
Microsoft has announced the new Windows 365 security lapse starting in the second half of 2025 and has affected new provisions and reprovisioned cloud PCs.
The company said that these changes include disabling clipboard, drives, USB, and printer redirections by defaults to users, from copying files between cloud PCs and physical equipment through clipboard functions, to block the risk of data theft and block malware to block the risk of data stolen and block malware.
However, while the USB redirects will be disabled by default, they only target the low-level device access, meaning that USB mice, keyboards and webcams will not be affected as they are managed through high-level redirections. These new security lapses will also be implemented to the newly created host pools for Azure virtual desktop.
Since last month, Microsoft has defaulted on Windows 365 Cloud PC by default by virtue-based security, credential guards, and HyperWizer-Proper Code Integrity (HVCI), which to create Windows 11 Gallery impetus to create Windows 11 Gallery images to create a safe memory, and concentrate colors at the concentration. To stop.
“Windows 365 clipboard, drive, USB, and printer is disabled by default by default and increasing cloud PC protection for all new provisions and reprovisioned cloud PCs,” Microsoft said,
“Since May 2025, all new provisions have been made and reprovisioned Windows 365 Claude PCs are capable of VBS, Credential Guard, and HVCI default forming a Windows 11 Gallery image.”
The notification banner in the Microsoft Intune Admin Center will also display IT administrators about changes and allow them to overridge new omissions if their final-user requires specific rejuvenates.
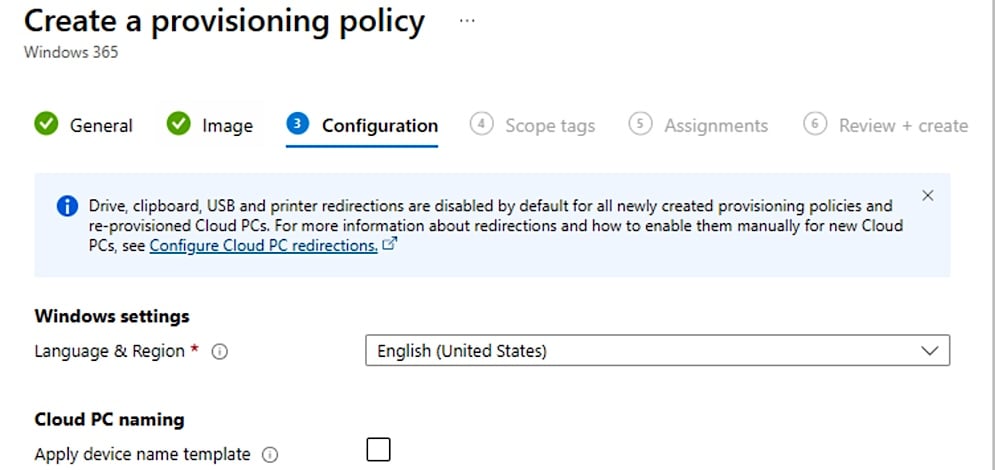
“When the new cloud PC is provided, the new omission will be implemented to disable the redirect,” the company explained. “Next, INTune will sink and enforce the desired settings of the IT administrator from existing policies, override the default configuration. The process assumes that the new cloud PC is being added to an existing group that is assigned to the relevant policy.”
On Tuesday, Microsoft announced that it would begin to update the safety omission for all Microsoft 365 tenants in July, which is to block access through the inherited authentication protocols in the heritage authentication protocols up to Sharepoint, Onedrive and Office Files.
From next month, the Microsoft 365 will automatically block ONEDRIVE and SharePoint using Legacy Browser authentication using RPS (Relying Party suit), along with protocols for office file opening with FPRPC (frontpage remote process call).
Since January, the company has also disabled all Activex controls in the Windows versions of Microsoft 365 and Office 2024 apps and said it will start rolling the convenience of a new teams, designed to block screenshots during Meetingsin July.
Microsoft also announced last week that it would add .library-MS and .Search-MS file types to the list of blocked outlook attachments starting in July.



