targeted 48 top stress services (also known as “bookers”).
Furki claimed that he could find out that my site was attacked with the isuru. But when the question was pressed a day later, Fourki said that it would come empty handed.
An interview on Telegram states, “I tried to ask around, not all the big people are enough to attack you.” “I had nothing to do with it. But welcome to write the story and try to blame me.”
Mirai’s ghost
The 6.3 TBPS attack last week did not disintegrate this site, as it was so brief – lasting about 45 seconds. The DDOS attacks of such magnitude and brevity usually arise when botnet operators want to test or perform their firepower to the benefits of potential buyers. In fact, Google’s Menses said that it is likely that the May 12 attack and a slightly larger 6.5 TBPS attack against Claudflair last month were both testing of the capabilities of the same botet.
In many ways, the danger generated by Iceuru/Aeri Botnet is reminiscent of Mirai, an innovative Iot malware strain that emerged in the summer of 2016 and successfully eliminated almost all IOT malware strains in the existence.
As the first was revealed by Krebssnasurity in January 2017, Mirai author was two American men who co-ranked a DDOS mitigation service-even that they were selling more attractive DDOS for-Hire Services using the most powerful boatnet on the planet.
After less than a week after Mirai Botnet used Krebsnsurity in a day -long DDOS, Mirai authors published the source code on their botnet so that they would not be in possession of their arrest by federal investigators.
Ironically, the leak of Mirai source is fine, inspired by the final unmasosing and arrest of Mirai authors, who went to serve probation sentences They need to consult with FBI investigators on DDOS checkBut that leak also rapidly produced dozens of Mirai Botett clones, many of which were exploited to fuel their own powerful DDOS-Hare Services.
Mensester told Krebsnasurity that as it may seem, as a counterbile, the Internet as a whole would be better if the source code for the asseru became a public knowledge. Finally, he said, the people behind Aisuru are in constant competition with other IOT Botton Operators, who are all striving to command a finite number of weakened IOT devices globally.
Such growth would definitely cause the spread of the Asuru Boteton clone, he said, but at least each individual botnett will reduce the overall shelling from each individual botet – or at least at least within the range of mitigation capabilities of DDOS security providers.
Preventing a source code leaks, Menses’ said, it would be good if someone published a complete list of software adventures, which are being used by Esuru operators so that they can develop their botten so quickly.
“The reason for this Mirai was so dangerous that it effectively poured out the botnets with competition,” he said. “This attack somehow managed to compromise all these boxes, which no one else knows. Ideally, we want to see the fragmented, so that no one (individual botet operator) controls too much.”


