
The lockbit ransomware gang has faced a data breech when its dark web affiliate panels were upset and replaced with a message connected to a MySQL database dump.
All administrator panels of the ransomware gang are now in the state. “Don’t commit crime Crime is bad Xoxo from Prague, “to download a” paneldb_dump.zip with a link. ,
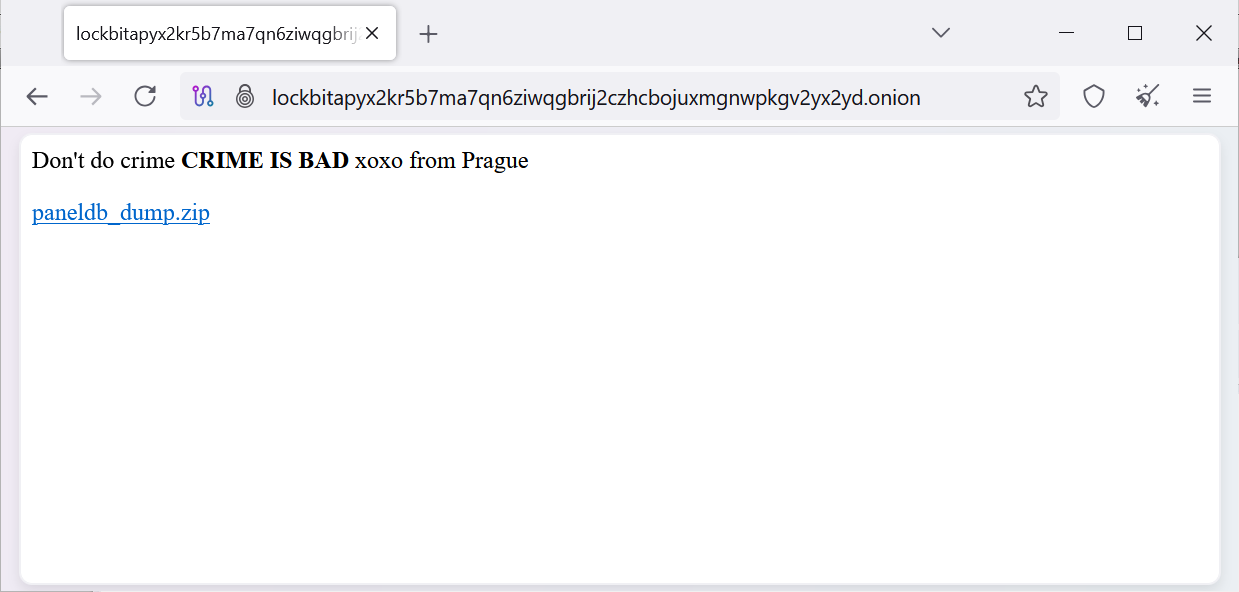
As First -minded Threatened by the actor, Ray, this collection has a SQL file dumped from the MySQL database of the site affiliated panel.
By analyzing by bleepingcomputer, there are twenty tables in this database, including something more interesting, including:
- A ‘Btc_addresses‘Table with 59,975 unique bitcoin addresses.
- A ‘Create‘There are individual buildings created by colleagues for the table attacks. Table rows have a public key, but no private key, unfortunately. The names of targeted companies are also listed for some buildings.
- A ‘Builds_ConfigationThe table consists of separate configurations used for each build, such as leaving the ESXI server or encrypting the files.
- A ‘Chat‘Table is very interesting as it includes ransomware operations from 19 December to 29 April and 4,442 dialogue messages between the victims.
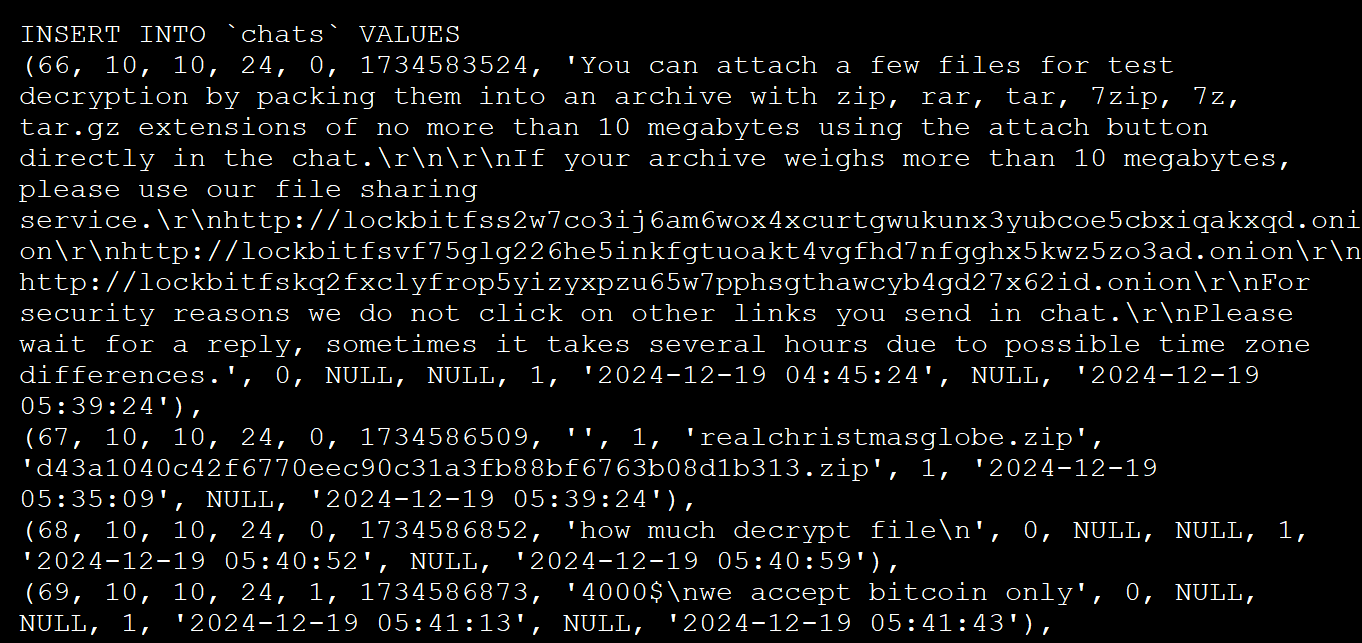
Allied panel ‘chat’ table - A ‘UsersThe table listed 75 administrators and colleagues, who had access to the affiliated panel Michael Gilespie That password was stored in placentch. Some of the plaintext passwords are examples’ Weekendalver 69, ‘Movingbricks 69420’, and ‘Lockbitpraude 231’.
One in Tox interaction with rayThe lockbit operator is known as ‘lockbitsup’, stated that no private key was leaks or data was lost.
Based on the last date record in the MySQL dump generation time and dialogue chat table, the database appears to be dumped at some point on 29 April 2025.
It is not clear who did Brech and how it was done, but the exclusion message matches a potential link used in the recent violations of the dark web site of Everest Rainmware, suggesting a potential link.
In addition, the PHPMYADMIN SQL dump suggests that the server was running PHP 8.1.2, which is unsafe for important and actively exploited vulnerabilities tracked as CVE-2024-4577, which can be used to achieve distance code performance on the server.
In 2024, a law enforcement operation called Operation Cronos took down the infrastructure of the lockbit, including 34 servers hosting the data leak website and its mirrors, stolen data from the victims, Cryptocurrency addresses, 1,000 diagram keys and comfortable panels.
Although the latest violation gives another blow to its already damaged reputation after the lockbit takedown, to resume and resume operations.
It is very early to mention whether this additional reputation will be the last nail in the coffin for the hit ransomware gang.
Other ransomware groups that have experienced similar leaks include Conty, Black Basta and Everest.



